Set up a local RADIUS server using a virtual machine
In this topic, you will learn how to install and run local RADIUS servers that work together with Portnox™ Cloud using virtual machines.
For information about how the Cloud RADIUS servers work, see the following topic: How do RADIUS servers work in Portnox Cloud?.
-
In the Cloud portal top menu, click on the Settings option.
-
In the Cloud portal left-hand side menu, click on the Services > LOCAL RADIUS SERVICE > Local RADIUS images option.
-
Under the Local RADIUS images heading, click on the relevant link to download the local RADIUS
server virtual machine file:
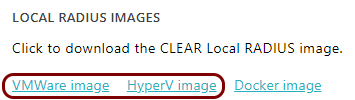
- Click on the VMware image link, if you use one of the following hypervisors: VMware Workstation, VMware Fusion, VMware ESXi.
- Click on the HyperV image link, if you use one of the following hypervisors: Microsoft Hyper-V, Oracle VirtualBox, Citrix Hypervisor, Proxmox Virtual Environment, Xen Project.
Save the downloaded file locally, you will use it later, after you prepare the configuration.
-
Under the Local RADIUS instance heading, click on the Add new RADIUS profile
(VM) link to begin the configuration process for the new local server instance.

Your browser will display the Add new Local RADIUS cluster heading with configuration fields for the new local server instance.
-
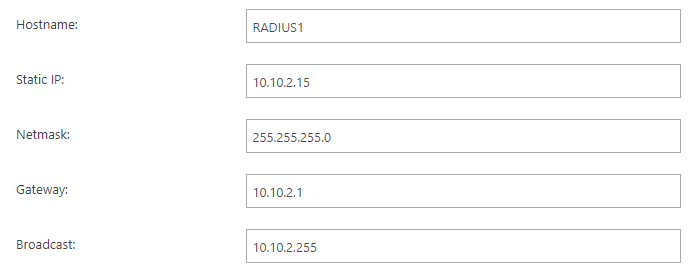
In the Hostname field, enter the local hostname for your local RADIUS server.
This is the hostname that your NAS devices will use to contact the local RADIUS server. However, using the IP address in NAS configuration is recommended.
-
In the Static IP field, enter the static local IP for your local RADIUS server.
This is the IP that your NAS devices will use to contact the local RADIUS server.
- In the Netmask field, enter the netmask defining the subnet for the entered static IP address.
- In the Gateway field, enter the default gateway IP address for the entered static IP address.
-
In the Broadcast field, enter the broadcast IP address for the subnet of the entered static IP
address.
-
Add DNS servers:
- In the Domain Name Servers (DNS) section, click on the Add DNS link to add the IP of at least one DNS resolver.
- In the IP field, enter the IP address of the DNS resolver and click on the Add button.
-
Repeat the above process if necessary by clicking on the Add DNS link to add another DNS
resolver.
You can also click on the Remove link on the right-hand side, if you want to remove one of the added DNS resolvers.

