Wi-Fi employee access – Ubiquiti
In this topic, you will learn how to configure Ubiquiti access points to work together with Portnox™ Cloud and 802.1X RADIUS authentication for Wi-Fi connections.
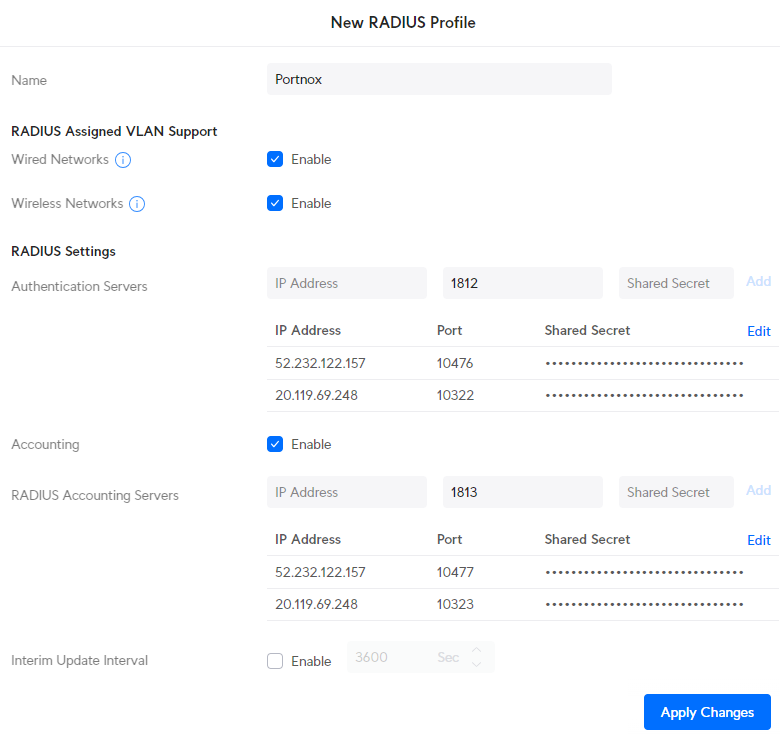
Create a RADIUS profile
In this section, you will create a RADIUS profile for Portnox™ Cloud RADIUS servers. You can then apply this profile to Wi-Fi configurations and Ethernet port profiles.
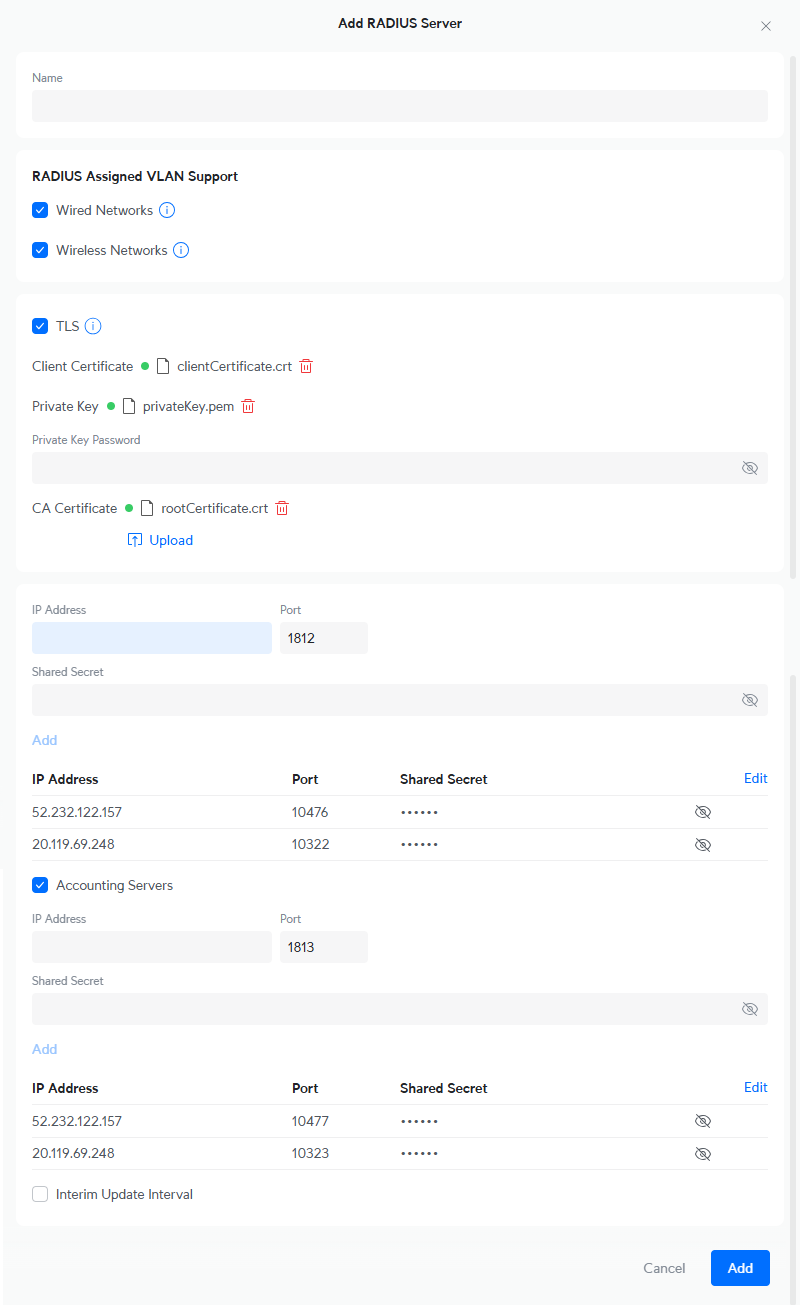
Optional: Create a RadSec profile
This is an optional task that modifies the previous task. Follow this task only if you want to connect to Portnox Cloud RADIUS servers using RadSec. Skip this task if you want to connect to Portnox Cloud RADIUS servers without RadSec.
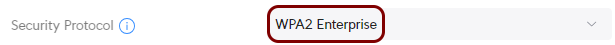
Create a Wi-Fi configuration for the 802.1X network
In this section, you will create a configuration for a Wi-Fi network with WPA2 Enterprise authentication (802.1X) and assign the RADIUS profile to this network.
Result: Your Wi-Fi devices can now access the protected Wi-Fi network, using the Portnox Cloud RADIUS servers for authentication.