How does Portnox Cloud handle certificate revocation?
In this topic, you will learn how Portnox Cloud handles certificate revocation for user and device certificates.
There are two options in Portnox Cloud for publishing revocation information for certificates:
-
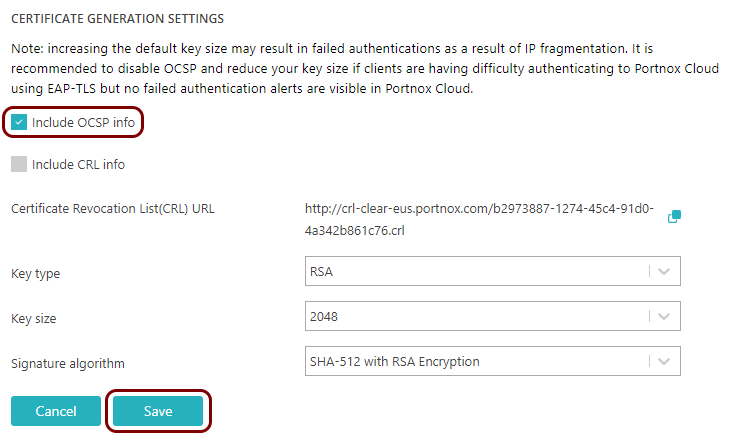
If you use the Portnox root certificate and public key (default setting) to generate user/device certificates, you can include OCSP (online certificate status protocol) information with the certificate. This information is included in the Certificate Authority Information Access extension.
To include OCSP information with Portnox Cloud certificates, go to the section, click on the Edit link, activate the Include OCSP info checkbox, and then click on the Save button.
-
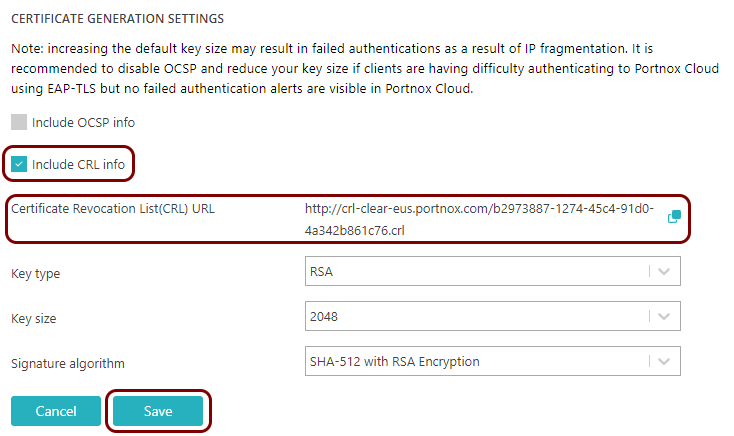
If you use the Portnox root certificate and public key (default setting) to generate user/device certificates, you can use your tenant’s CRL (certificate revocation list) hosted by Portnox.
To include CRL information with Portnox Cloud certificates, go to the section, click on the Edit link, activate the Include CRL info checkbox, and then click on the Save button.
The URL of your CRL is displayed in the Certificate Revocation List (CRL) URL field.
-
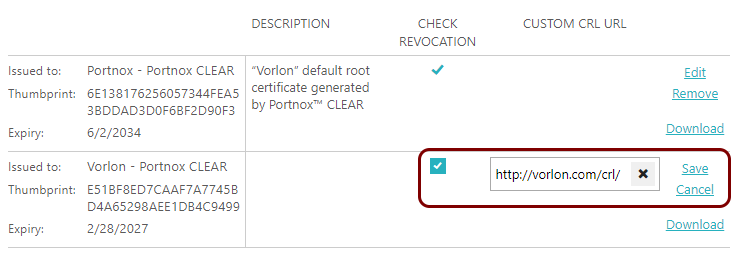
If you use your own certificate authority to generate certificates, and you publish a CRL (certificate revocation list) on your own web server, you can include the URL of that CRL when adding your own certificate.
Follow the procedure described in the following topic: Onboard devices using your own root certificate authority. After uploading your own certificate, click on the Edit link, activate the checkbox in the CHECK REVOCATION column, and enter your CRL URL in the CUSTOM CRL URL column. Then, click on the Save link.
-
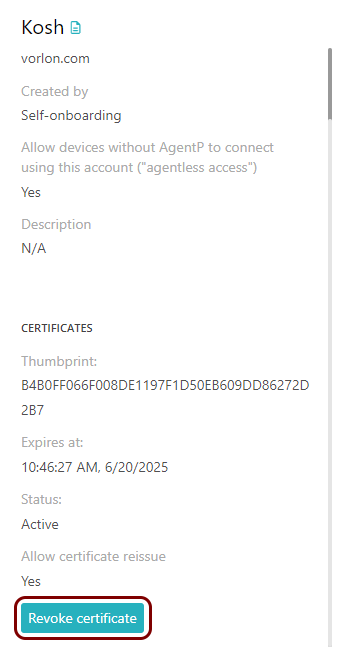
To revoke a certificate generated by Portnox Cloud, go to the Devices pane, select an account, and scroll down the right-hand side pane. If the account has a certificate that can be revoked, there is a Revoke certificate button.
 Note: The effect is not immediate. The certificate revocation lists hosted by Portnox Cloud are updated every 90 minutes.
Note: The effect is not immediate. The certificate revocation lists hosted by Portnox Cloud are updated every 90 minutes.
SCEP certificate revocation
Revocation, invalidation, or removal of SCEP certificates is fully handled by the endpoint management software that requested the certificate from Portnox Cloud in the first place.
The SCEP protocol does not specify a method to request certificate revocation. Therefore, to invalidate certificates requested originally through SCEP, the endpoint management software must remove certificates that are installed on devices. For example, the Intune documentation states that SCEP certificates are removed but not revoked when using a third-party certification authority (such as Portnox Cloud).
