Create an account
In this topic, you will learn how to create an account in Portnox™ Cloud. You can create accounts manually for IoT devices, external contractors, and more.
To understand what are accounts in Portnox Cloud and how they work together with groups and policies, read the following topic: What are accounts in Portnox Cloud?.
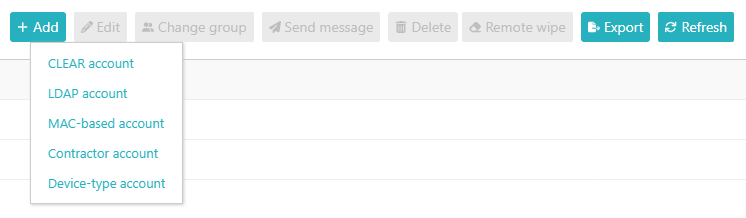
Create a Portnox account
Use this type of account if you want to use Portnox Cloud as your user repository.
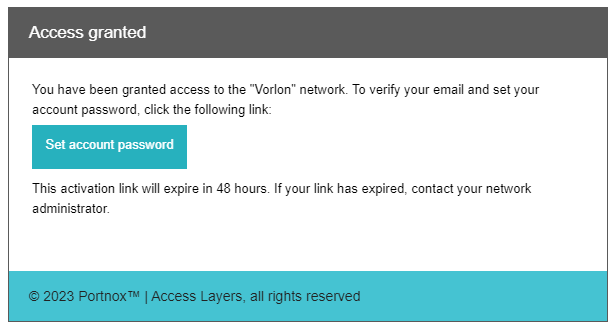
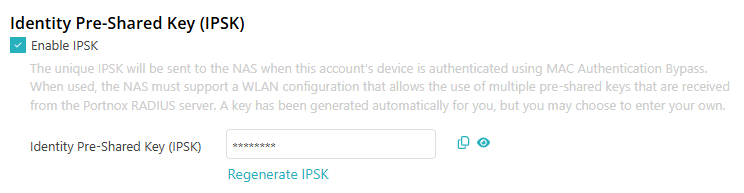
Result: The user will be able to access Portnox Cloud using their email address and the password that they set.
Create a LDAP account
Use this type of account if you want to add individual users from an authentication repository that you configured earlier.
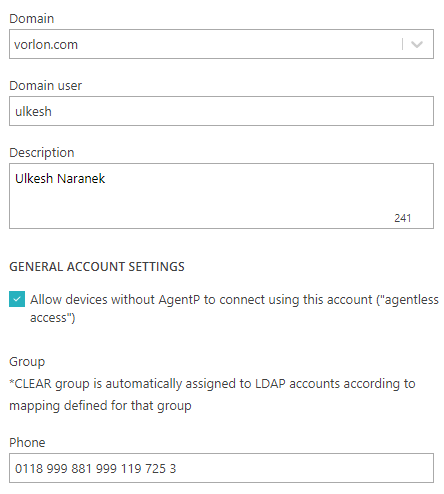
Result: The user will be able to access Portnox Cloud using their credentials from the external authentication repository.
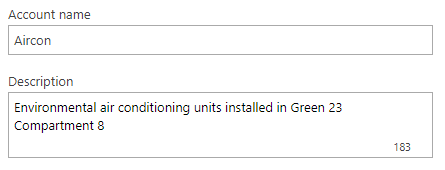
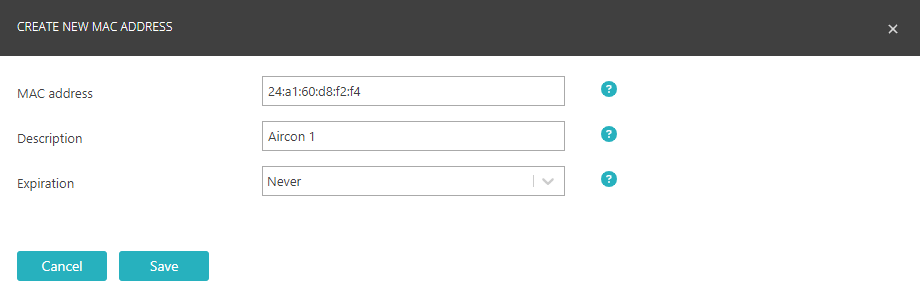
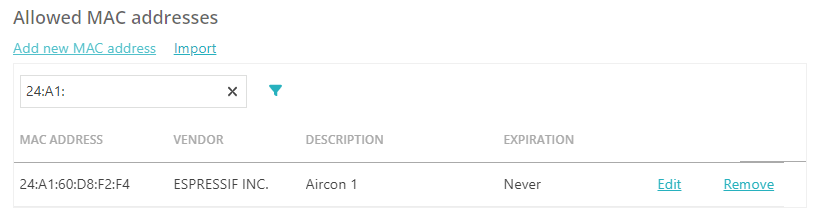
Create a MAC-based account
Use this type of account if you want to give network access to devices that do not work with the 802.1X protocol.
