Integrate with Entra ID using manual provisioning
In this topic, you will continue Portnox™ Cloud integration with Entra ID using the manual provisioning method.
This task is a continuation of the following task: Integrate with Microsoft Entra ID.
You must complete the first steps in the previous task to continue with this one.
-
In the Azure Directory Applications provisioning mode step, you selected the
Manual option and clicked on the Start Integration button.

- In another browser tab, open your Azure Portal dashboard.
-
In the Azure Portal main menu, click on the Microsoft Entra ID option.
You can access the main menu by clicking on the icon in the top left corner of the Azure Portal.
-
In the left-hand menu, click on the App registrations option.
-
In the top menu of the Azure Portal App registrations screen, click on the New
registration option.

-
In the Register an application pane, enter a name for the application and click on the
Register button at the bottom of the page.
 In this example, we used the name Portnox Cloud, but you can use any name you like.
In this example, we used the name Portnox Cloud, but you can use any name you like. -
In the left-hand menu of your application screen, click on the Certificates & secrets
option.
-
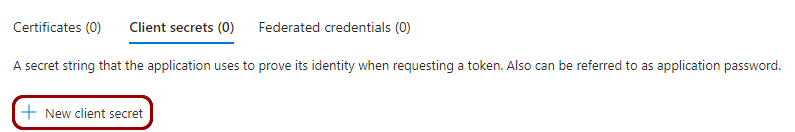
In the right-hand side pane of the Certificates & secrets screen, click on the New
client secret option.
-
In the Add a client secret pane, add an optional Description and select
expiration time in the Expires field. Then, click on the Add button on the
bottom of the pane.
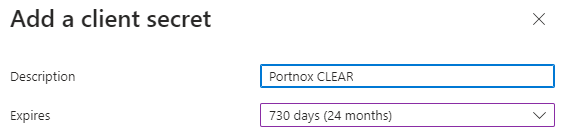
We recommend choosing the longest available expiration date (24 months) or a custom expiration date, so you don’t have to revisit this configuration to generate new secrets.
-
In the right-hand side pane of the Certificates & secrets screen, click on the copy icon next
to the newly added secret.
 Important: Make sure to copy the value, not the ID. You will not be able to copy this secret later. You can also save the value in a temporary text file and enter it in Portnox Cloud later.
Important: Make sure to copy the value, not the ID. You will not be able to copy this secret later. You can also save the value in a temporary text file and enter it in Portnox Cloud later. -
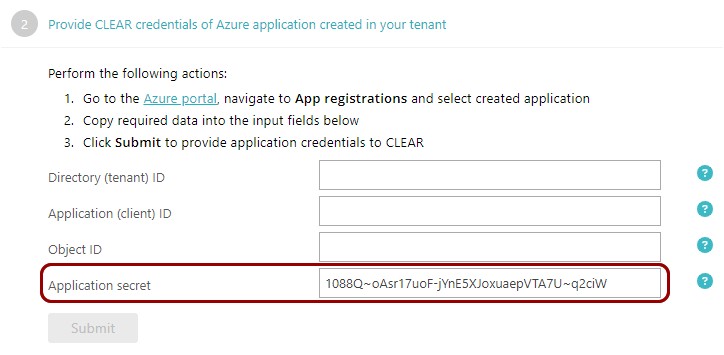
Go back to the Portnox Cloud screen on another browser tab. Paste the copied secret into the Application
secret field.
-
Go back to the Azure Portal and in the left-hand menu of your application screen, click on the API
permissions option.

-
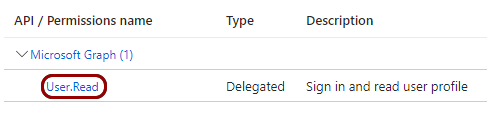
In the right-hand side pane of the API permissions screen, click on the default permission.
-
In the default permission pane, click on the Remove permission option. Confirm your choice by
clicking on the Yes, remove button.

-
In the right-hand side pane of the API permissions screen, click on the Add a
permission option.
-
In the Request API permissions pane, click on the Microsoft Graph
tile.

-
In the Request API permissions pane, click on the Delegated permissions
tile.

-
In the Request API permissions pane, type User.Read.All in the
Select permissions field, expand the User section below, and click on
the User.Read.All checkbox. Then, click on the Add permissions button in
the bottom of the pane.

-
In the right-hand side pane of the API permissions screen, click on the Add a
permission option.

-
In the Request API permissions pane, click on the Microsoft Graph
tile.

-
In the Request API permissions pane, click on the Application permissions
tile.

