Ethernet 802.1X configuration – Cisco (most models)
In this topic, you will learn how to configure Cisco switches to work together with Portnox™ Cloud and 802.1X RADIUS authentication for wired Ethernet connections.
Important:
This guide gives general instructions for integrating Portnox Cloud with
specific third-party devices. We try to provide useful examples for common models, but settings can differ between
manufacturers, models, and environments. Because of this, we cannot guarantee these steps will work in every case.
For questions or problems with RADIUS setup – which is an industry standard and not specific to Portnox – or with
device-specific settings and troubleshooting, we recommend checking the device manufacturer’s documentation and contacting
their support team. Portnox Support can help when possible, but detailed setup of third-party devices is usually best
handled by the manufacturer. We also recommend updating your NAS device firmware to the latest version, as old
firmware can cause issues.
Important:
All values in this configuration are examples. Make sure to adjust the
configuration to your individual profile names, RADIUS server addresses, ports, and keys by replacing the values that are
presented as underlined italics.
General configuration (IOS/NX-OS)
This is a general configuration template for Cisco switches with the IOS or NX-OS operating system.
Warning:
We tested this configuration on several models and several versions of Cisco operating systems (IOS and
NX-OS) but we cannot guarantee that it will cover every Cisco model. Also, the configuration is general and may not fit
every single environment. Therefore, to get the most accurate and current configuration guidance on switch 802.1X
configuration, we strongly recommend that you refer to the documentation provided by Cisco on these topics for your
particular device model and OS version.
Here is the entire example configuration for your convenience:
aaa new-model
!
aaa group server radius PORTNOX
server name PORTNOX-CLOUD-US
server name PORTNOX-CLOUD-EMEA
exit
!
aaa authentication dot1x default group PORTNOX
aaa authorization network default group PORTNOX
aaa accounting update newinfo
aaa accounting identity default start-stop group PORTNOX
aaa accounting send stop-record always
!
dot1x system-auth-control
!
dot1x critical eapol
dot1x critical recovery delay 2000
!
radius-server dead-criteria time 30 tries 4
radius-server deadtime 30
!
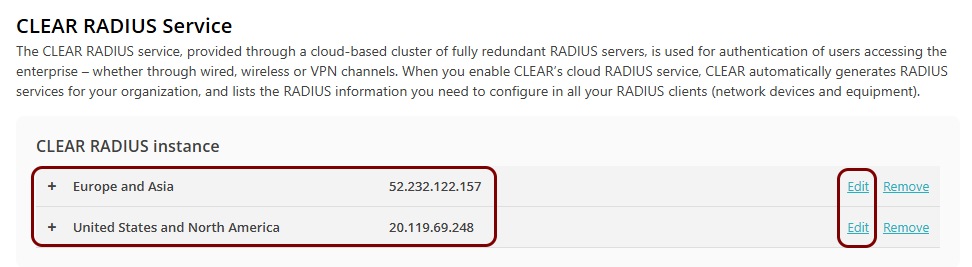
radius server PORTNOX-CLOUD-US
address ipv4 20.119.69.248 auth-port 10322 acct-port 10323
key rTHO9HEo9BcqfC9Yg0hHFelK6o0tH8N1
exit
!
radius server PORTNOX-CLOUD-EMEA
address ipv4 52.232.122.157 auth-port 10476 acct-port 10477
key fnSrSEHhXFZ5Rqpz756NJhkeVqIHTlPt
exit
!
interface gigabitethernet 0/1
authentication port-control auto
dot1x pae authenticator
authentication host-mode single-host
mab
authentication order dot1x mab
!
vlan 10
interface vlan 10 ip address 10.0.10.0 255.255.255.0
!
interface gigabitethernet 0/1
authentication event server dead action authorize vlan 10IBNS 2.0 (multi-domain)
This is a multi-domain configuration template for Cisco switches with IBNS 2.0.
Here is the entire example configuration for your convenience:
aaa new-model
!
radius server PORTNOX-CLOUD-US
address ipv4 20.119.69.248 auth-port 10322 acct-port 10323
key rTHO9HEo9BcqfC9Yg0hHFelK6o0tH8N1
exit
radius server PORTNOX-CLOUD-EMEA
address ipv4 52.232.122.157 auth-port 10476 acct-port 10477
key fnSrSEHhXFZ5Rqpz756NJhkeVqIHTlPt
exit
aaa group server radius PORTNOX
server name PORTNOX-CLOUD-US
server name PORTNOX-CLOUD-EMEA
exit
aaa authentication dot1x default group PORTNOX
aaa authorization network default group PORTNOX
!
dot1x system-auth-control
!
