Integrate GitLab with Zero Trust Network Access
In this topic, you will find general instructions on how to integrate GitLab with Portnox™ Zero Trust Network Access using the conditional access method.
Create a Portnox Cloud application configuration
In this step, you will create a configuration in Portnox Cloud that will contain all the information necessary to integrate with GitLab.
-
In a new tab of your browser, open your Portnox Cloud account by accessing the following URL: https://clear.portnox.com/
From now on, we will call this tab the Portnox tab.
-
In the Cloud portal top menu, click on the Zero Trust Resources option.

-
On the Resources screen, click on the Create resource button.
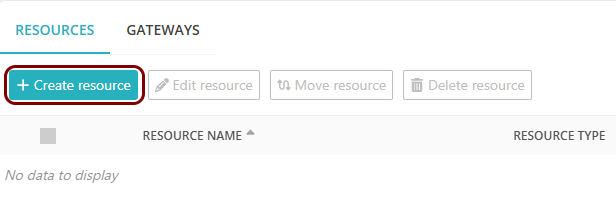
- In the What type of resource is this? section, select the SSO web resource option.
- In the Authentication protocol section, select the SAML option.
- Click on the Next button.
- Optional: If you have more than one SAML identity provider configured, select the identity provider in the Select an identity provider to use for this resource section.
-
In the Resource details section, enter a Resource name and
optionally a Description.

In this example, we used the name GitLab for the new application configuration but you can use any name you like.
- Keep this browser tab open. You will need it later.
Open your GitLab SAML SSO settings
In this section, you will access your GitLab administrative interface and find the SAML single sign-on (SSO) settings.
-
In another tab of your browser, open GitLab by accessing the following URL: https://gitlab.com/. Then, log in to your account.
From now on, we will call this tab the GitLab tab.
-
Go to the SAML SSO settings for the group that you administer.
You can access your group’s SAML SSO settings in two ways:
Click: , and from the left-hand menu, select the option.

