Integrate with Splunk
In this topic, you will learn how to send Portnox™ Cloud alerts to the Splunk Cloud.
Create a HTTP Event Collector in Splunk Cloud
In this section, you will learn how to add a HTTP Event Collector in Splunk Cloud, so that it can receive data via HTTPS from Portnox™ Cloud.
-
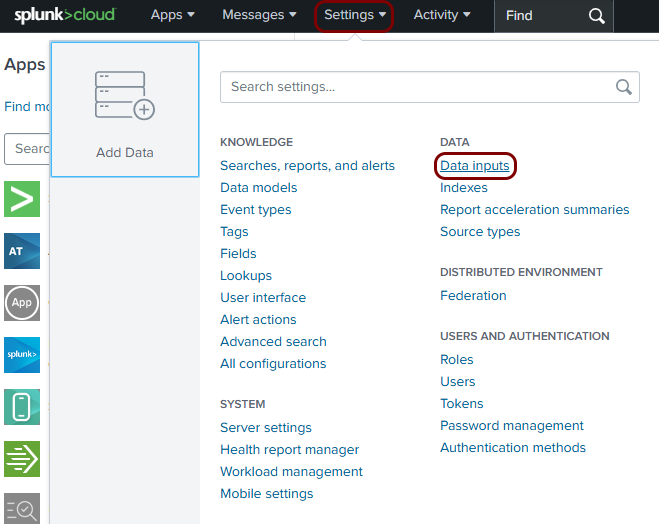
Open your Splunk Cloud dashboard in the browser and select the Settings > DATA > Data inputs option.
-
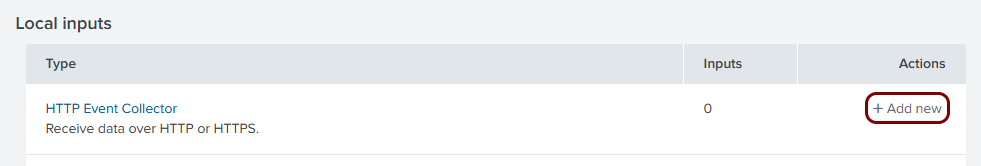
In the Data inputs pane, in the Local inputs table, find the row with
the following Type: HTTP Event Collector, and then click on the
+ Add new link in the Actions column for this row.
-
In the Add Data step, enter a name for the HTTP Event Collector, and then click on the
Next button.

In this example, we used the name Portnox but you can use any name you like.
-
In the Input Settings step of the Add Data wizard, click on the
add all link above the list of available indexes, and then click on the
Review button.

-
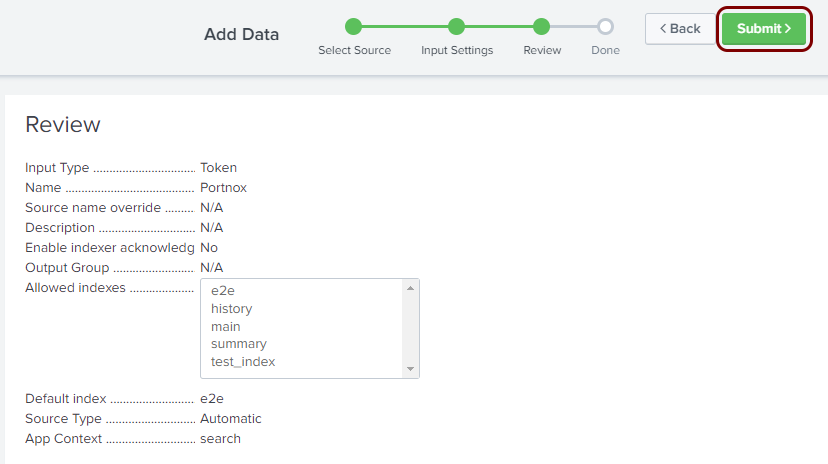
In the Review step of the Add Data wizard, click on the
Submit button.
-
In the Done step of the Add Data wizard, click on the Token
Value field to highlight it, and then copy the value (for example, using
Ctrl+C on Windows).
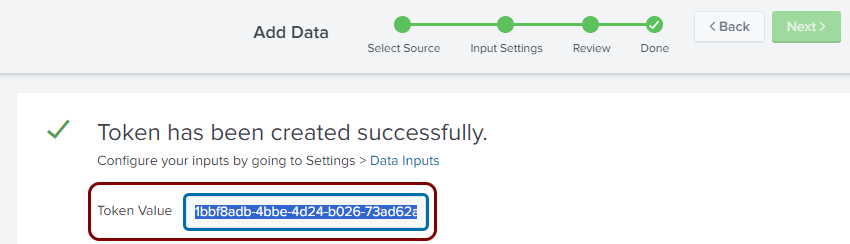
Paste and save the copied value in a text file. You will need this value to configure Portnox Cloud.
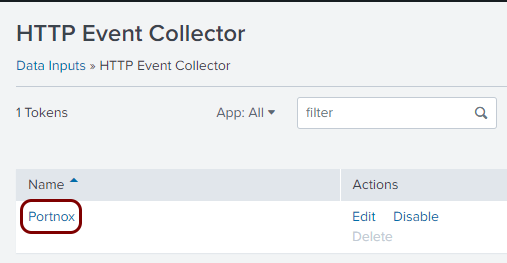
Result: The HTTP Event Collector is active. You can check it here: Settings > Data inputs > HTTP Event Collector.
Configure Portnox Cloud
In this section, you will learn how to configure Portnox™ Cloud to send alert data to the Splunk collector.
-
In the Cloud portal top menu, click on the Settings option.
-
In the Cloud portal left-hand menu, click on the Integration Services > SIEM INTEGRATION SERVICE option.
-
Create a new SIEM integration with Splunk.
-
In the SIEM integration service section, click on the Add new
SIEM link.

