Certificate fragmentation issues
In this topic, you will learn how to address fragmentation issues when onboarding devices onto a network managed by Portnox™ Cloud using certificates.
If certificate-based authentication does not work but credential-based authentication works, check if the packets are being fragmented by firewalls/routers between the NAS and the RADIUS server. You can do this by obtaining a packet capture of the communication between the NAS device and the Cloud RADIUS service.
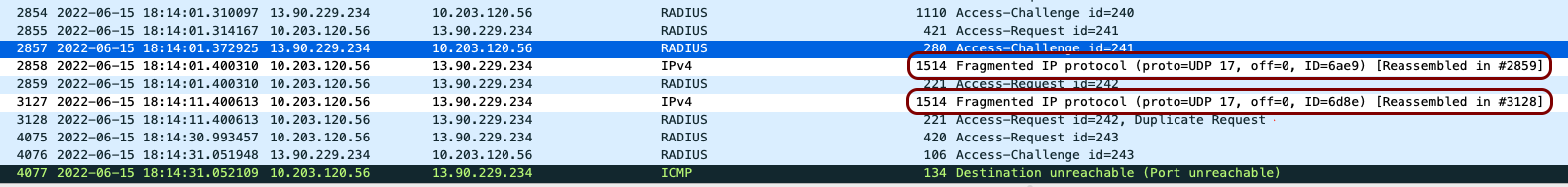
Fragmentation happens because Ethernet frames have a maximum size, called the Maximum Transmission Unit (MTU), which is limited to 1500 bytes. Certificates, however, are sometimes much larger than this limit. When a certificate is too big to fit within a single frame, the router or firewall will try to split it into smaller pieces, sending the data across multiple frames. Unfortunately, when the certificate is in separate pieces, the smaller fragments are often eliminated by DDoS protection mechanisms, so the server isn’t able to put them back together correctly and doesn’t recognize the certificate as valid.
The following are potential options to resolve such fragmentation problems:
- Reduce the key size of the certificate and eliminate any unnecessary information from the certificate (for example, OCSP or CRL information). If you remove any unnecessary information from the certificate, it may be small enough to fit in a single frame.
- Reduce the key size of your certificates, for example, set it to 1024. This value is configured when generating the certificate, for example, in your SCEP profiles if you use Intune, Jamf, or another UEM platform to generate your certificates, and it’s often set to be 2048 or 4096. This will also reduce the packet size, so certificates will fit in a single frame.
- Use ECC encryption to generate your certificates, not the default RSA, if possible. ECC is better, stronger, and much more efficient (requires fewer bytes) than RSA, so resultant certificates will be smaller and will be more likely to fit within a single frame even with extra information.
- Use RadSec (secure RADIUS) to communicate to Cloud RADIUS servers. RadSec is immune to frame size issues. Unfortunately, while RadSec is quite common, it may be unsupported by some NAS devices, so check manufacturer information for your model.
- Install a local RADIUS server and use it as a proxy to the Cloud RADIUS servers. The local RADIUS server communicates with Cloud RADIUS servers using different protocols so the frame size problem does not apply – 802.1X communication happens only within your network.
- For Palo Alto switches, try this solution.
- For Cisco Internet SD-WAN connections, packet reassembly might cause the issue, which is resolved by issuing the following command on the interface level: no ip virtual-reassembly-out.
- For Cisco switches also consider disabling jumbo frames.
- For Meraki access points, consider activating the Dashboard RADIUS proxy option in the SSID configuration.