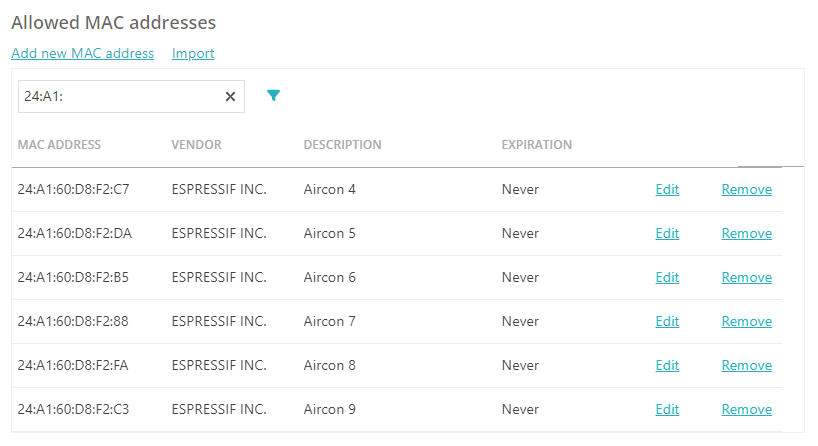
A MAC-based account can represent a single device or a group of devices. For better security and control, we recommend creating accounts for individual devices or small groups of closely related devices.
- You add a MAC address to a MAB account – the day when you do this counts as day 1.
- The day counter increases every day at midnight tenant-time,
- Any time the device with the MAC address authenticates, the counter resets to 1.
- The moment that the counter reaches the configured limit, the MAC address is removed from the MAB account.
- The device with the MAC address is no longer in the MAB account so it cannot authenticate.
Create a contractor account
Use this type of account if you want to give network access to users that do not belong to the organization.
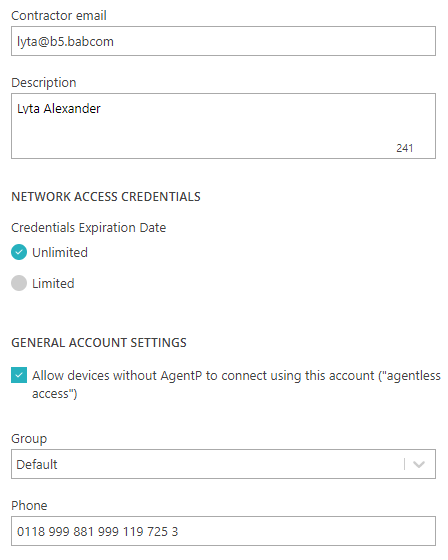
Result: The contractor will be able to access Portnox Cloud using their email address and the password that they set.
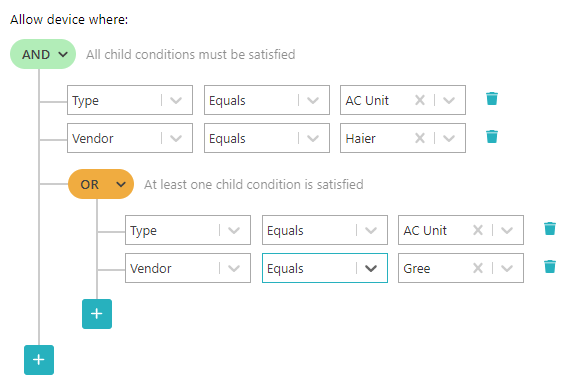
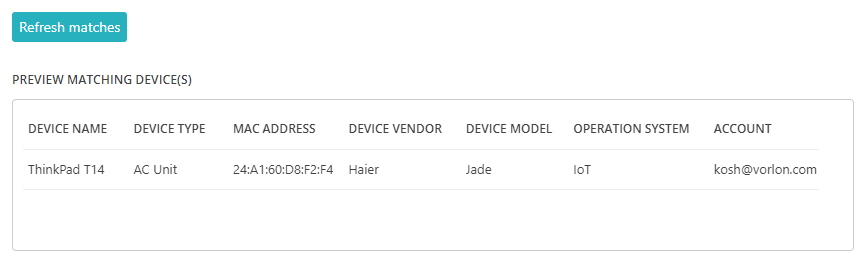
Create a device-type account
Use this type of account if you want to give network access to a large number of similar devices that do not work with the 802.1X protocol.
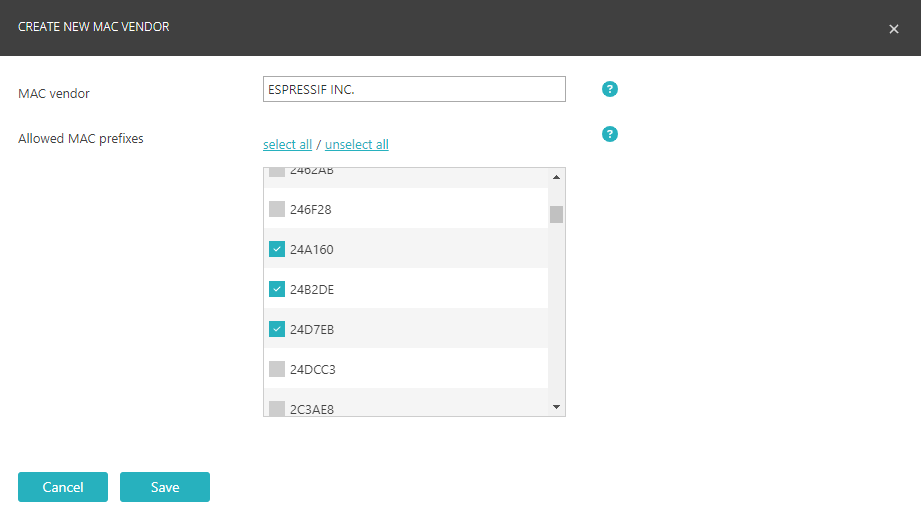
Device-type accounts let you define rules based on device properties such as type, vendor, model, and operating system. Similar to MAC-based addresses, they are meant for devices that cannot authenticate using the 802.1X protocol, such as IoT devices.