The NEW SIEM INTEGRATION section opens.
-
In the Type field, select the Custom option.

-
In the Name field, enter the name for the new integration.

In this example, we used the name Splunk but you can use any name you like.
-
In the Status field, select the Enabled option.

-
In the Protocol type field, select the HTTPS option.

-
In the Endpoint url field, paste the following HTTP source URL depending on whether
you use Splunk Cloud or on-premises Splunk Enterprise:
-
Splunk Cloud:
https://your_instance_name.splunkcloud.com:443/services/collector/event
where your_instance_name is your unique tenant name.
Note:The URL and port may be different if you use, for example, Splunk ES hosted on Google Cloud or AWS. For more information about such cases, consult Splunk documentation. Note that integration is not possible for Splunk Cloud trial accounts because the SSL/TLS certificate served on port 8088, which is required for trial accounts, is signed by an untrusted internal Splunk CA.Important:Previously, the Splunk URL included a prefix http-inputs-, which is still listed in Splunk documentation, but returns a 404 error for new tenants. If you previously configured Splunk but are now facing problems with the integration, try changing the endpoint to not include http-inputs- before the tenant domain name. If that fails, please create a support ticket with Splunk to guide you on the correct collector URL for your tenant/infrastructure. -
Splunk Enterprise (on-premises):
https://your_server:8088/services/collector/eventwhere your_server is your on-premises server.
Note:The standard port is 8088 but you can configure a different port in Splunk: Settings > Data inputs > HTTP Event Collector > Global Settings > HTTP Port Number.Note:By default, Splunk Enterprise uses its own self-signed certificates, which don’t work with Portnox Cloud. To set up a valid certificate in Splunk, consult Splunk documentation. Alternatively, if you’re just testing the integration in a lab environment, you can temporarily turn off SSL support (Settings > Data inputs > HTTP Event Collector > Global Settings > Enable SSL) and use http:// in the URL.Note:If you need to configure the firewall to restrict this access to specific IPs, use the following IP addresses: 23.97.155.157, 52.168.164.222, 20.85.190.232/29, 20.67.6.144/29.
-
-
In the Authentication token field, paste the token that you copied earlier when
setting up the Splunk collector.

-
In the Data format field, select the JSON option.

-
Click on the Save button to add the integration.

- Optional:
Test the configuration by clicking on the Test button.

