Deploy the local TACACS+ server container in Microsoft Azure
In this topic, you will learn how to deploy the Portnox™ Cloud local TACACS+ server container in Microsoft Azure using Azure Container Instances.
To deploy the local TACACS+ server Docker container in Azure Container Instances, you must first configure the settings for the local TACACS+ server container and generate environment variables. To do it, go to the following topic: Run the local TACACS+ server in a container.
Read the following important information before you begin:
-
Azure Container Instances are not the only way to deploy the local TACACS+ server container in Azure but it is the easiest way. Other options include Azure Kubernetes, Azure Container Apps, and more. If you choose a different option, please follow relevant Microsoft Azure documentation to deploy your container.
-
In order for the local TACACS+ server container in Azure to be able to communicate with your NAS devices in your local network, you must create a virtual network in Azure and connect it to your local network. Azure offers many ways of achieving this. This topic is beyond the scope of this guide, but you can find useful information in the following Microsoft documentation topics: Create a site-to-site VPN connection in the Azure Portal and Connect an on-premises network to Azure.
-
You cannot place NAS devices behind a NAT because the local TACACS+ server uses the source IP address of the connection, and with a NAT in place, that address would be the same for several NAS devices.
-
If you have multi-factor authentication (MFA) enabled in Azure for your policy, you must allow Portnox Cloud services to bypass MFA by whitelisting the services’ IP addresses. To lean how to do it, see the following topic: Bypass multi-factor authentication in Entra ID.
-
We highly recommend that you create a free Docker Hub account before you begin and use the credentials of that account to pull the Docker image. This is because Docker Hub has limits on the number of anonymous pulls per IP address per hour, and without credentials, you may be unable to pull the image due to those limits being exceeded by others sharing your infrastructure’s external IPs.
-
When you’re using stateless containers and you want to update to a newer version of the Docker image, you need to delete the container and recreate it from scratch with the same parameters.
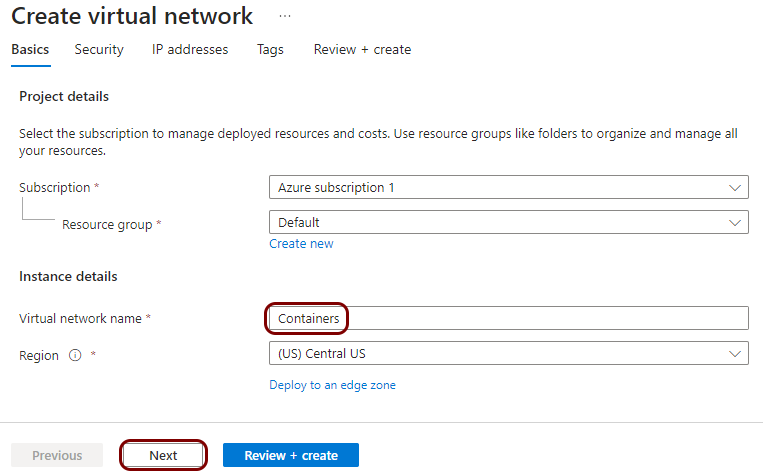
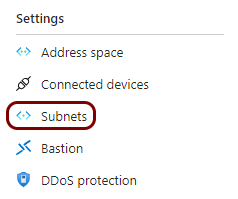
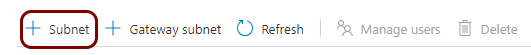
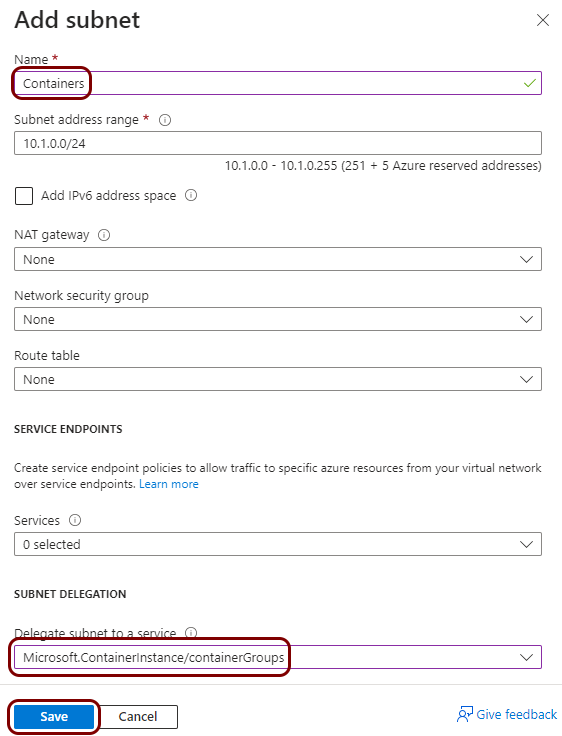
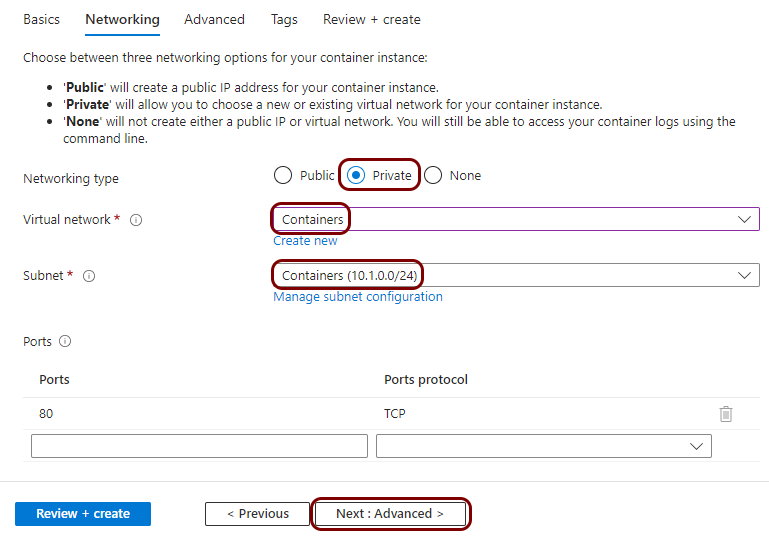
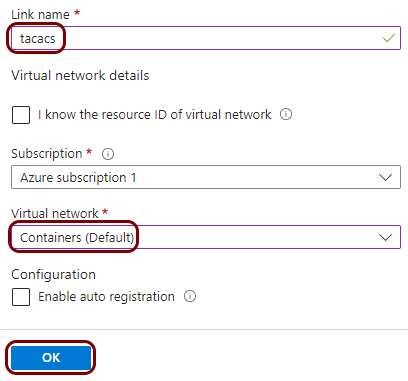
Create a virtual network and subnets
In this section, you will create a virtual network with a subnet for local TACACS+ server containers.
