Add Microsoft Entra ID as a SAML identity provider for Zero Trust Network Access
In this topic, you will find instructions on how to add Microsoft Entra ID as a SAML identity provider for Portnox™ Zero Trust Network Access.
Prerequisites:
-
You must first integrate your Portnox Cloud instance with your Microsoft Entra ID repository (Azure Active Directory) as an authentication provider. For more information, see the following topic: Integrate with Microsoft Entra ID.
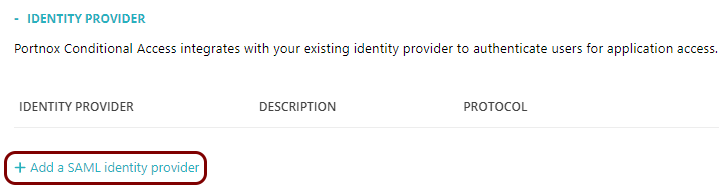
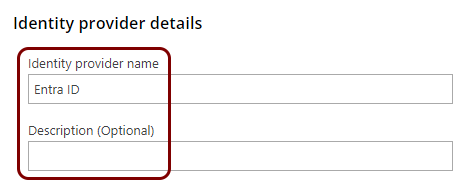
Create a new identity provider configuration in Portnox Cloud
In this section, you will create a new SAML identity provider configuration in Portnox Cloud
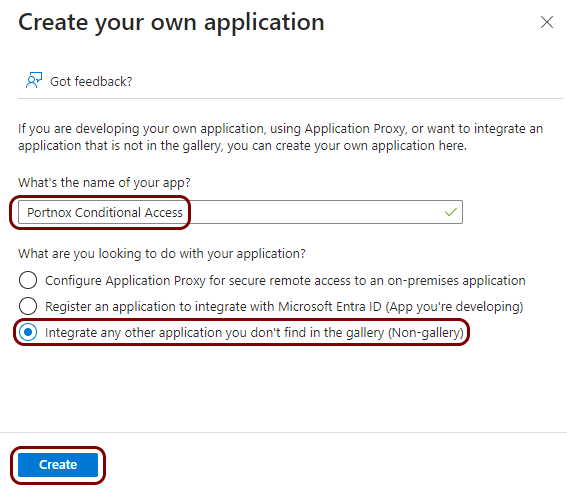
Create a new identity Entra ID application
In this section, you will access the Microsoft Azure administrative interface and use it to create a new Entra ID application that will handle integration with Portnox Cloud.
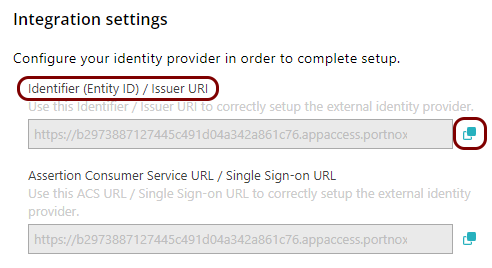
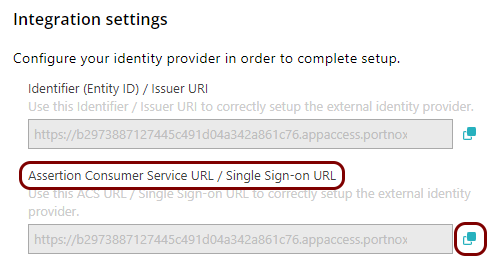
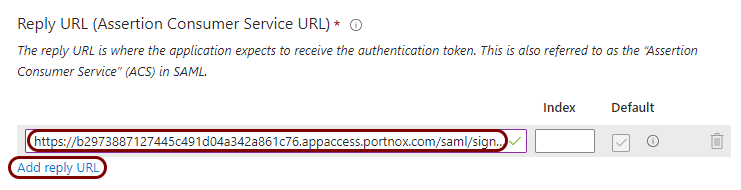
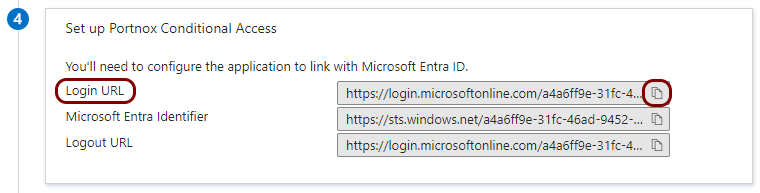
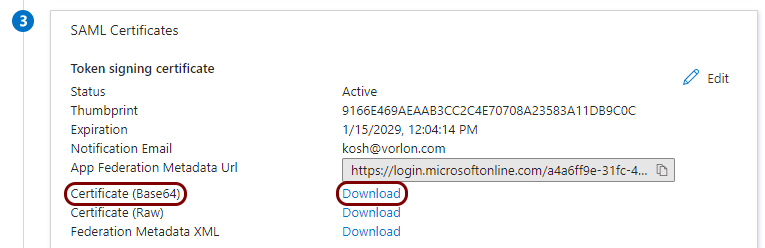
Copy configuration values from the Portnox tab to the Azure tab
In this section, you will copy the values displayed by Portnox Cloud and paste them in the relevant fields in the Entra ID application setup section.