class-map type control subscriber match-all DOT1X
match method dot1x
!
class-map type control subscriber match-all DOT1X_FAILED
match method dot1x
match result-type method dot1x authoritative
!
class-map type control subscriber match-all DOT1X_NO_RESP
match method dot1x
match result-type method dot1x agent-not-found
!
class-map type control subscriber match-all MAB
match method mab
!
class-map type control subscriber match-all MAB_FAILED
match method mab
match result-type method mab authoritative
!
policy-map type control subscriber DOT1X_MAB_MULTIDOMAIN
event session-started match-all
10 class always do-until-failure
10 authenticate using dot1x priority 10
20 authenticate using mab priority 20
event authentication-failure match-first
10 class DOT1X_FAILED do-until-failure
10 terminate dot1x
20 class MAB_FAILED do-until-failure
10 terminate mab
20 authenticate using dot1x priority 10
30 class DOT1X_NO_RESP do-until-failure
10 terminate dot1x
20 authentication-restart 60
40 class always do-until-failure
10 terminate mab
20 terminate dot1x
30 authentication-restart 60
event agent-found match-all
10 class always do-until-failure
10 terminate mab
20 authenticate using dot1x priority 10
!
interface GigabitEthernet1/0/1
switchport access vlan 613
switchport mode access
switchport voice vlan 612
access-session closed
access-session host-mode multi-domain
access-session port-control auto
mab
dot1x pae authenticator
spanning-tree portfast
service-policy type control subscriber DOT1X_MAB_MULTIDOMAINNote:
The following is an alternative policy map segment of the configuration. We recommend this setup if the above
configuration causes the NAS device to attempt MAB authentication even for 802.1X devices, resulting in excess
alerts.
!
policy-map type control subscriber DOT1X_MAB_MULTIDOMAIN
event session-started match-all
10 class always do-until-failure
10 authenticate using dot1x priority 10
event authentication-failure match-first
10 class DOT1X_NO_RESP do-until-failure
10 terminate dot1x
20 authenticate using mab priority 20
20 class MAB_FAILED do-until-failure
10 terminate dot1x
20 authentication-restart 60
30 class DOT1X_FAILED do-until-failure
10 terminate dot1x
20 authenticate using mab priority 20
40 class always do-until-failure
10 terminate dot1x
20 terminate mab
30 authentication-restart 60
event agent-found match-all
10 class always do-until-failure
10 terminate mab
20 authenticate using dot1x priority 10
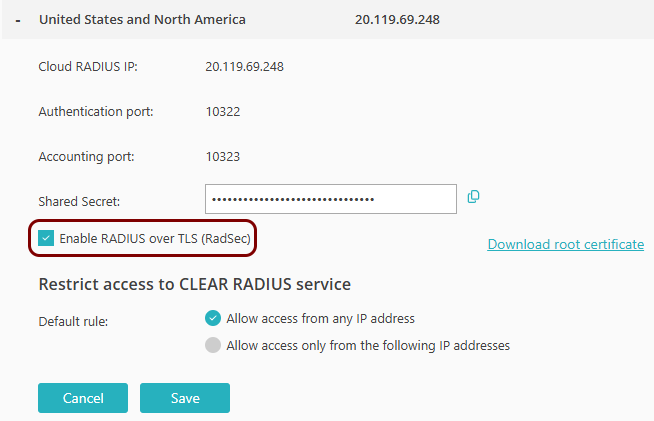
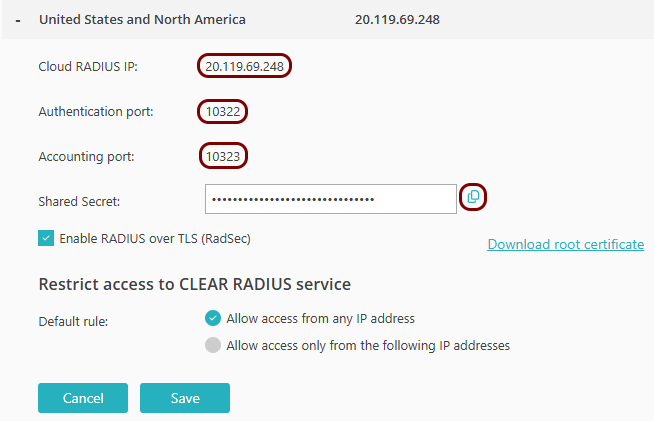
!Cisco 9200/9300 RadSec
This section contains an example configuration for the Cisco Catalyst 9200/9300 Ethernet switches and Portnox Cloud RADIUS servers using secure RADIUS (RadSec) connections.