What is Portnox Zero Trust Network Access (ZTNA) and how does it work?
In this topic, you will learn about Portnox™ Zero Trust Network Access (ZTNA) and how it provides secure access to SSO web applications and to resources hosted on-premises or in private cloud environments.
Portnox™ Zero Trust Network Access (ZTNA) provides secure access to both public and private resources by enforcing authentication and device validation before allowing any connection. It does not rely on network location or trusted zones. Instead, access is granted after verifying the user’s identity via a certificate and confirming that the device meets defined security requirements using either Portnox AgentP or Microsoft Intune/Jamf.
ZTNA supports two types of resources:
SSO-enabled web resources: Web applications or services that support SSO and are located in a public space, already accessible over the internet, such as a cloud service or a VPN front-end. With ZTNA, access is secured using certificate-based authentication and device validation, which is more secure than typical SSO.
Hosted resources: Applications or services hosted in a private, secured network, such as on-premises or in a private cloud. This support allows users in public or untrusted networks – such as remote employees working from home – to securely access internal applications or services. It replaces traditional VPNs with a simpler, more maintainable alternative.
Note that the technologies used to support these two types of resources are very different, and so the setup process is also very different.
ZTNA for SSO-enabled web applications
In this topic, you will learn how Portnox™ Zero Trust Network Access works together with SSO web applications.
ZTNA provides secure single sign-on user access to web applications that support SSO.
In a traditional single sign-on (SSO) access model, the user can access the web application from any device, as long as the user is authenticated. In the ZTNA model, an extra security condition is added: only specific user devices may access the application, and only if these devices meet the security requirements defined by the administrator.
For example:
-
Traditional security model:
- The user authenticates with the single sign-on provider using their email address and a password (optionally with multi-factor authentication).
- The user can access the web application from any device.
-
The ZTNA model for SSO-enabled web applications:
- The user authenticates with the single sign-on provider using their email address and a password (optionally with multi-factor authentication).
- If the device does not provide risk assessment information (through Portnox AgentP or Intune/Jamf integration), the user cannot access the application.
- If the device does not have the Portnox security certificate (distributed by AgentP or obtained through Intune/Jamf using the SCEP protocol), the user cannot access the application.
- If the user meets the above conditions, but the risk assessment engine (AgentP or Intune/Jamf) discovers that
certain conditions are not met, the administrator may prevent the user from accessing the application. For
example:
- If the device has an outdated version of the operating system
- If the device has no antivirus software installed
- If the user is currently located outside United States
How does ZTNA work with SSO-enabled web applications?
If your web application is integrated with ZTNA through SSO, here is what happens when an example user tries to access the application.
From the user’s point of view, the process is almost identical to the one when the user logs in using single sign-on such as Azure or Google.
-
The user types the address of the web application in their browser to access it, just like they would without ZTNA.
-
The user either clicks or taps on the button to log in using ZTNA or simply enters their email address (this depends on the application).
-
The application automatically redirects the browser to Portnox Cloud, which checks if the user’s device has a Portnox security certificate. If the device is certified, Portnox Cloud redirects the browser to an identity provider such as Microsoft Entra ID, Google Workspace, or other. The identity provider is configured in Portnox Cloud for the specific application.
-
The identity provider handles user authentication. For example, the user may enter their email address and password, provide multi-factor authentication using an authenticator app, or use any other authentication method supported by the identity provider. Once the user is authenticated, the identity provider redirects the browser back to Portnox Cloud.
-
Now that Portnox Cloud knows the application, knows that the device is certified, and knows the logged in user, it communicates with Portnox AgentP installed on the user’s device or the Intune/Jamf agent/engine. It then checks the policies configured in Portnox Cloud or in Intune/Jamf for the application or for a specific group of users. These policies may include operating system versions, installed software, location, and more. Based on these policies, either AgentP or Intune/Jamf decides if the device is safe for application access or not, and sends that information to Portnox Cloud.
-
Portnox Cloud either redirects the user back to the application after a successful login, or informs the user that they cannot be logged in because their device is not safe. Optionally, Portnox Cloud can redirect the user to the company’s support pages, software download pages, or simply display a custom message configured by the administrator.
What do you need to be able to use ZTNA with SSO-enabled web applications?
To be able to use Portnox ZTNA with SSO-enabled web applications, you need to meet the following conditions.