- In the Request API permissions pane, type User.Read.All in the Select permissions field, expand the User section below, and click on the User.Read.All checkbox.
- In the Request API permissions pane, type Group.Read.All in the Select permissions field, expand the Group section below, and click on the Group.Read.All checkbox.
- In the Request API permissions pane, type Domain.Read.All in the Select permissions field, expand the Domain section below, and click on the Domain.Read.All checkbox.
- In the Request API permissions pane, type Device.Read.All in the Select permissions field, expand the Device section below, and click on the Device.Read.All checkbox.
- Click on the Add permissions button at the bottom of the pane.
-
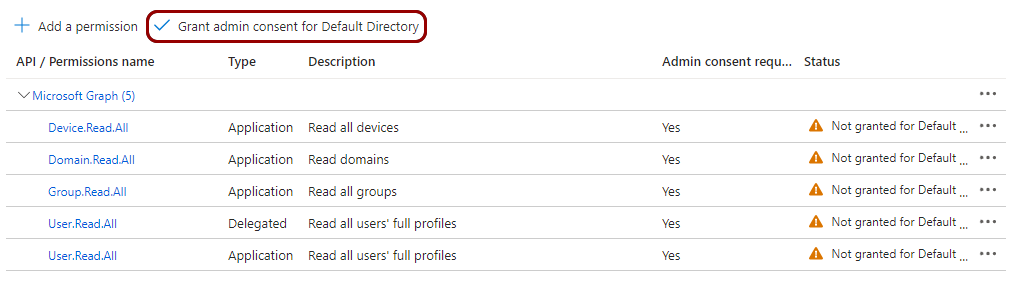
In the right-hand side pane of the API permissions screen, click on the Grant admin
consent for Default Directory option. Click on the Yes button in the confirmation
window.
-
In the left-hand menu of your application screen, click on the Authentication option.
-
In the right-hand side pane of the Authentication screen, click on the Yes
button in the Allow public client flows section towards the bottom of the page. Then, click on
the Save button in the confirmation window.

-
In the left-hand menu of your application screen, click on the Overview option.

-
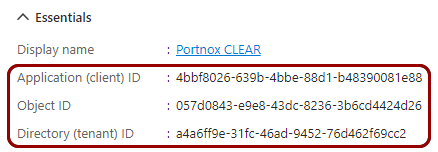
Copy the following information from the Essentials section in the right-hand side pane:
Application (client) ID, Object ID, Directory (tenant)
ID.
You can save this information temporarily in a text file or copy it directly.
-
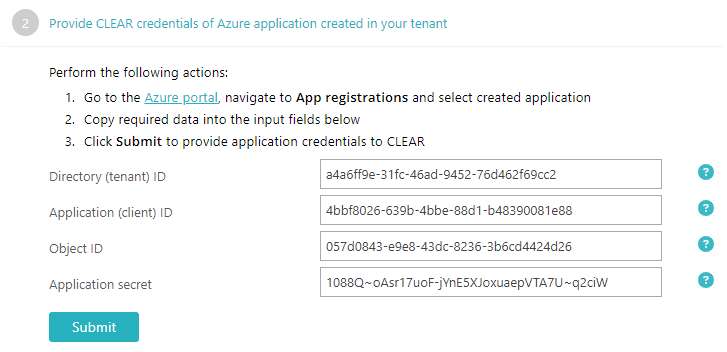
Go back to the Portnox Cloud screen on another browser tab. Paste the data copied in the previous step into their
respective fields in Cloud and then click on the Submit button.
-
Select the domains managed by Entra ID that you want to associate with your Portnox Cloud organization.
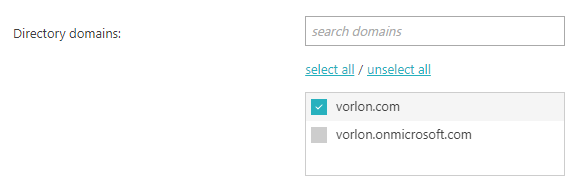
- If your Active Directory manages many domains you can use the search domains field to search for a string that matches a domain name. The list of domains below the search field will be updated as you type.
- Click on the select all or unselect all link to select or deselect all domains in the list.
- Click checkboxes next to domains to select or deselect them individually.
- After you select the domains, click on the Save Domains button to save your selection.
- Optional: If you want to edit the options of your Entra ID integration or configure additional options, read the following topic: Edit your Entra ID integration.
Result: Your Entra ID integration is now active. You can authenticate devices on your network using Entra ID.