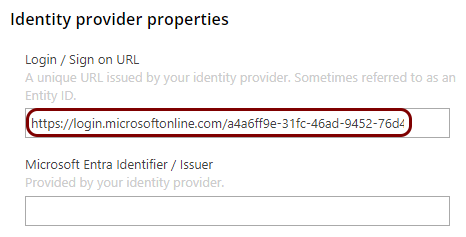
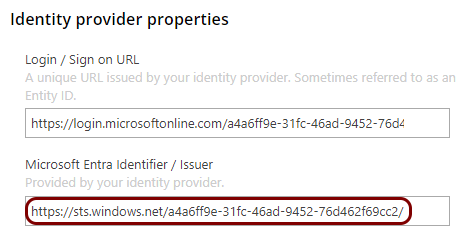
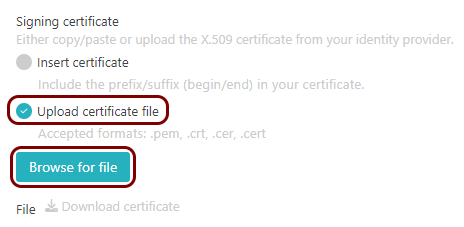
Copy configuration values from the Azure tab to the Portnox tab
In this section, you will copy the values displayed by the Entra ID application setup section and paste them in the relevant fields in Portnox Cloud.
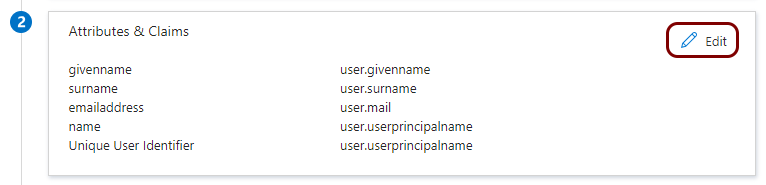
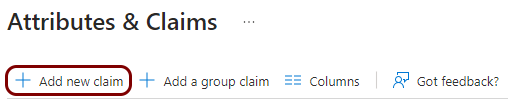
Add attribute mapping
In this section, you will add attribute mapping in Azure. This mapping is needed by some applications to correctly map users between the identity provider and the application.
Finalize the configuration
In this section, you will finalize the configuration in the Portnox Cloud and in Azure.
-
Finalize the configuration in the Portnox tab.
-
Finalize the configuration in the Azure tab.
Result: You have added Entra ID as an identity provider for Portnox Zero Trust Network Access.
After configuring the identity provider, check your access privileges in Entra ID to make sure that your users can access this application. You can also click on the Test button in Step 5 to test your configuration.