Go to the following URL: https://gitlab.com/groups/<your_group>/-/saml, replacing <your_group> with the identifier of your group.
Copy configuration values from the Portnox tab to the GitLab tab
In this section, you will copy the values displayed by Portnox Cloud and paste them in the relevant fields in the GitLab SAML SSO setup section.
-
In the Portnox tab, in the Service details section, click on the ⧉ icon next to the Sign-In URL / SSO URL field to copy the
value.
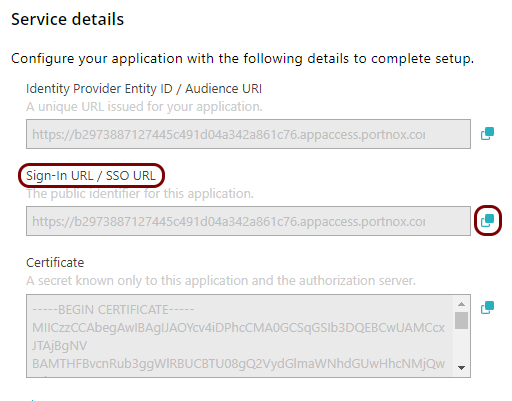
-
In the GitLab tab, click on the empty field next to the Identity provider single sign-on URL
label and paste the value copied from Portnox Cloud.
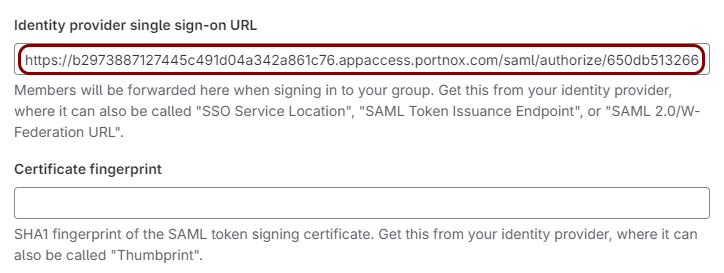
-
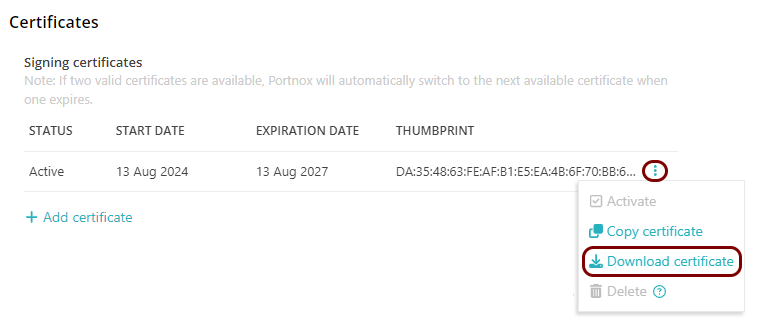
In the Portnox tab, in the section, click on the ⋮ icon next to the
Active certificate and select the Download certificate option to
download the certificate to the local drive.
-
Open the certificate in your operating system. Then, find and copy its thumbprint value.
For example:
- In Windows:
-
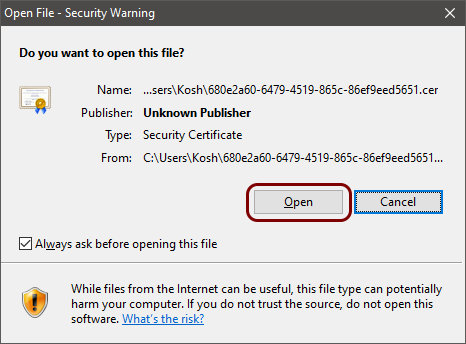
Double-click on the downloaded certificate file and click on the Open button.
-
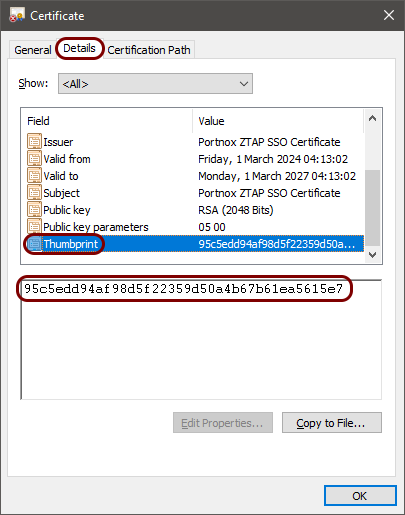
In the Certificate window, go to the Details tab, scroll down the list to see the Thumbprint entry, click on it, and then double-click on the value in the field below and press the key combination CTRL + C to copy the value to the clipboard.
-
- In macOS:
-
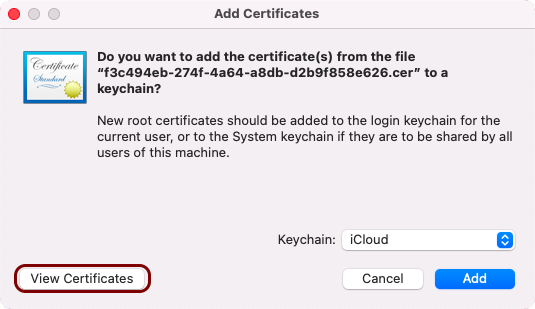
Double-click on the downloaded certificate file and click on the View Certificates button.
-
Click on the Details label to show certificate details.
-
Scroll down to the Fingerprints section, mark the value of the SHA-1 field, and press the key combination Command + C to copy the value to the clipboard.
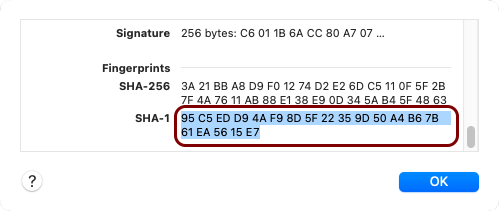
-
- In Windows:
-
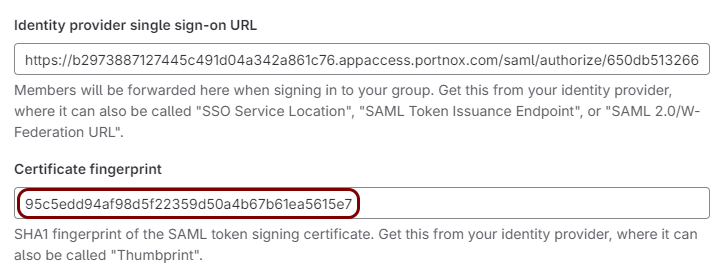
In the GitLab tab, click on the empty field next to the Certificate fingerprint label and
paste the value copied from your operating system.
Copy configuration values from the GitLab tab to the Portnox tab
In this section, you will copy the values displayed in your GitLab SAML SSO setup section, and paste them in the relevant fields in Portnox Cloud.
-
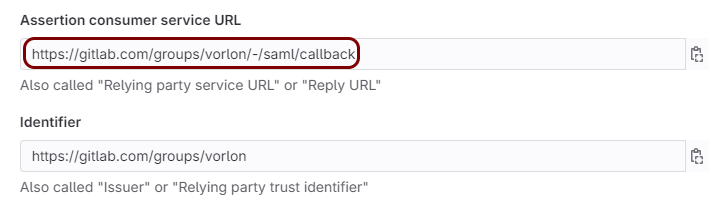
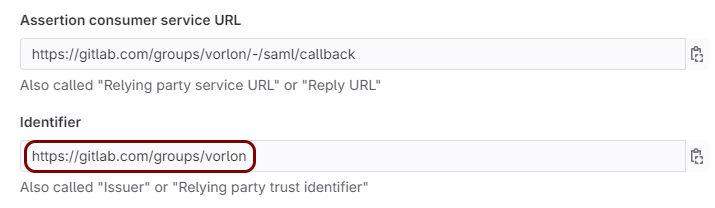
In the GitLab tab, click on the ⧉ icon next to the Assertion
consumer service URL field.
-
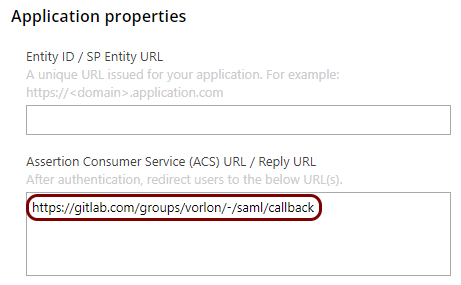
In the Portnox tab, in the Resource properties section, click on the empty field under the
Assertion Consumer Service (ACS) URL / Reply URL heading and paste the value copied from
GitLab.
-
In the GitLab tab, click on the ⧉ icon next to the
Identifier field.
-
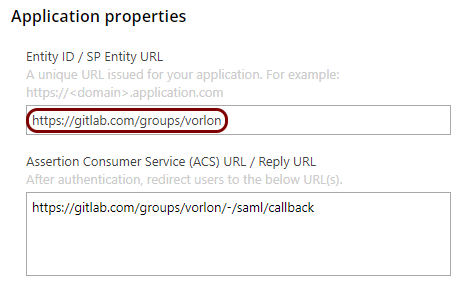
In the Portnox tab, in the Resource properties section, click on the empty field under the
Entity ID / Service Provider Entity URL heading and paste the value copied from
GitLab.
Finalize the configuration
In this section, you will finalize the configuration in Portnox Cloud and GitLab.
-
Finalize the configuration in the Portnox tab.
-
Finalize the configuration in the GitLab tab.
Result: You have configured GitLab to be accessible using Portnox Zero Trust Network Access.