-
You need to have a configured cloud-based authentication repository such as Microsoft Entra Id (Azure Active Directory) or Google Workspace. Portnox Cloud must work together with your authentication repository to know the users accessing your applications.
-
You need to have an identity provider that supports the Security Assertion Markup Language (SAML) protocol or the OpenID Connect (OIDC) protocol. Such identity providers are offered by most authentication repositories (including Entra ID and Google Workspace) but you can also use third-party identity providers that work together with your authentication repository.
-
You need to have an option to configure a SAML-based or OIDC-based single sign-on (SSO) integration in your resource (web application or service). Most enterprise applications and services have such capabilities.
-
Your users need to have Portnox AgentP installed on all their devices, even their BYOD/personal devices, or these devices must be enrolled in Intune/Jamf, and Portnox Cloud must then be integrated with Intune/Jamf:
-
You can distribute AgentP using your endpoint management solutions such as Intune, or you can ask your users to install AgentP manually. If you want to ask your users to install AgentP manually, such as on BYOD (bring your own device) devices, you can give them the following link: https://docs.portnox.com/byod/. This link contains end-user instructions for all popular desktop/mobile operating systems: Windows, macOS, iOS, and Android.
-
If you prefer not to use AgentP, you must integrate Portnox Cloud with Intune or Jamf, and you must configure Intune/Jamf so that enrolled devices request Portnox Cloud certificates using the SCEP protocol (see: Automatic onboarding with endpoint management).
-
How is the integration with ZTNA and SSO configured?
For ZTNA to work with SSO, Portnox Cloud needs to be integrated with at least one identity provider and with at least one application.
Both integrations are very similar and do not involve any coding or any external components. Integration happens by exchanging a set of single sign-on (SSO) identifiers and URLs. To integrate with an identity provider or with an application, you simply need to copy some values from the configuration screen of one product and paste them into the right fields on a configuration screen of the other product.
ZTNA supports a globally recognized mechanisms for single sign-on integration: Security Assertion Markup Language (SAML) and OpenID Connect (OIDC).
Integrating with an identity provider
When you integrate ZTNA with an SAML identity provider, you must create a custom app in the identity provider configuration, and then copy at least the following values from the Portnox Cloud configuration screen to a custom app configuration screen:
- The Portnox Cloud identifier that it generated for the identity provider, so that Cloud can recognize and trust the communication
- The Portnox Cloud URL to which the identity provider is supposed to send the user after successfully authenticating them
You must also copy at least the following values from the identity provider’s custom SAML app configuration screen to the Portnox Cloud configuration screen:
- The identity provider’s URL to which Portnox Cloud is supposed to redirect users for authentication
- The identity provider’s identifier used in its single sign-on tokens
- The identity provider’s security certificate, so that Portnox Cloud can verify that it’s communicating with the identity provider and not an intruder
The process for OIDC identity providers is very similar and also involves only copying values across between Portnox Cloud and the identity provider’s administration interface.
In the left-hand side menu, you will find examples for popular identity providers. For example, Entra ID and Google Workspace.
Integrating with a web application
When you integrate a SAML web application with ZTNA, you must copy at least the following values from the Portnox Cloud configuration screen to the application configuration screen:
- The Portnox Cloud identifier that the application is supposed to use during communication, so that Cloud can recognize and trust the incoming authentication requests
- The Portnox Cloud URL to which the application is supposed to redirect the user for authentication
- The Portnox Cloud security certificate, so that the application can verify that it’s communicating with Portnox and not an intruder
You must also copy at least the following values from the application configuration screen to the Portnox Cloud configuration screen:
- The application’s unique identifier, so that Portnox Cloud can identify it during communication
- The application’s URL to which Portnox Cloud is supposed to redirect the user after successfully authenticating them
The process for OIDC applications is very similar and also involves only copying values across between Portnox Cloud and the application’s administration interface.
In the left-hand side menu, you will find examples for popular web applications.
What resources are supported by ZTNA for SSO web based applications?
ZTNA works with all SSO resources that support SP-initiated SAML or OIDC.
In the left-hand side menu, you can see a list of resources that we tested and confirmed to work with ZTNA. This list will grow with more resources that we are able to test either internally or together with our customers.
ZTNA for hosted resources
In this topic, you will learn how Portnox™ Zero Trust Network Access works with hosted resources.
ZTNA for hosted resources provides secure user access to private resources (applications and services), removing the need for VPNs when they are only used to access such applications.