-
In the SIEM integration service section, click on the Add new
SIEM link.
- Optional:
To configure the types of alerts sent to your SIEM solution, see the following topic: Portnox Cloud alerts.
Note:To learn more about the content and format of alert messages sent to SIEM solutions, see the following topic: Format and content of alert information for SIEM.
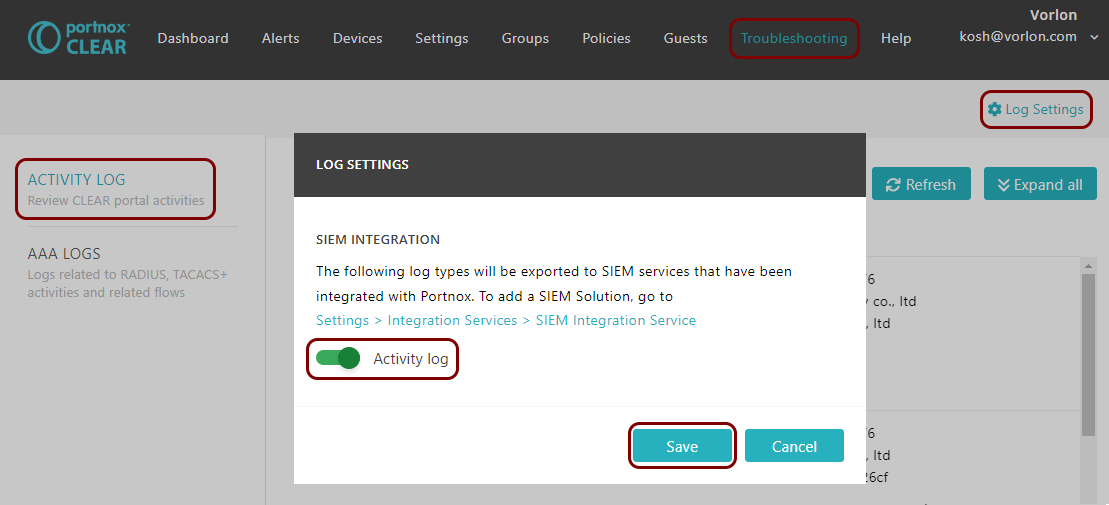
You can also send all of the Portnox Cloud activity log (activities performed by administrators in Portnox Cloud) to your SIEM solution. To do this, go to Troubleshooting > ACTIVITY LOG > Log Settings, activate the Activity log switch, and click on the Save button.
Result: Splunk is receiving alerts from Portnox Cloud.
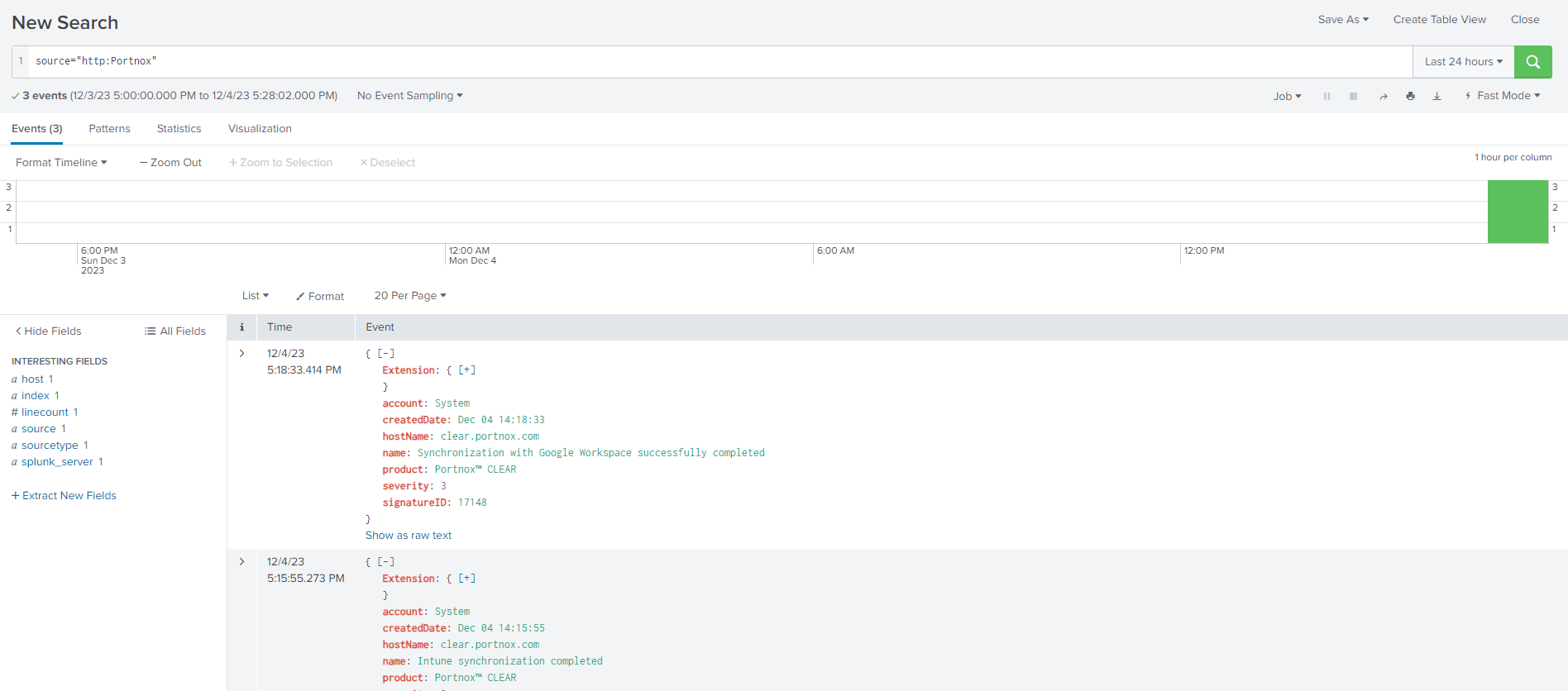
You can confirm the integration, for example, by running a query source="http:collector_name" where collector_name is the name that you used for the HTTP Event Collector.