-
Copy the value of the Shared Secret field to use it when configuring NAS devices to contact this
local RADIUS server.
If you want to generate a different shared secret, click on the Regenerate link on the right-hand side.
Note:You can also display and copy this value later. - Optional:
In the Syslog Destination field, enter the IP and port of a local syslog server, if you want to
stream logs from the virtual machine to a syslog server.
If you leave this field empty, Portnox Cloud will not send syslog streams. If you omit the port number, Cloud will use the default port 514.
- Optional:
In the SNMP Configuration section, click on the Enable SNMP v1 and v2c
checkbox to enable support for SNMP v1/v2 protocols on the local RADIUS server.
-
In the Community string field, enter the community string for this local RADIUS
server.
Write down this community string, so you can use it later to configure other devices. The community string acts like a password/shared secret and lets other devices authenticate via SNMP v1 or v2 with the local RADIUS server.
-
In the Community string field, enter the community string for this local RADIUS
server.
- Optional:
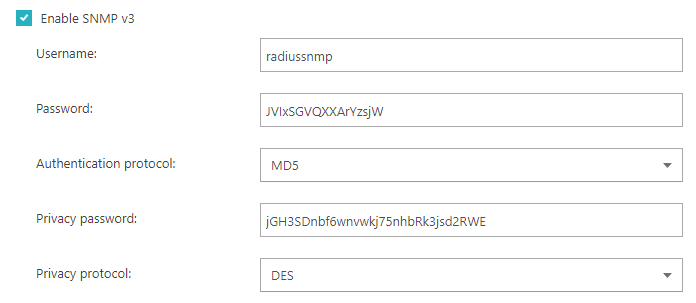
In the SNMP Configuration section, click on the Enable SNMP v3 checkbox
to enable support for the secure SNMP v3 protocol on the local RADIUS server and provide the configuration
information.
-
In the Username field, enter the SNMP v3 username.
The SNMP username is a unique identifier for an SNMP v3 user.
-
In the Password field, enter the SNMP v3 password.
The SNMP v3 password, also known as the authentication key or authentication passphrase, is a shared secret between the SNMP manager and the SNMP agent.
-
In the Authentication protocol field, select the SNMP v3 authentication protocol.
The authentication protocol determines the method used to authenticate the SNMP v3 user: HMAC-MD5 or HMAC-SHA.
-
In the Privacy password field, enter the SNMP v3 privacy password.
The privacy password, also known as the encryption key or encryption passphrase, is used for encrypting SNMP v3 messages using symmetric encryption.
-
In the Privacy protocol field, select the SNMP v3 privacy protocol.
The privacy protocol is the method used to encrypt SNMP v3 messages: DES or AES 128.
-
In the Username field, enter the SNMP v3 username.
- Optional:
In the Fast reauthentication section, click on the Enable EAP session
resumption checkbox to turn on the fast reconnect functionality.
Then, if needed, change the default Session lifetime (hours) value.

If this setting is on, if a device loses connection to the local RADIUS server and reconnects within the session lifetime, it can authenticate quickly by providing a valid connection session ID. We recommend using this setting, along with higher priority for the local RADIUS server, for devices that need fast reconnection.
Note:The session lifetime counts from the last successful connection, not the disconnection. - Optional:
In the Fast reauthentication section, click on the Enable Local cache
checkbox to let the local RADIUS server authenticate devices on the basis of cached MAC addresses. Then, if needed,
change the default Cache lifetime (hours) value.

If this setting is on, if a device loses connection to the local RADIUS server and reconnects within the cache lifetime, it is automatically authenticated if the local RADIUS server recognizes the MAC address. We recommend using this setting, along with higher priority for the local RADIUS server, for devices that need fast reconnection. The cache lifetime counts from the last successful connection, not the disconnection.
Note:The local cache is a different mechanism than the primary RADIUS server cache. The primary RADIUS server cache enables clients to authenticate for up to 7 days with no connection to the Cloud RADIUS servers and this period is not configurable. For more explanation of the differences between the two caching mechanisms, see the following topic: How do local RADIUS servers work?. - Optional:
If you want to access the local RADIUS instance using SSH, click on the Enable SSH
checkbox.
 Note:To learn how to troubleshoot the RADIUS instance using the PuTTY application and Linux commands, see the following topic: How to troubleshoot the local RADIUS/TACACS+ instance using SSH.
Note:To learn how to troubleshoot the RADIUS instance using the PuTTY application and Linux commands, see the following topic: How to troubleshoot the local RADIUS/TACACS+ instance using SSH. -
Click on the Save and Download button to save the configuration and download the configuration
ISO image.
Important:The downloaded ISO image is required to configure the virtual machine file downloaded earlier.

-
Run the downloaded local RADIUS virtual machine file in a hypervisor together with the downloaded configuration.
- To learn how to configure the local RADIUS server in Microsoft Hyper-V, read this topic: Run the local RADIUS server in Microsoft Hyper-V.
- To learn how to configure the local RADIUS server in VMware Workstation, read this topic: Run the local RADIUS server in VMware Workstation.
- To learn how to configure the local RADIUS server in Oracle VirtualBox, read this topic: Run the local RADIUS server in Oracle VirtualBox.
