Add Microsoft Entra ID as an OIDC identity provider for Zero Trust Network Access
In this topic, you will find instructions on how to add Microsoft Entra ID as an OIDC identity provider for Portnox™ Zero Trust Network Access.
Prerequisites:
-
You must first integrate your Portnox Cloud instance with your Microsoft Entra ID repository (Azure Active Directory) as an authentication provider. For more information, see the following topic: Integrate with Microsoft Entra ID.
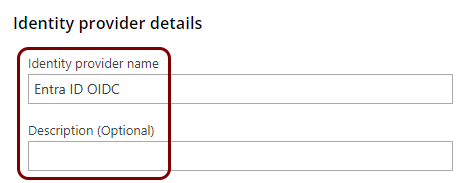
Create a new identity provider configuration in Portnox Cloud
In this section, you will create a new OIDC identity provider configuration in Portnox Cloud
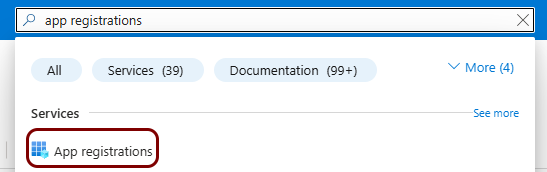
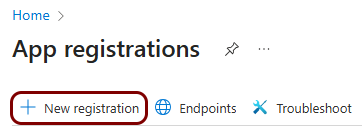
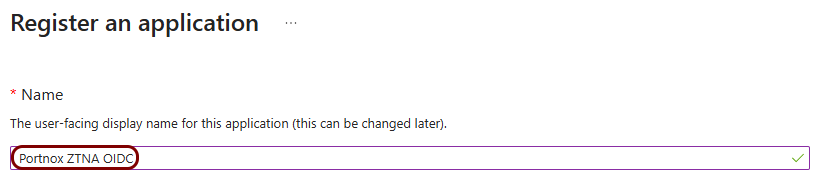
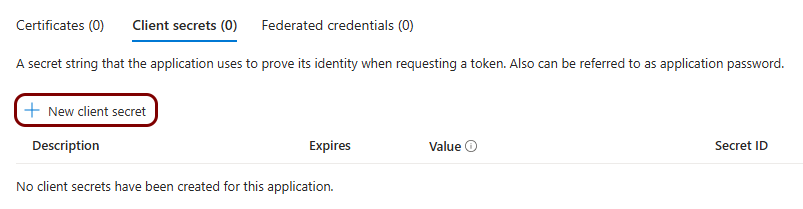
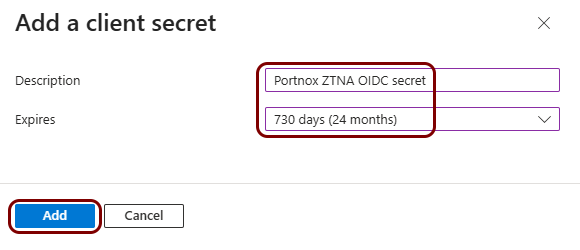
Create a new identity Entra ID application registration
In this section, you will access the Microsoft Azure administrative interface and use it to create a new Entra ID application registration that will handle integration with Portnox Cloud.
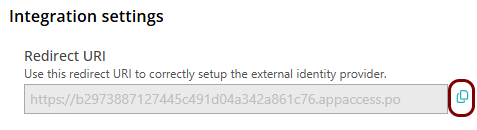
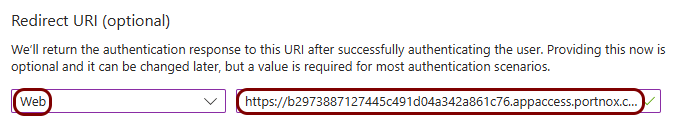
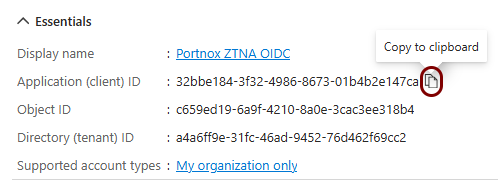
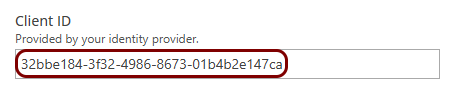
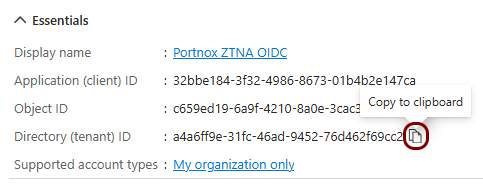
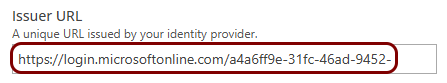
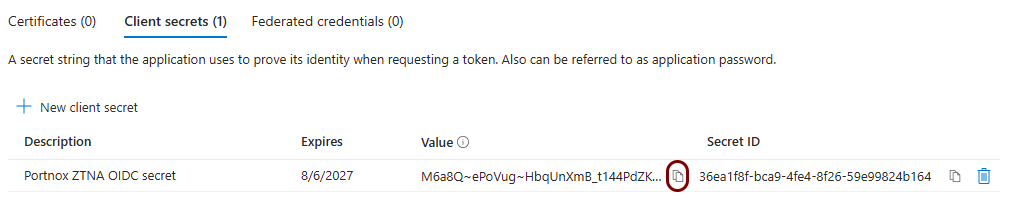
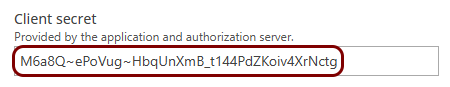
Copy configuration values from the Azure tab to the Portnox tab
In this section, you will copy the values displayed by the Entra ID application setup section and paste them in the relevant fields in Portnox Cloud.