Add Zero Trust Network Access to the Okta Platform as an authentication factor
In this topic, you will find instructions on how to add Portnox™ Zero Trust Network Access to the Okta Platform as an authentication factor.
Prerequisites:
-
You must first integrate your Portnox Cloud instance with your Okta Workforce Identity repository as an authentication provider. For more information, see the following topic: Integrate with Okta Wokforce Identity.
When Portnox ZTNA is added as an authentication factor to Okta, every time you access a web application using Okta single sign-on (SSO), you are verified by Portnox ZTNA instead of only receiving Okta Verify prompts. This adds all the benefits of ZTNA, such as device compliance checks.
This setup lets you configure the integration once and then use it with any app that supports Okta SSO. You do not need to configure Okta as an identity provider for each app individually. However, this also gives you less control over specific apps, since you cannot apply different configurations in Portnox Cloud (for example, policies).
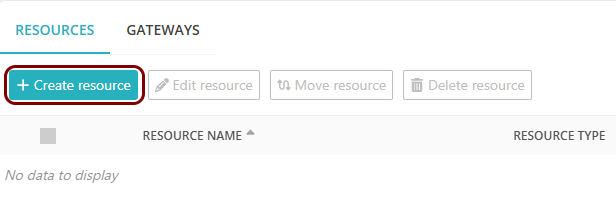
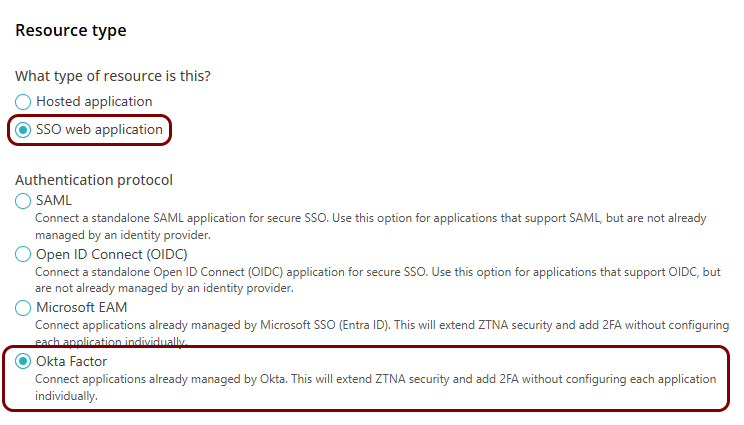
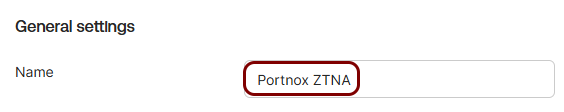
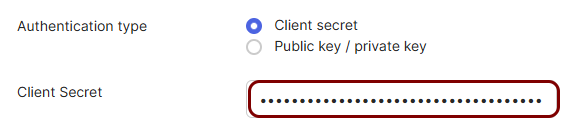
Create a new resource configuration in Portnox Cloud
In this section, you will create a new resource configuration in Portnox Cloud, which will let you add Portnox ZTNA as a factor to the Okta Platform.
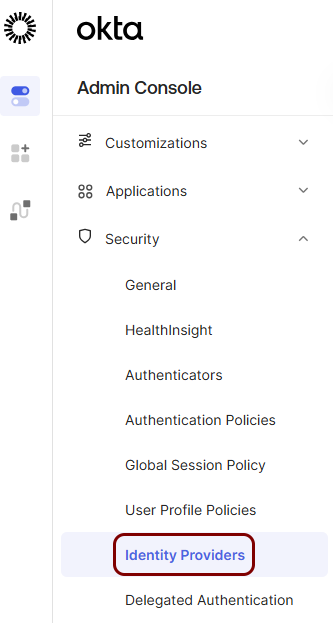
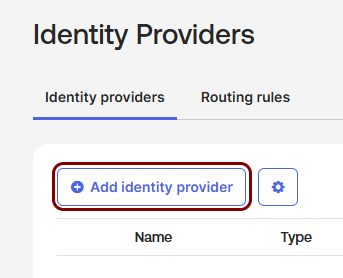
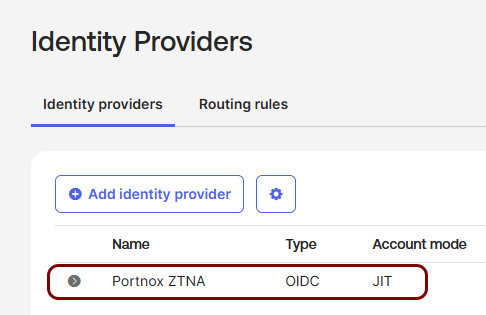
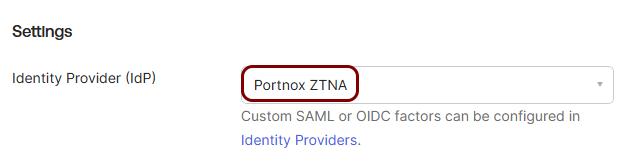
Create an Identity Provider configuration in Okta
In this section, you will create an identity provider configuration in the Okta Platform.