A private resource is an application or service that is not publicly accessible. It can be hosted on-premises or in a secure cloud instance and is meant only for specific people, such as employees, students, or contractors who have been explicitly given access. With the rise of remote work, these resources are often accessed by remote employees, requiring a secure connection over possibly insecure internet networks.
Traditionally, VPNs have been used to create secure connections. However, VPNs are often hard to manage and do not have modern security features like multi-factor authentication, certificate-based authentication, and real-time risk assessment. They may also need special hardware for on-premises deployments.
ZTNA for hosted resources provides a simpler and more cost-effective way to access secure resources. The only requirement is to set up a Docker container or a container instance in a network that has a direct connection to the resources, such as a local network or a virtual network in the cloud.
One key advantage of Portnox ZTNA for hosted resources is its ability to adapt to changes in the security status of devices accessing private resources. By integrating with your UEM solution, such as Intune, or using Portnox AgentP to manage configuration and monitor device risk levels, you can instantly revoke access if a device goes above a set security limit. For example, if a user removes antivirus software, Portnox Cloud can be set to automatically block access to private resources from that device until the issue is fixed.
How does ZTNA for hosted resources work?
If your hosted resource is integrated with ZTNA, here is what happens when an example user tries to access the resource.
For the user, the process is almost the same as logging into a public resource.
-
The user types the address (URL) of the resource in their browser to access it. Depending on how the organization’s administrator sets up Portnox Cloud, this URL can be in the customer’s domain (for example, https://resource.vorlon.com) or in the portnox.com domain (for example, https://resource.us.portnox.com).
Note:To use your own domain, the organization administrator must add a canonical name record to the organization’s DNS server, and upload a TLS certificate (for that subdomain or wildcard) with the corresponding private key to Portnox Cloud. -
The user is then connected to Portnox Cloud. Cloud checks for the user’s certificate in the browser’s underlying operating system, and uses this certificate to securely authenticate the user.

-
Portnox Cloud then creates a secure tunnel within the browser, which connects the user to the private resource without any extra steps needed.
Note:The secure tunnel first connects Portnox Cloud with the Docker container in your resource’s local network, and then connects the Docker container with the resource. The entire connection is fully encrypted and highly secure.
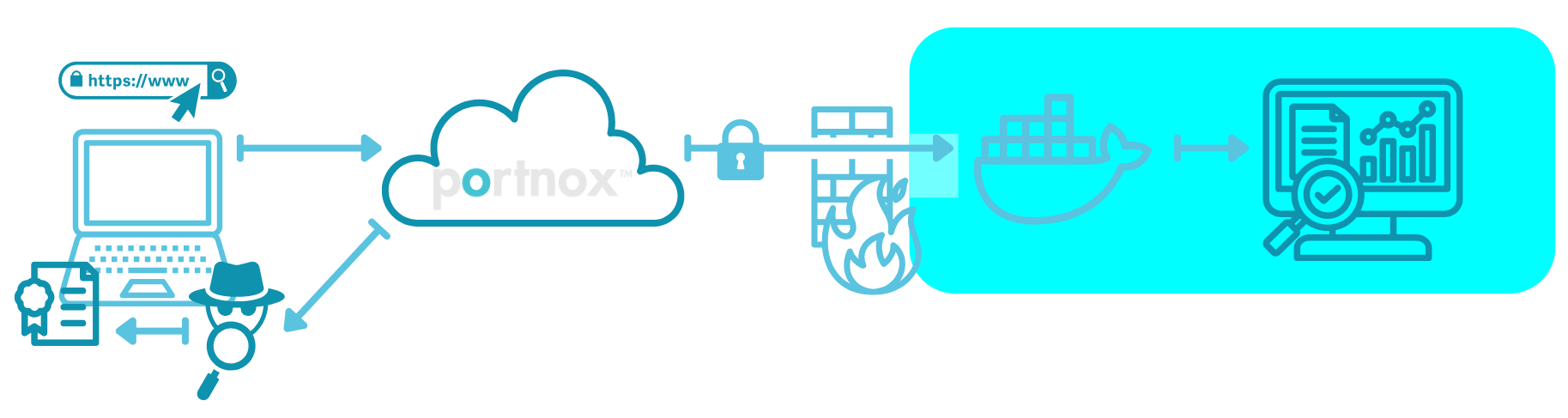
In addition to HTTPS-based hosted resources, ZTNA continues to expand its support for additional technologies. Currently, you can also use ZTNA to securely access the following server types remotely: Remote Desktop Protocol (RDP), Secure Shell (SSH), Virtual Network Computing (VNC), and Telnet.
