Onboard Windows devices with certificates using Microsoft Intune and SCEP
In this topic, you will learn how to deploy Portnox™ Cloud certificates to Windows devices via Microsoft Intune SCEP.
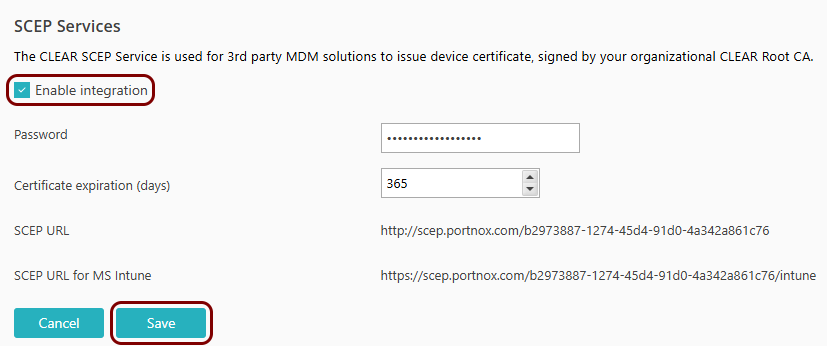
Turn on the Portnox Cloud SCEP services
In this section, you will configure Portnox™ Cloud to provide SCEP services to your devices.
If you have previously turned on the Portnox Cloud SCEP services, skip to the step in which you get the Cloud SCEP URL for Microsoft Intune.
Portnox Cloud SCEP services let devices contact the Cloud SCEP server and get a unique certificate for the device or for the specific user of the device.
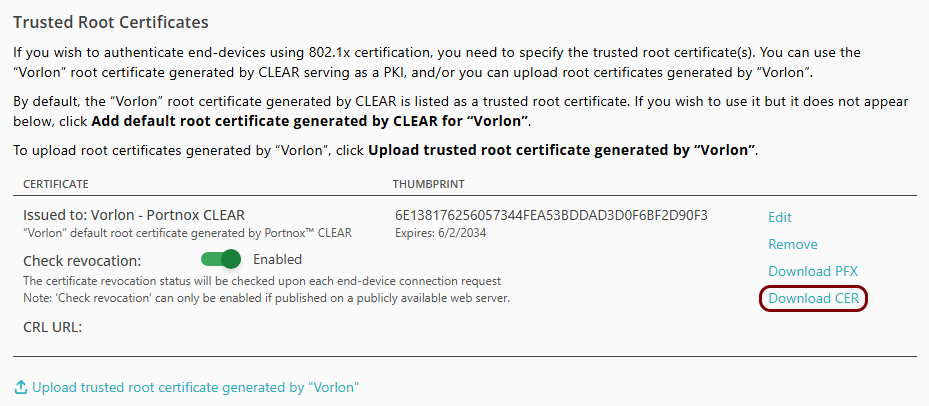
Download the root CA certificate from Portnox Cloud
In this section, you will download the Portnox™ Cloud root CA certificate from the Cloud portal.
You need the root CA certificate so that your managed devices can verify the validity of Cloud RADIUS servers, which have certificates signed by this root CA certificate. If the root CA certificate is not distributed to managed devices, some devices may show a security warning each time that the user connects to networks managed by Portnox Cloud.
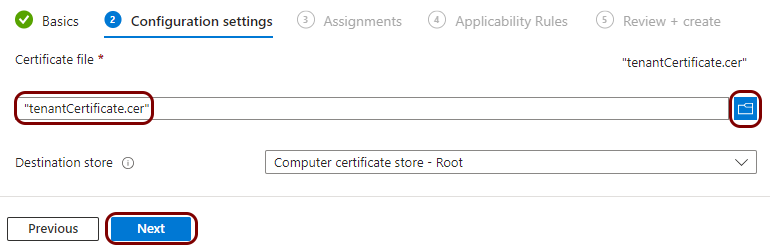
Download the tenant CA certificate from Portnox Cloud
In this section, you will download the Portnox™ Cloud tenant CA certificate from the Cloud portal.
You need the tenant CA certificate from Portnox Cloud so that your managed devices can verify the validity of individual SCEP certificates, which are signed using the tenant CA certificate.
Optional: Hand over information from the Portnox Cloud team to the Intune team
In this section, you will learn what information was collected in previous steps from Portnox Cloud, which is needed to configure Microsoft Intune to work with Portnox Cloud.
If different people are responsible for managing Portnox Cloud and Intune, here is the information you need to hand over:
-
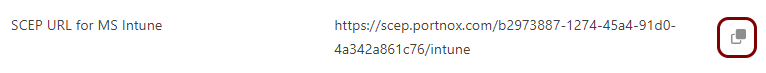
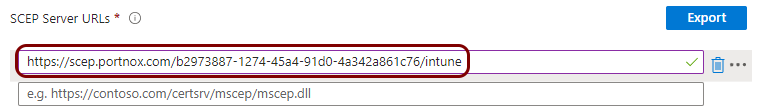
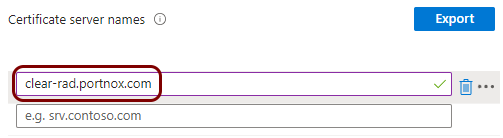
The URL of the Portnox Cloud SCEP server for Intune. For example, https://scep.portnox.com/b2973887-1274-45d4-91d0-4a342a861c76/intune.
