Deploy the local TACACS+ server container in Google Cloud Platform (GCP)
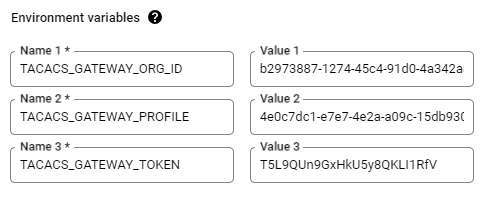
In this topic, you will learn how to deploy the Portnox™ Cloud local TACACS+ server container in Google Cloud Platform (GCP) using the Google Compute Engine (GCE).
Read the following important information before you begin:
-
You can deploy containers in Google Cloud Platform using either the Compute Engine (GCE), Cloud Run, or the Kubernetes Engine (GKE). We are only describing the process for GCE due to its simplicity and applicability.
The weak spot of GCE is the inability to directly store Docker tokens as secrets. The major disadvantage of Cloud Run is the inability to reserve a fixed IP address (requires the use of Google Load Balancer). The downside of using GKE is its complexity and the necessity to use the console.
For Google documentation on deploying containers with Google Cloud Run, see the following Google documentation topic: Deploying container images to Cloud Run.
For Google documentation on deploying containers with GKE, see the following Google documentation topic: Deploying a containerized web application.
-
You cannot place NAS devices behind a NAT because the local TACACS+ server uses the source IP address of the connection, and with a NAT in place, that address would be the same for several NAS devices.
Create a new VM instance in GCE
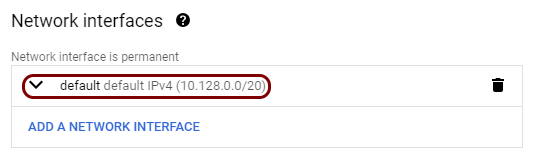
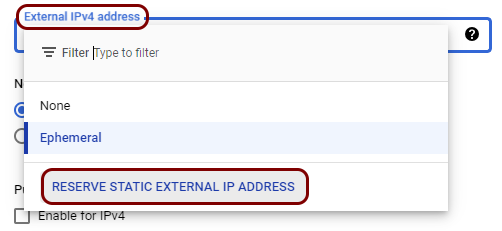
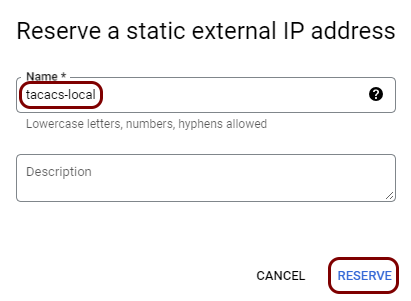
In this section, you will create a new virtual machine instance in GCE, deploy the Portnox Docker container, and assign a static, external IP address to the instance.
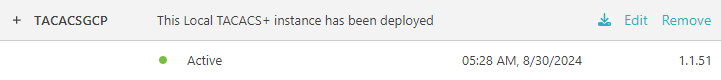
Result: The local TACACS+ container is working correctly and communicating with Portnox Cloud.
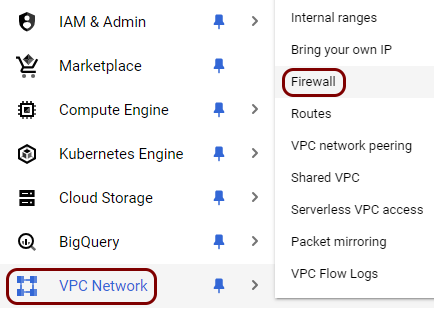
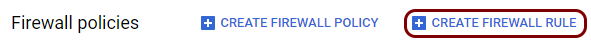
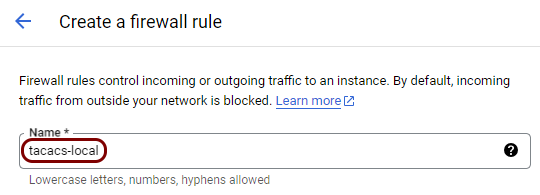
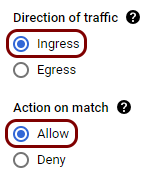
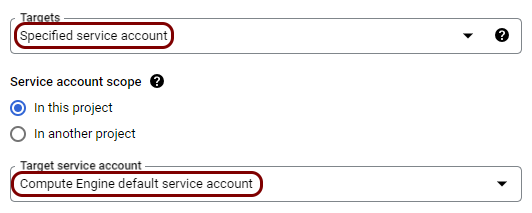
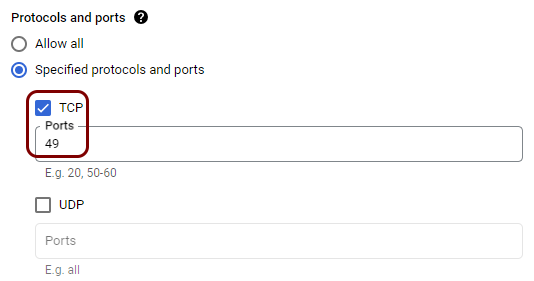
Create firewall rules to allow traffic to the local TACACS+ server
In this section, you will create firewall rules to open the port required by the local TACACS+ server to be reachable for clients.
While the container is running and communicating with the cloud, Google Cloud VM instances by default block access on all ports, so clients cannot use this TACACS+ server yet. You need to configure the Google Cloud firewall to allow TACACS+ traffic to reach the local TACACS+ instance.
Result: The local TACACS+ instance is now able to serve clients.