Configure ZTNA with on-premises console resources and a Linux Docker container
In this topic, you will learn how to configure Portnox™ ZTNA to allow your remote users to access your private console resources hosted on-premises, by using a Docker container in an on-premises machine with Linux.
In this scenario:
-
You want your remote users to be able to access private console resources that you host on-premises.
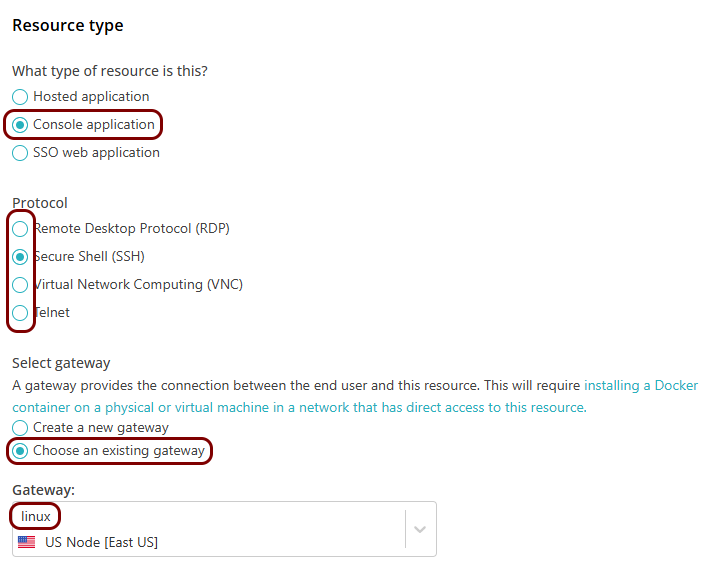
Note:At the moment, ZTNA supports the following console resources: RDP, SSH, VNC, and telnet. -
You need to host a Portnox Docker container in the on-premises local network to be able to access these resources. You want to use a Linux-based physical or virtual machine to run Docker and host the container.
We assume that you have already set up a physical or virtual machine on your chosen platform with Linux installed. We also assume that this machine is running in a network that has direct access to the resource. We will provide examples for Ubuntu and Red Hat, which you can easily adapt for other Linux distributions. We also assume that you already distributed certificates to your client devices.
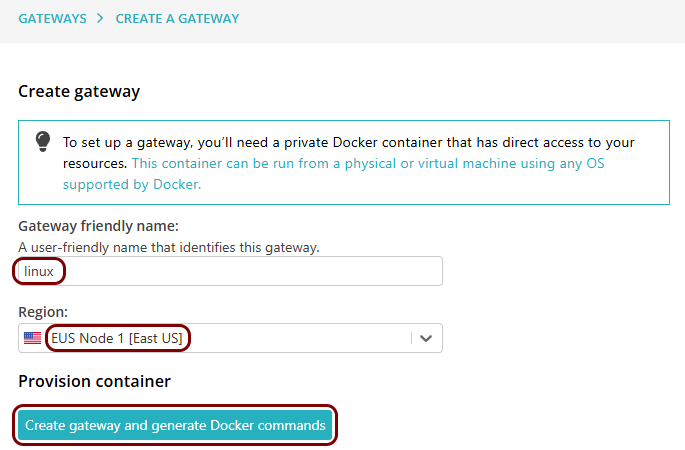
Set up the ZTNA gateway in Portnox Cloud
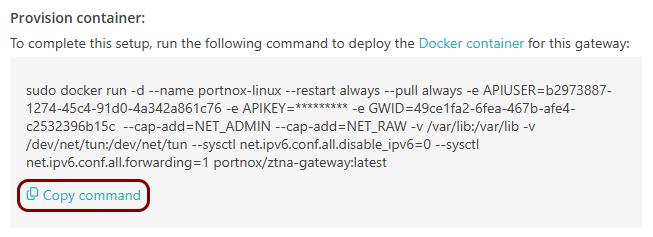
In this section, you will set up a ZTNA gateway in Portnox Cloud, install Docker on your machine, and run the Portnox ZTNA Docker container.
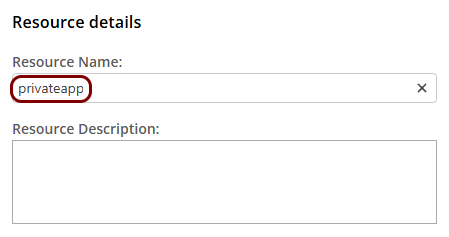
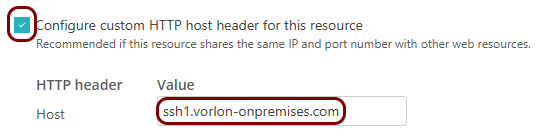
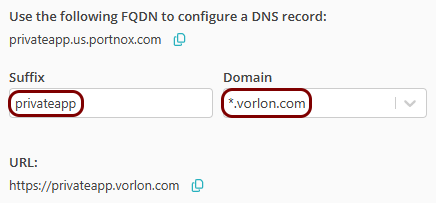
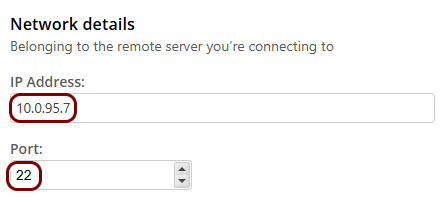
Set up the ZTNA resource in Portnox Cloud
In this section, you will set up a ZTNA resource in Portnox Cloud and configure it to access your private resource hosted in the same local network as the Docker container.
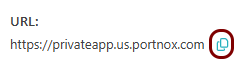
Result: Your users can now access your private console resource by typing the URL in the browser.
Configure the hosted application access control policy
In this section, you will configure the access control policy for groups that you want to have access to this hosted application.
Automatically update an existing local server container
In this section, you will learn how to automatically update your Docker container to the latest version by deploying another Docker container: portnox-autoupdate.