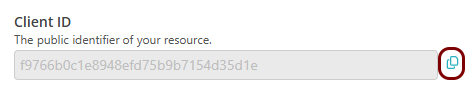
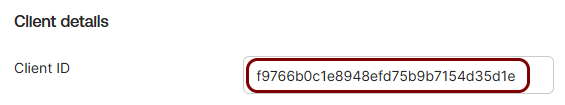
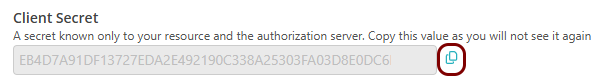
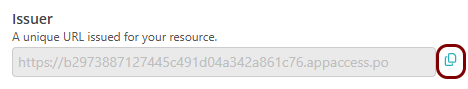
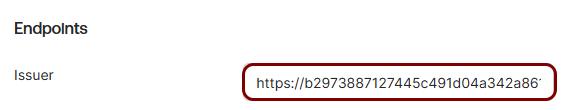
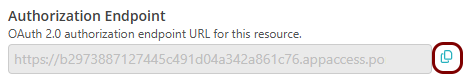
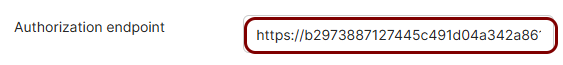
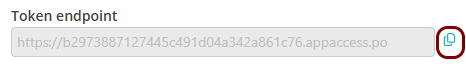
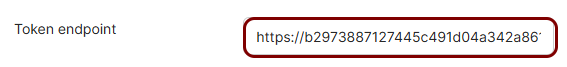
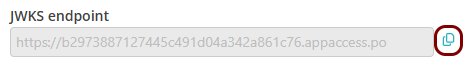
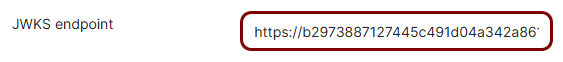
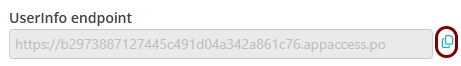
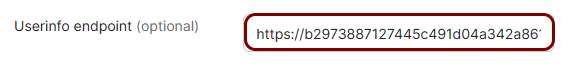
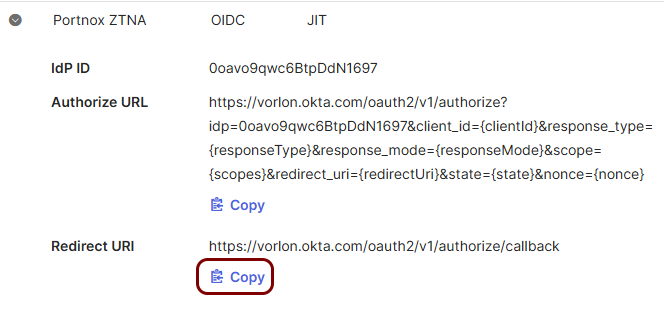
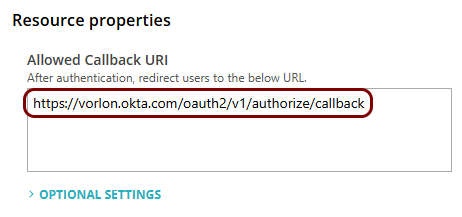
Copy values between the Portnox tab and the Okta tab
In this section, you will keep switching between the Portnox tab and the Okta tab, and copy values required for the integration.
Finalize the configuration in Portnox Cloud
In this section, you will finalize the configuration in Portnox Cloud.
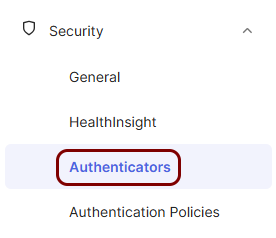
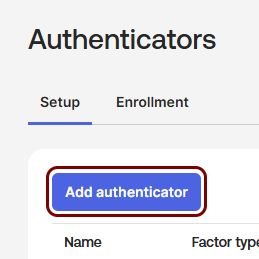
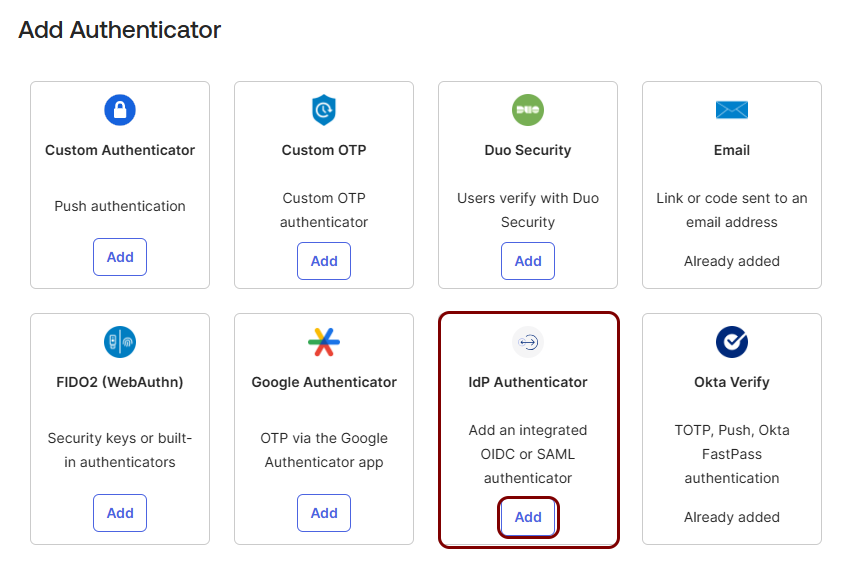
Add ZTNA as an authenticator in the Okta Platform
In this section, you will add Portnox ZTNA as an Authenticator in the Okta Platform.
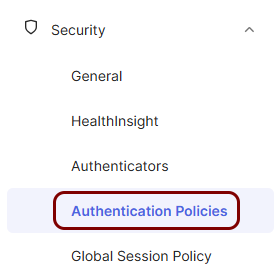
Modify Okta app sign-in policies
In this section, you will modify Okta authentication policies as needed by your organization.