Guest access – Cisco Wireless Controller
In this topic, you will learn how to configure a Cisco Wireless Controller to work together with the Portnox™ Cloud captive portal for guest user authentication.
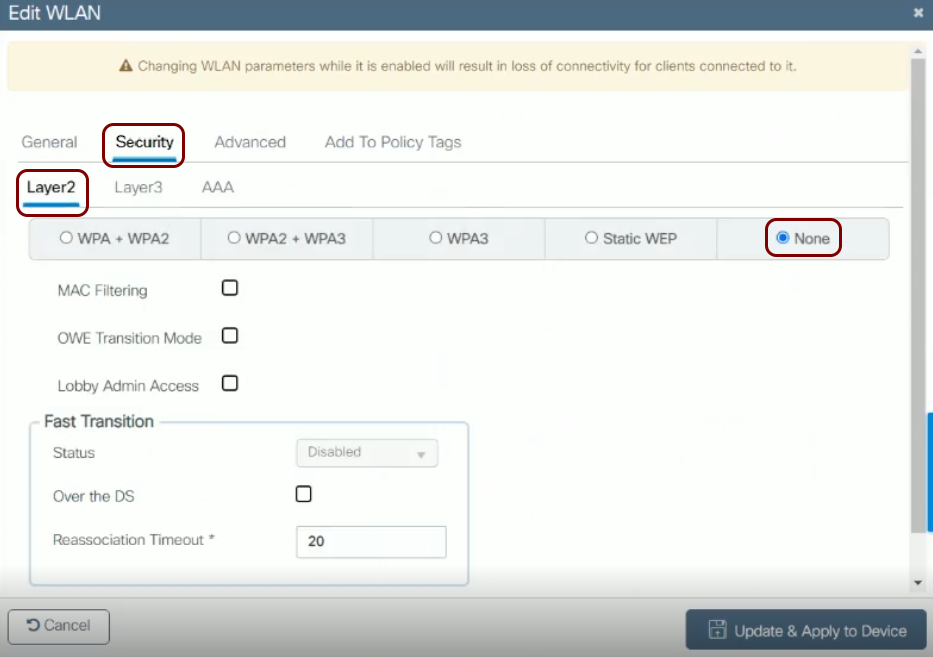
Cisco Catalyst 9800 Wireless LAN Controller (IOS-XE)
Before you begin configuring your wireless controller, you must:
-
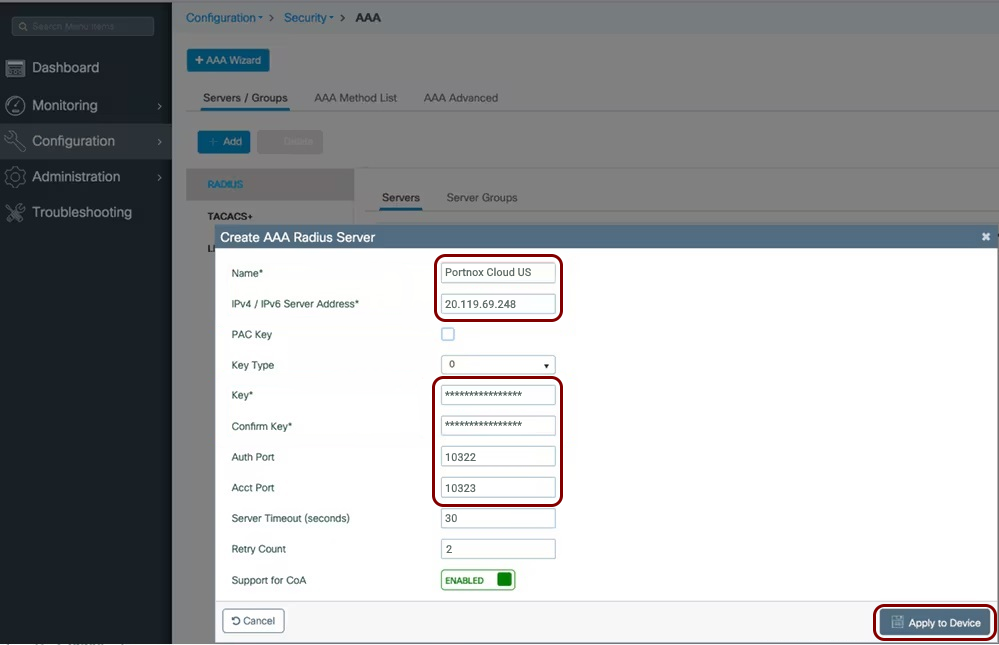