Access to these resources uses the same mechanism as HTTPS resources: a ZTNA gateway (running as a Docker container) and a web browser. The user enters the resource URL in the browser, ZTNA performs authentication and risk assessment, and the browser functions as the client for the selected protocol.
No third-party clients are required or supported for these protocols. For example, you cannot use PuTTY or a standalone VNC client, as all functionality is provided directly through the browser.
ZTNA is continuously being extended to support additional protocols and to enhance existing ones. For example, support for key-based SSH authentication is currently under development.
What do you need to be able to use ZTNA for hosted resources?
To be able to use ZTNA for hosted resources, you need to meet the following conditions.
- Authentication repository
You need to set up a cloud-based authentication repository, such as Microsoft Entra ID or Google Workspace. Portnox Cloud connects with your authentication repository to authenticate users accessing your private resources.
If you do not use an external repository, you can use Portnox Cloud’s internal repository to manage users.
- Docker container
You need to deploy a Portnox Docker container in a network that has direct access to your private resources, for example, the same local network where you host your private resources. You can run the container on physical or virtual machines using any operating system supported by Docker, including Linux, Windows, or macOS.
If your private resources are hosted in the cloud, you can deploy the container in services like Azure, AWS, or Google Cloud.
The Docker container needs to be able to communicate with the Internet on ports TCP 443 and UDP 3478.
- Certificates
You need to install user or device certificates on all devices that need access to the private resources.
You can install certificates using Portnox AgentP. You can also install them by having Intune or Jamf trigger a request for the certificate from the device to the Portnox SCEP service.
- Optional: custom domain configuration
To use a custom URL in your organization’s domain:
-
You need to add a canonical name (CNAME) record to your domain’s zone on your DNS server.
-
You need to obtain a TLS certificate with a private key for this URL or use an existing wildcard certificate, and upload this certificate to Portnox Cloud.
-
How is the integration with ZTNA for hosted resources configured?
For ZTNA for hosted resources to work, you need to create at least one gateway and at least one resource entry in Portnox Cloud, and you need to run the Docker container in a network with direct access to your private resources.
Creating a gateway entry in Portnox Cloud
You need to choose where the Portnox end of the gateway is located. Portnox Cloud provides three locations: two US-based and one EMEA-based. You can choose the location depending on where you host your resources, but the performance of Portnox Cloud is excellent with both locations. If your resources are hosted outside US/EMEA, you can use either location without any noticeable performance losses.
You need to install Docker on a physical or virtual machine in a network that has direct access to your private resource. If you host your private resources in a cloud such as Azure, AWS, or Google Cloud, you need to use the provider’s mechanism to create a Docker instance in its virtual network, for example, Azure container instances.
You need to create a Docker container by running a command provided by Portnox Cloud. This makes it very easy to create the container correctly, even if your knowledge of Docker is very limited.
Creating an resource entry in Portnox Cloud
-
You need to choose which gateway the resource works with.
-
You need to choose if you want to use a Portnox URL for the resource, or a URL in your organization’s domain:
-
If you want to use a portnox.com URL, this URL will be either: resource_name.us.portnox.com, if your resource is connected to the US-based gateway, or resource_name.eu.portnox.com, if your resource is connected to the EMEA-based gateway.
Note:Make sure to check if your web resource will accept connections when accessed using this URL. If your web security solution has an anti-CSRF feature, you will need to configure it to allow this URL. -
If you want to use your organization’s URL, for example, https://resource.vorlon.com, you need to upload a certificate and a private key obtained from a certification authority for resource.vorlon.com (or a wildcard certificate for *.vorlon.com), and you need to add a canonical name (CNAME) record to your DNS server’s zone, for example:
resource.vorlon.com. IN CNAME resource.us.portnox.com.
-
-
You need to supply the IP address and port of the private resource, which must be accessible from the Docker container. For example, if you use a Class A (10.0.0.0/16) network, you can have your Docker container running at 10.250.0.10, and you can have your resource running on a web server at 10.1.9.57, on port 443, using the HTTPS protocol.
-
If your resource runs on the same IP address and port number as other resources, you need to provide the Host HTTP header value that will be sent to the web server to open the correct resource.
-
For resources other than HTTPS, additional options may be available, such as display size settings for RDP and copy/paste support for SSH, Telnet, and VNC.
