Integrate Tailscale with Zero Trust Network Access
In this topic, you will find general instructions on how to integrate Tailscale with Portnox™ Zero Trust Network Access.
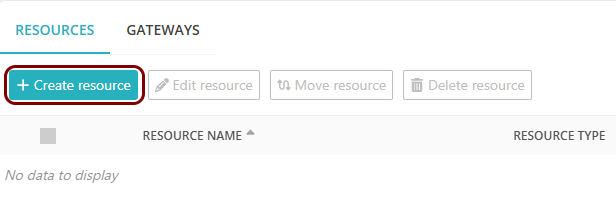
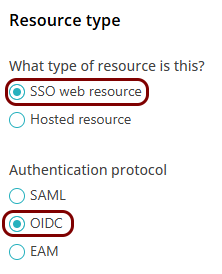
Create a Portnox Cloud application configuration
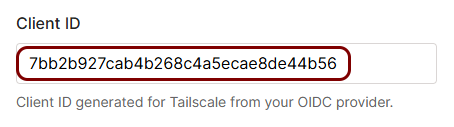
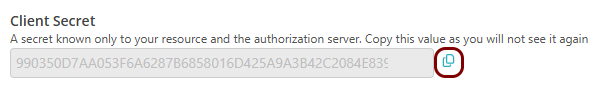
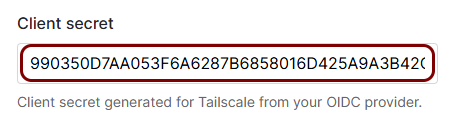
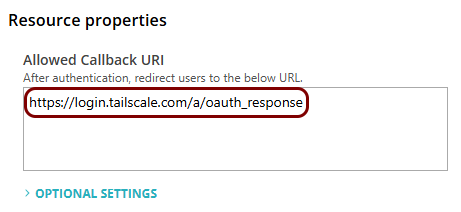
In this step, you will create a configuration in Portnox Cloud that will contain all the information necessary to integrate with Tailscale.
Create a WebFinger endpoint for Tailscale
In this section, you will create a file that will serve as a WebFinger endpoint for Tailscale, and upload this file to your web server.
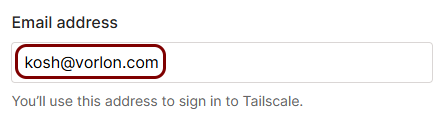
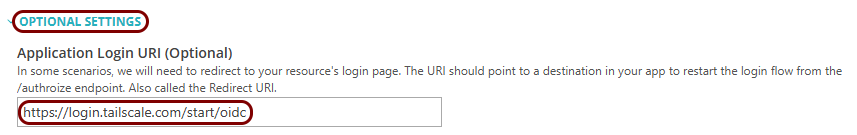
When signing up for Tailscale using an OIDC identity provider, you must serve a WebFinger endpoint from your web server to prove that you are the owner of the domain. For example, if you sign up as kosh@vorlon.com, you must serve the endpoint from the following URL: https://vorlon.com/.well-known/webfinger. Make sure that you have access to the web server and can create the relevant file when signing up for Tailscale.
Sign up for Tailscale using a custom OIDC identity provider
In this section, you will sign up for a new Tailscale tenant using Portnox as a custom OIDC identity provider.
Finalize the configuration
In this section, you will finalize the configuration in Portnox Cloud and Tailscale.
-
Finalize the configuration in the Portnox tab.
-
Finalize the configuration in the Tailscale tab.
Result: You have configured Tailscale to be accessible using Portnox Zero Trust Network Access.