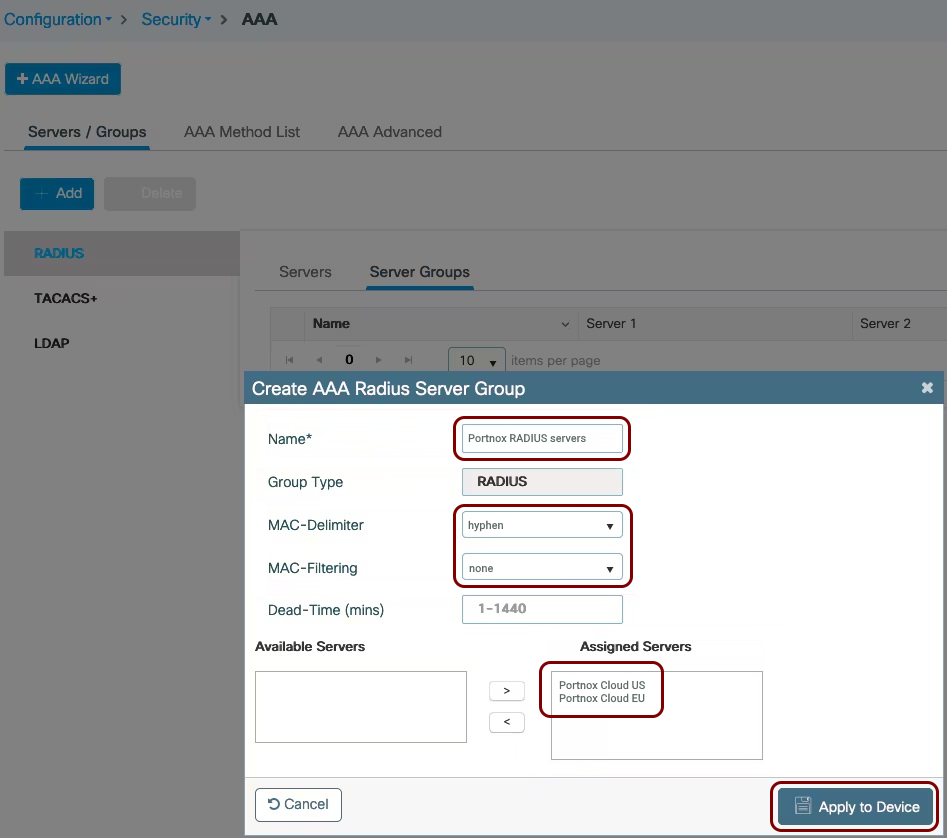
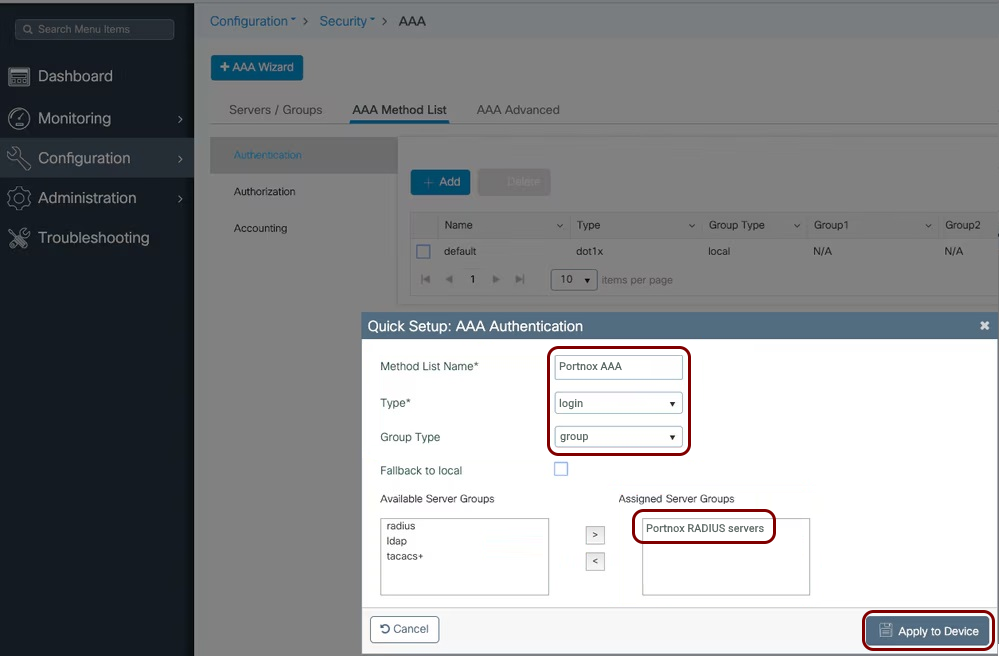
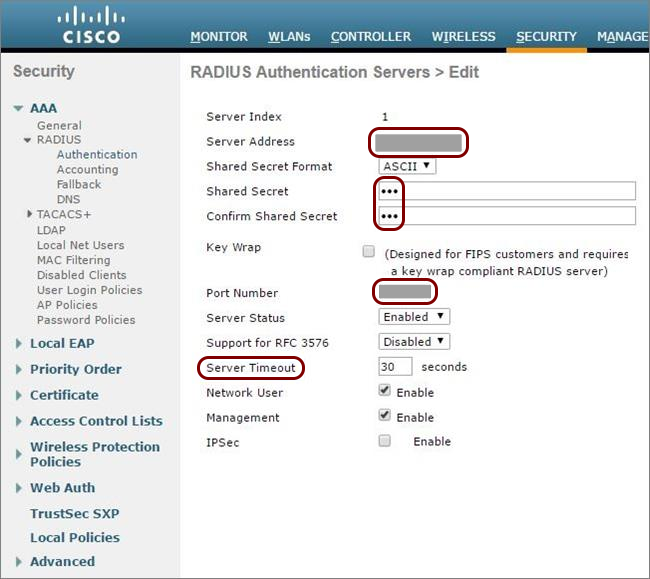
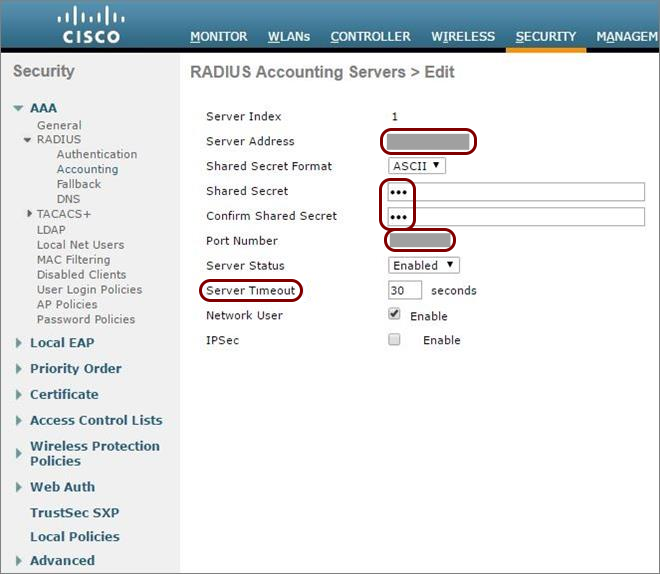
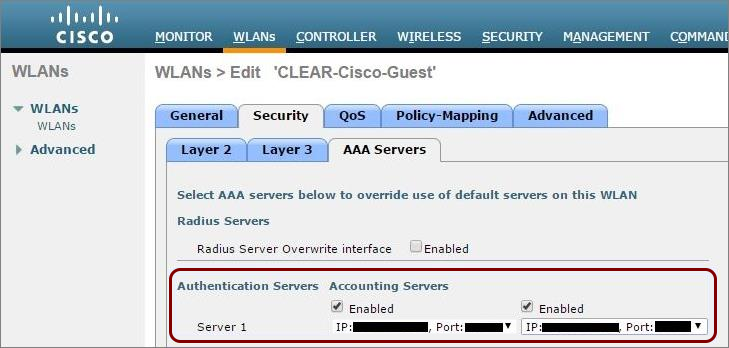