You must deploy the local TACACS+ server container to a subnet that is delegated to Container Instances. This subnet cannot contain other resource types. If you already have a subnet that meets this condition, you can skip this step and choose an existing subnet instead. You can also add a subnet to an existing virtual network instead.
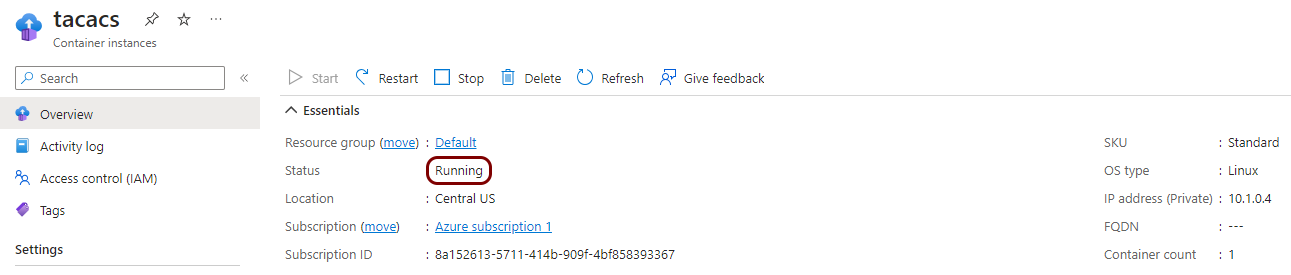
Create a container instance
In this section, you will deploy the local TACACS+ server Docker container to the virtual network created in the previous step.
Result: Your local TACACS+ server is active.
You can check its status in Portnox Cloud, in the section.

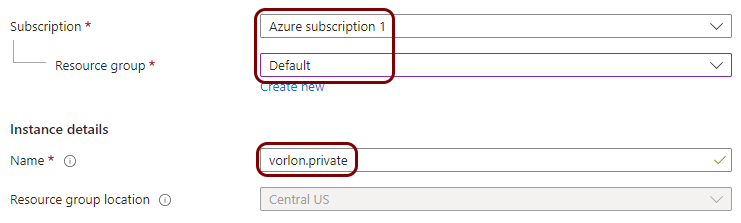
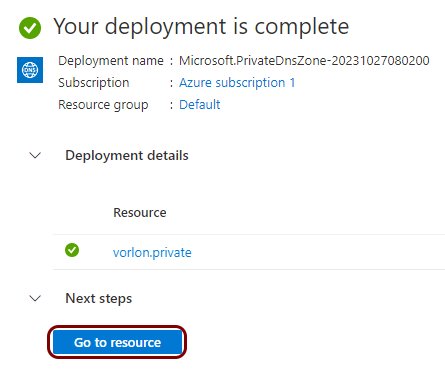
Create a private hosted DNS zone
In this section, you will create a DNS zone for your virtual network, which lets you configure your NAS devices to access the local TACACS+ server using a fully-qualified domain name (FQDN) instead of its IP address.
Every time that you stop and restart your local TACACS+ server container in Azure, it may be assigned a different IP address on the subnet, which means you would have to reconfigure your NAS devices after every restart. Unfortunately, at this time, Azure does not offer any method to maintain a fixed IP address on its virtual private cloud.
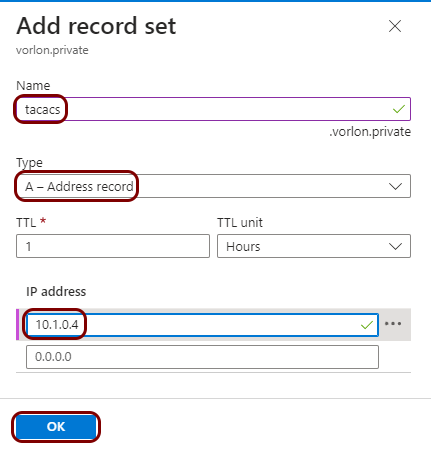
To overcome this problem, you can configure a DNS zone in Azure, assign a private FQDN to the local TACACS+ server, and configure the NAS devices to access this server using this FQDN. This way, if you need to restart the container and get a different IP address, you can just change the IP address in the zone definition instead of having to reconfigure every NAS device.
Result: You can configure your NAS devices in the virtual network to access the local TACACS+ server using its FQDN (in our example, tacacs.vorlon.private) in the virtual network instead of its IP address (in our example, 10.1.0.4). You also need to configure the resolver in the NAS device to use azureprivatedns.net as one of the DNS servers.
If you need to restart the container and the IP address of the local TACACS+ server changes, change the IP address in the record that you created for your hosted zone.