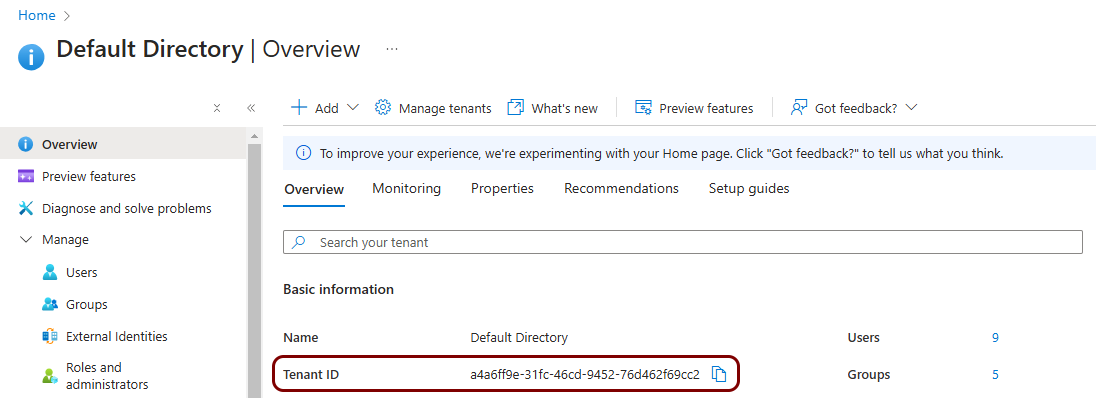
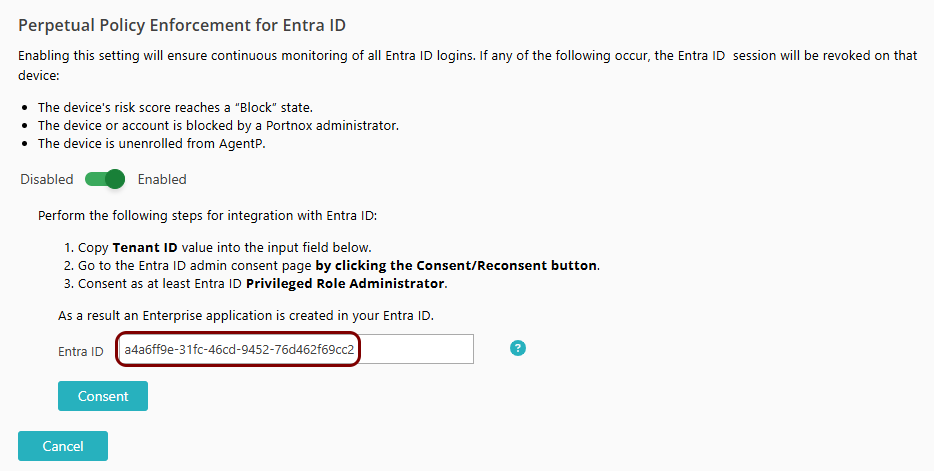
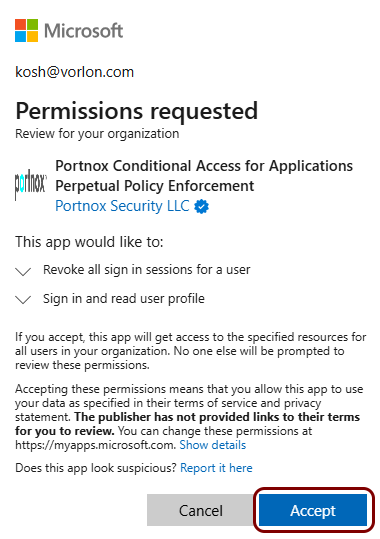
Perpetual policy enforcement for Entra ID
Optionally, in this section, you will turn on the perpetual policy enforcement option for your Entra ID identity provider.
Without perpetual policy enforcement, if a device is no longer compliant or is manually blocked, it retains access to applications until the next time the user is asked to log in to Entra ID.
If you turn on the perpetual policy enforcement option, Entra ID will revoke application access if the device is blocked, if AgentP was uninstalled, or if the device risk score reached the Block level. This way, the user immediately loses access to the application if there is risk. They user may gain access again after remediating the cause of the risk.
Result: Portnox Cloud installs an application in your Azure tenant called Portnox Zero Trust Network Access Perpetual Policy Enforcement, which provides perpetual policy enforcement functionality.