Create Cloud RADIUS servers and note down the following values: Cloud RADIUS IP, Authentication port, Accounting port, and Shared Secret.
-
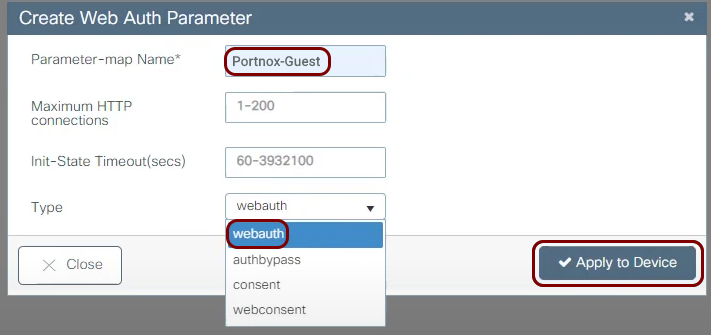
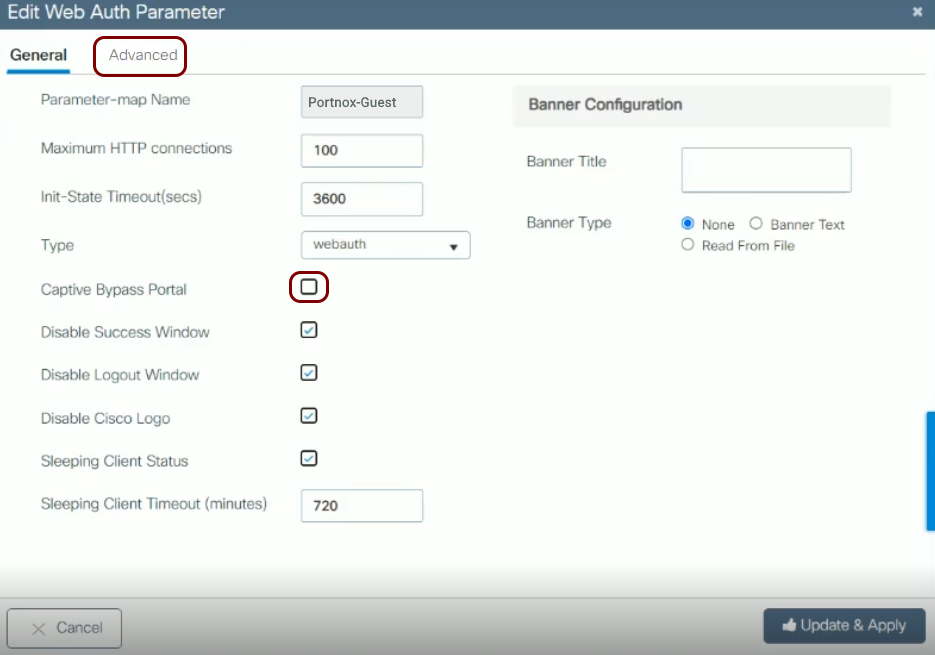
