Guest access – Aruba
In this topic, you will learn how to configure Aruba wireless controllers to work together with the Portnox™ Cloud captive portal for guest user authentication.
Aruba Central
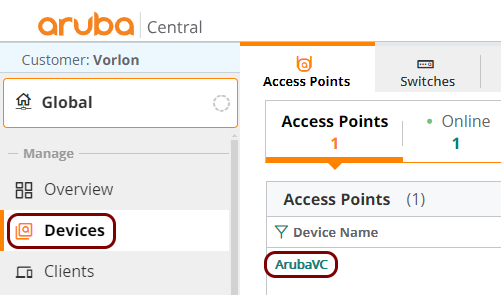
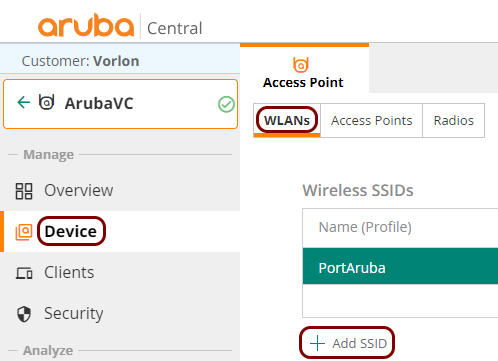
In this section, you will learn how to configure access points managed using Aruba Central to work together with the Portnox™ Cloud captive portal for guest user authentication.
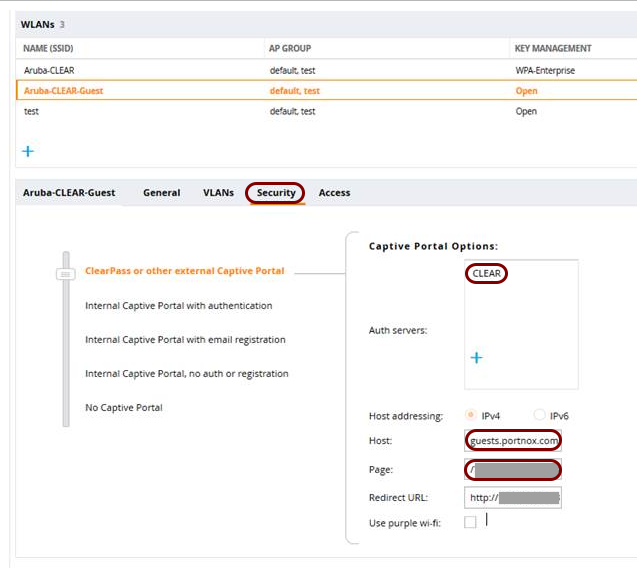
Aruba Mobility Controller
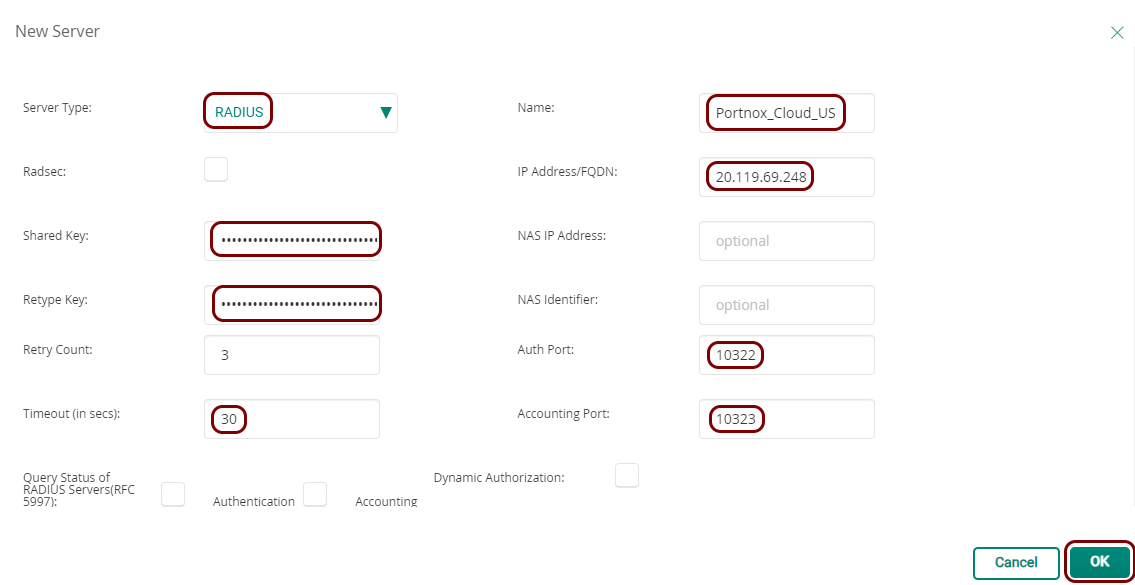
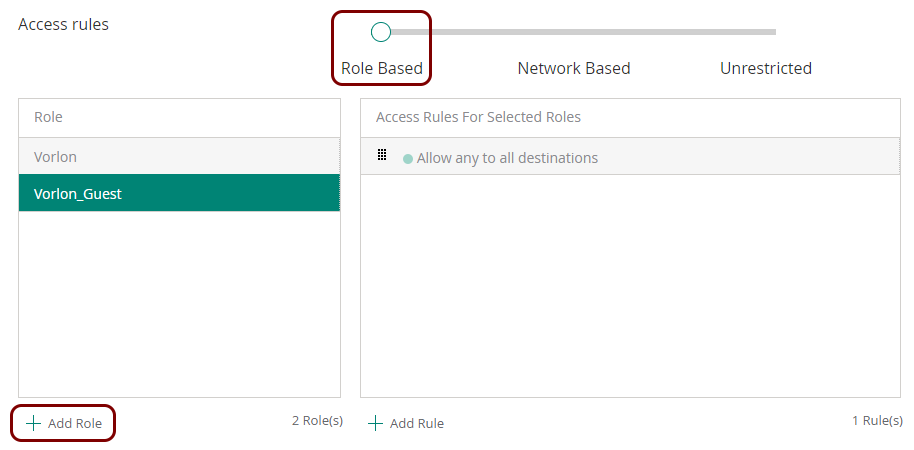
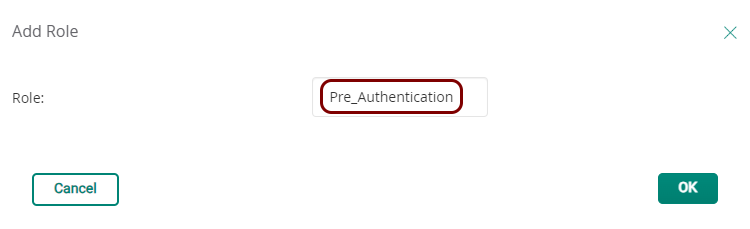