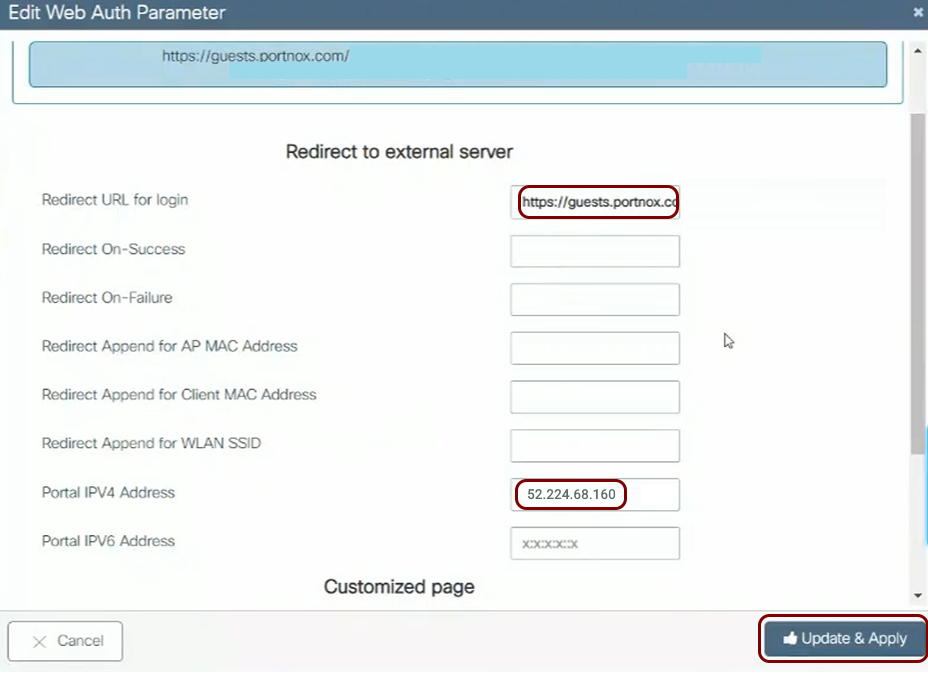
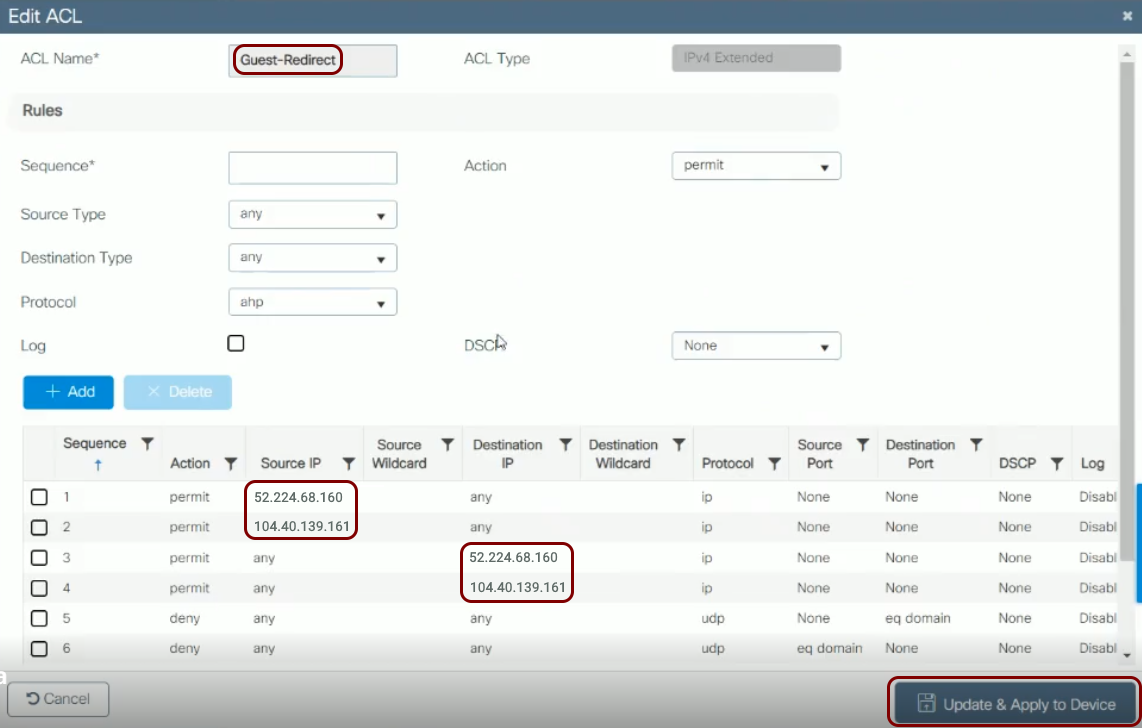
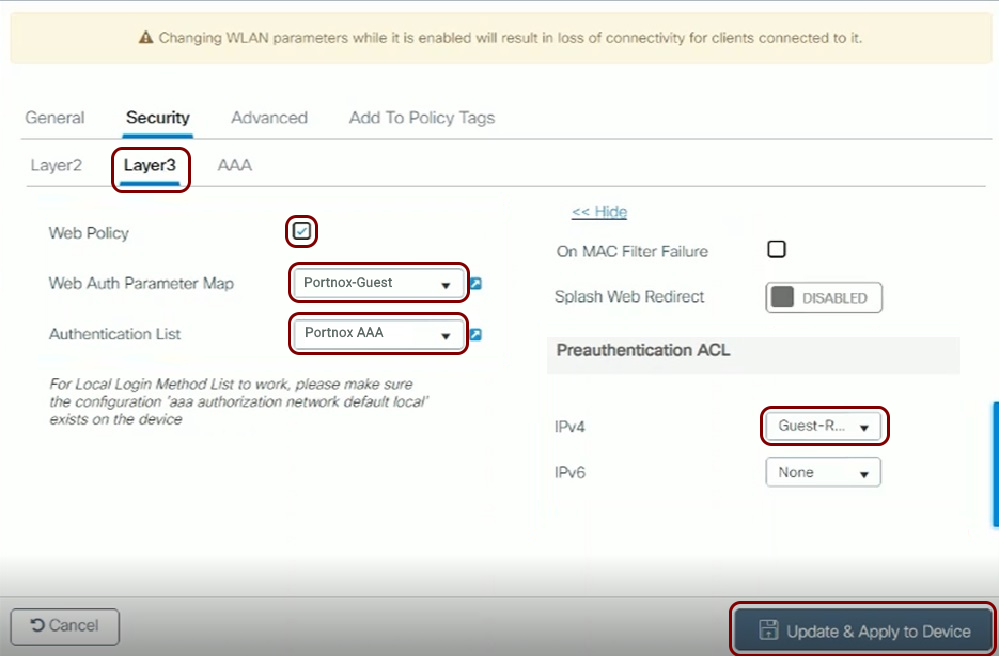
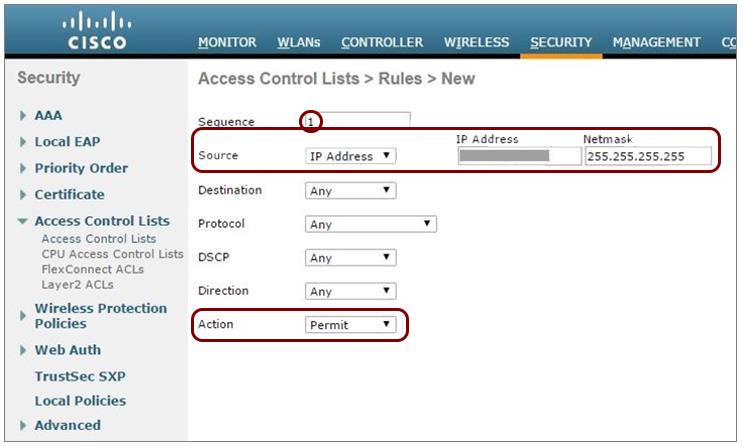
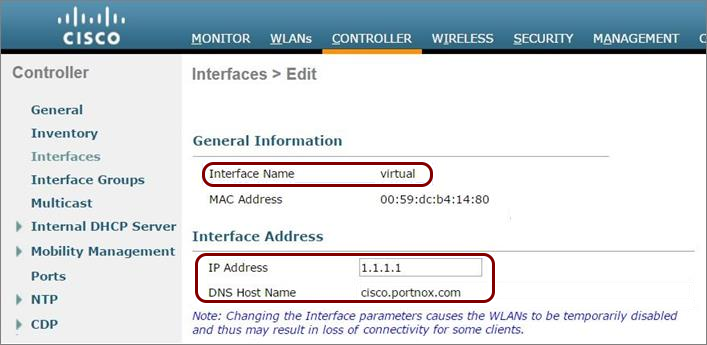
Configure the guest network in Portnox Cloud and note down the values of the fields: IP (for walled garden) and Captive Portal URL.
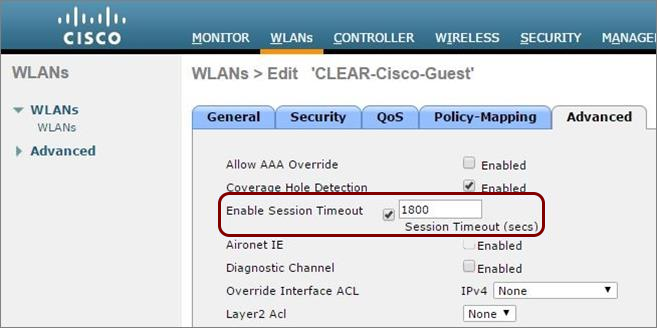
Cisco AireOS Wireless LAN Controllers
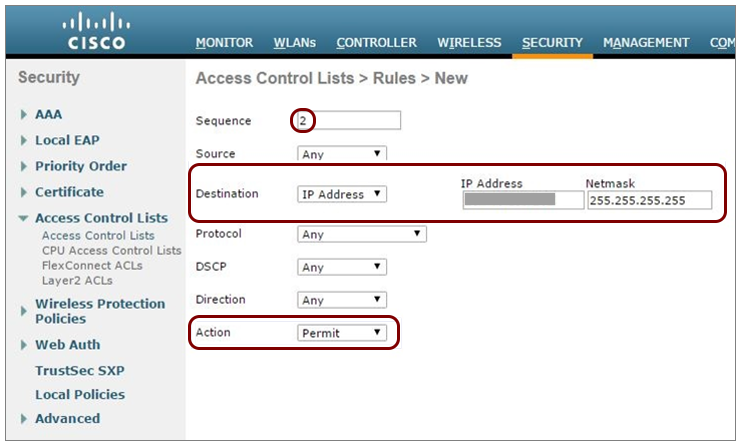
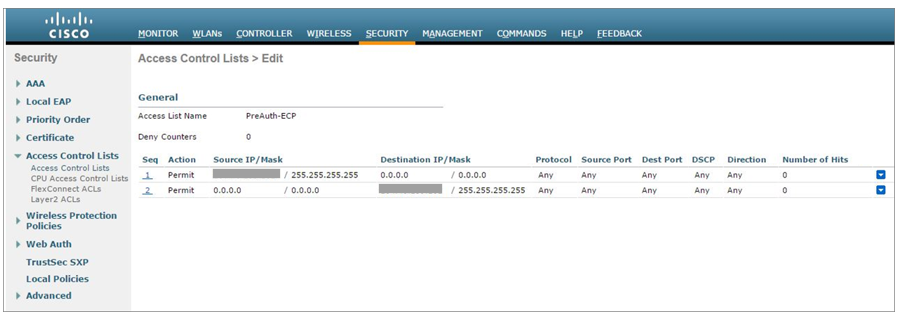
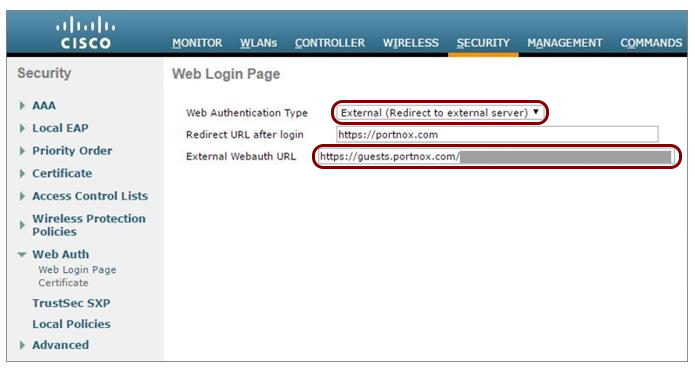
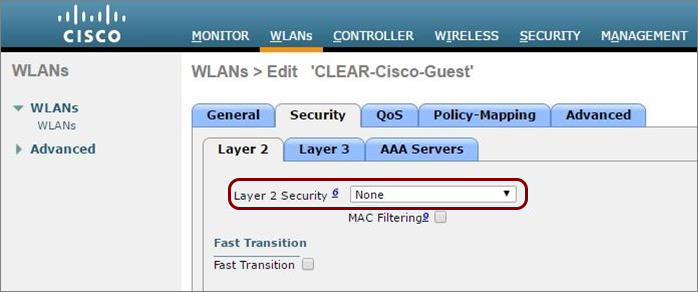
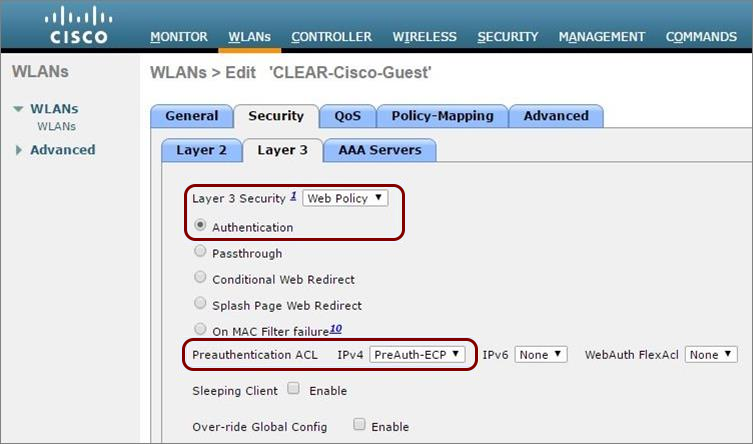
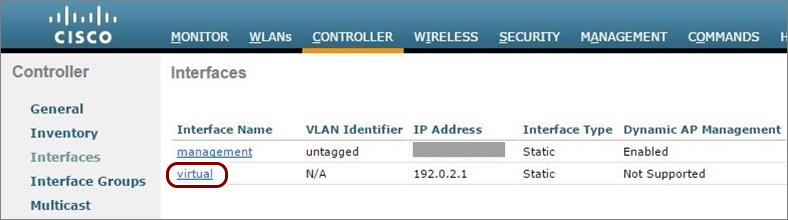
Before you begin configuring your access point, you must configure the guest network in Portnox Cloud and note down the values of the fields: IP (for walled garden) and Captive Portal URL.