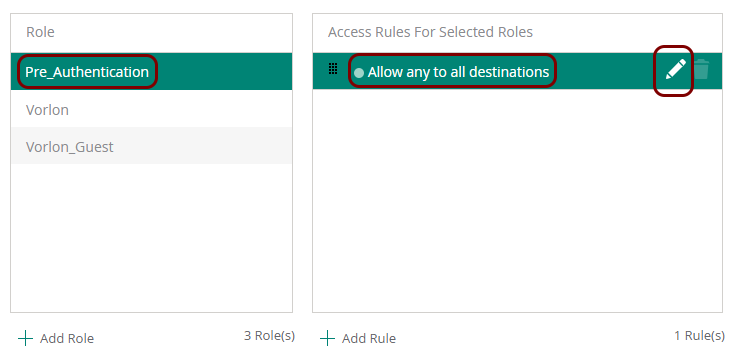
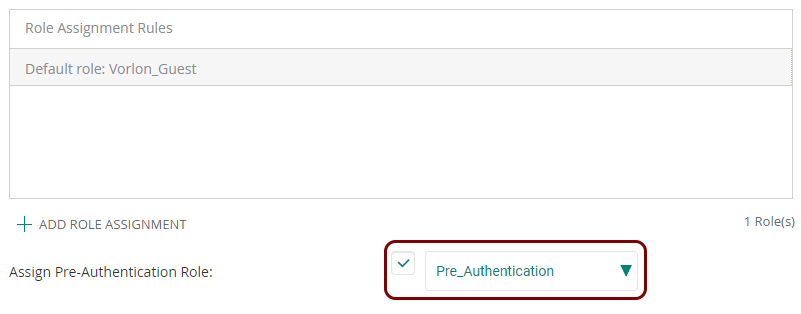
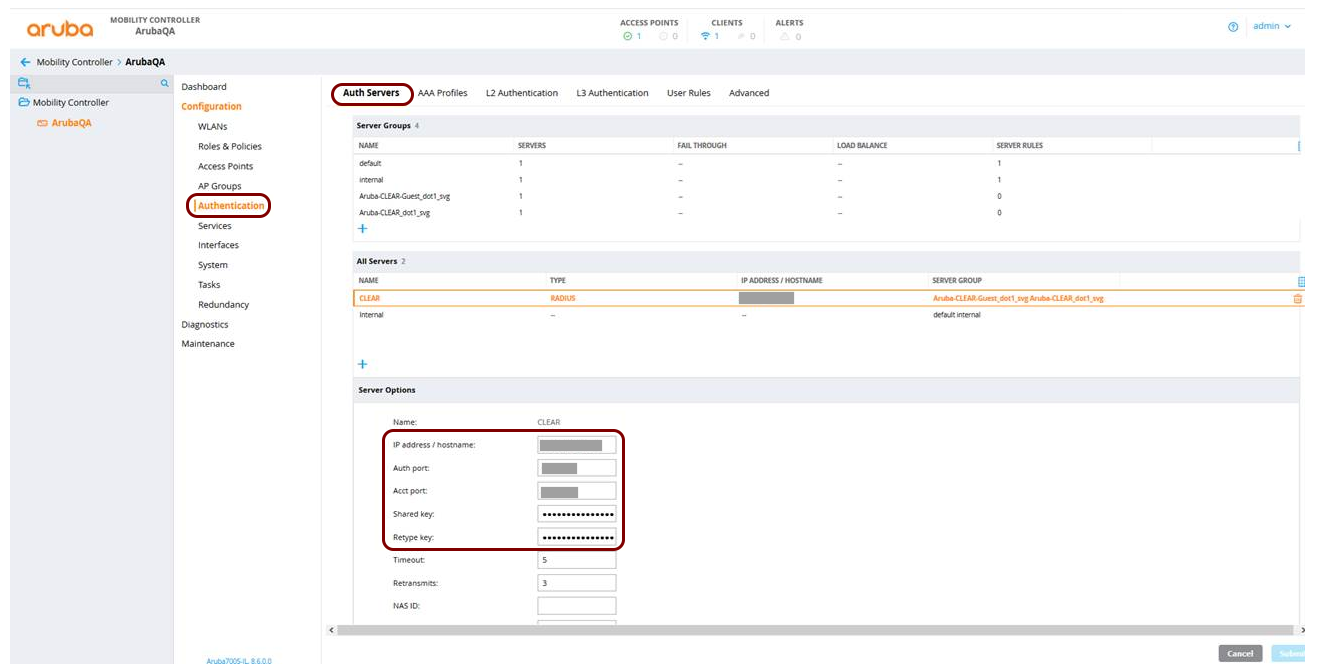
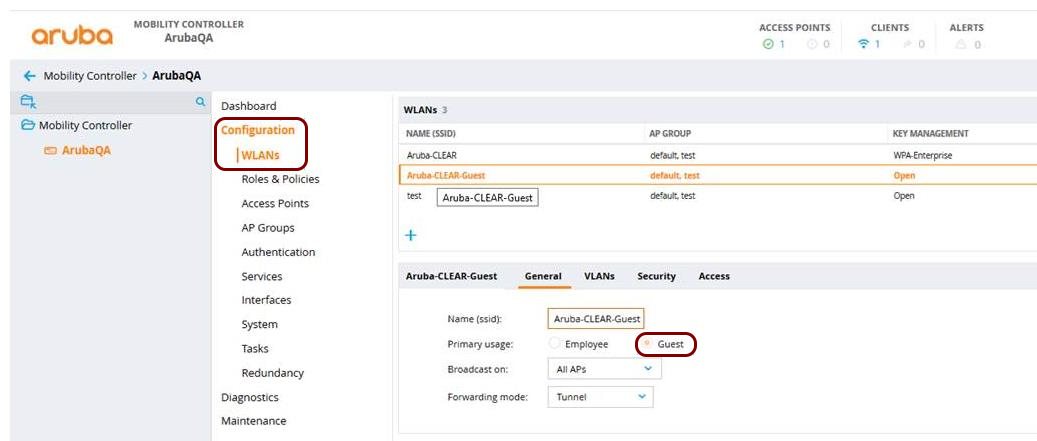
In this section, you will learn how to configure an Aruba Mobility Controller to work together with the Portnox™ Cloud captive portal for guest user authentication.
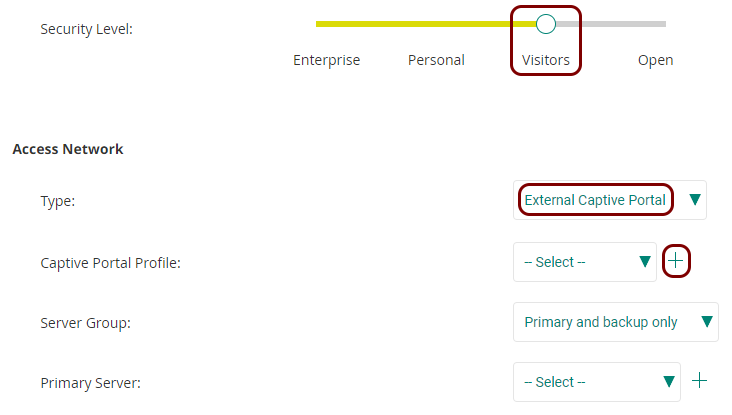
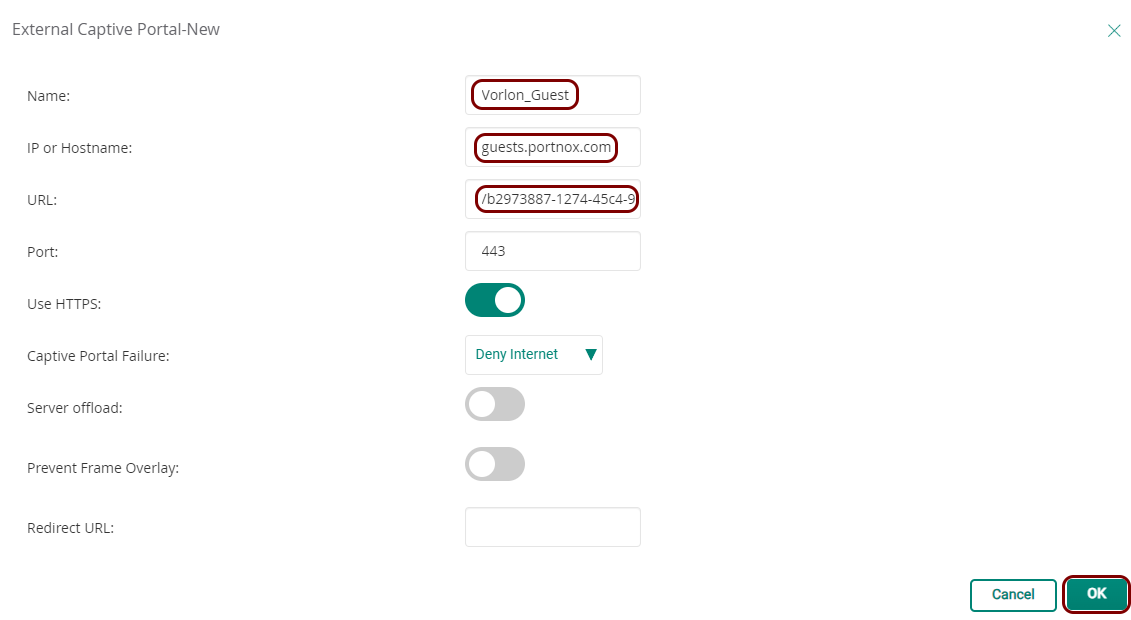
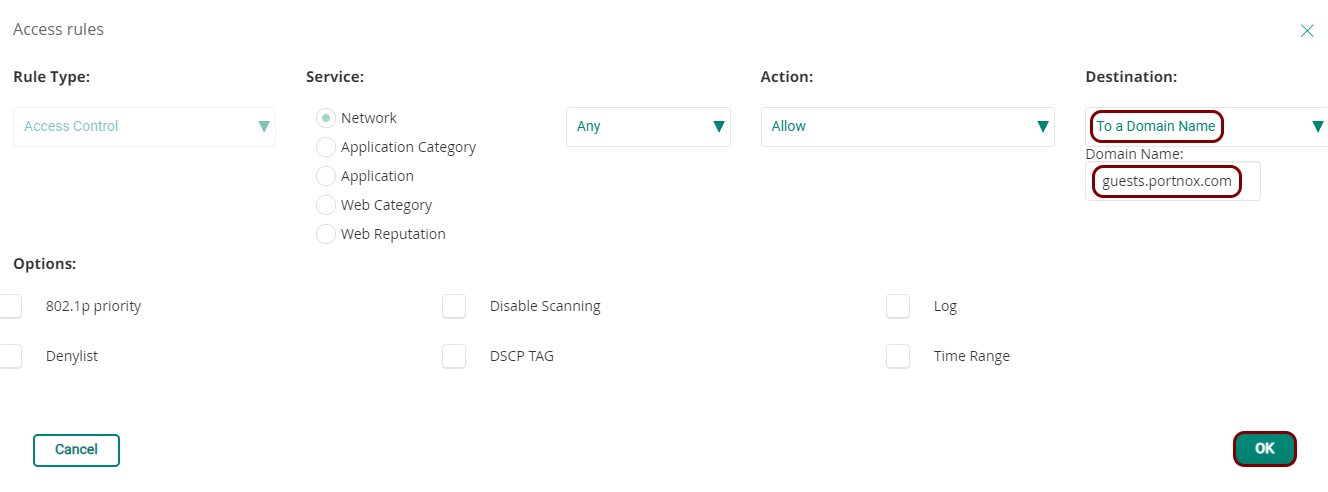
Before you begin configuring your access point, you must configure the guest network in Portnox Cloud and note down the values of the fields: IP (for walled garden) and Captive Portal URL.