-
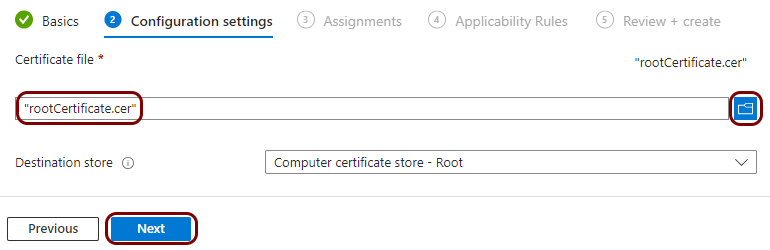
The root CA certificate file in the X.509 format. For example, rootCertificate.cer.
-
The tenant CA certificate file in the X.509 format. For example, tenantCertificate.cer.
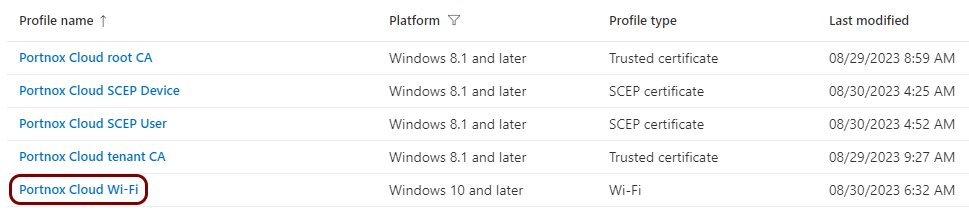
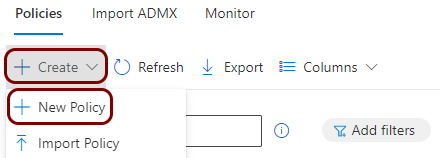
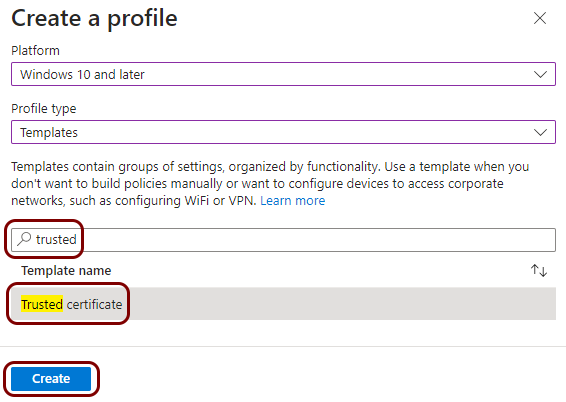
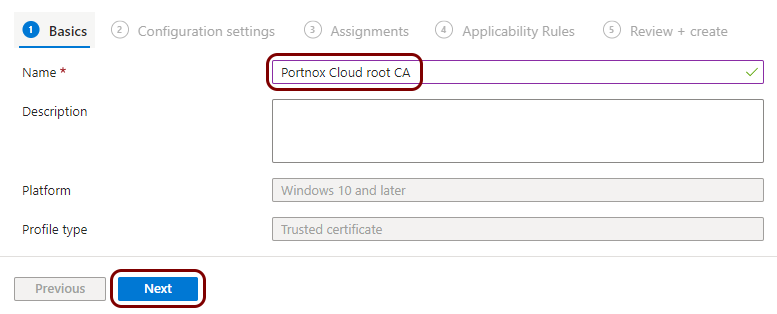
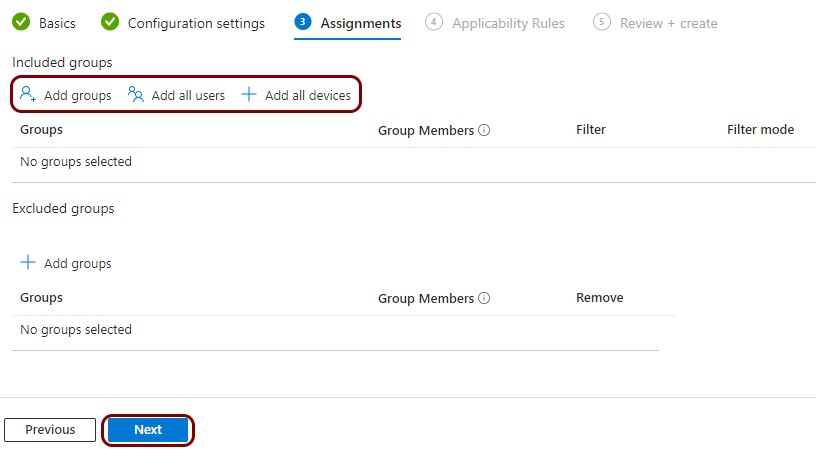
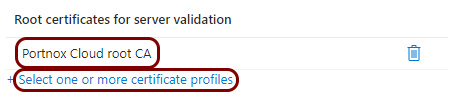
Create a profile for the root CA certificate
In this section, you will create a profile in Microsoft Intune for the downloaded Portnox™ Cloud root CA certificate.
Result: You created a trusted certificate profile for the Portnox Cloud root CA certificate.
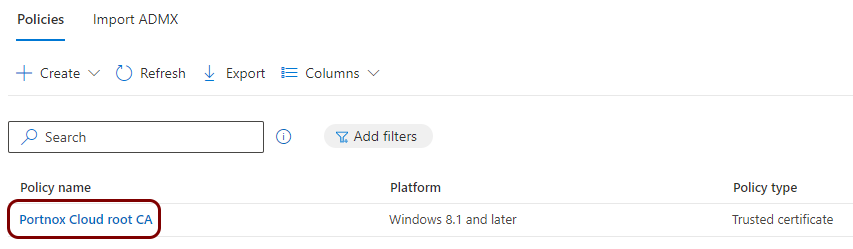
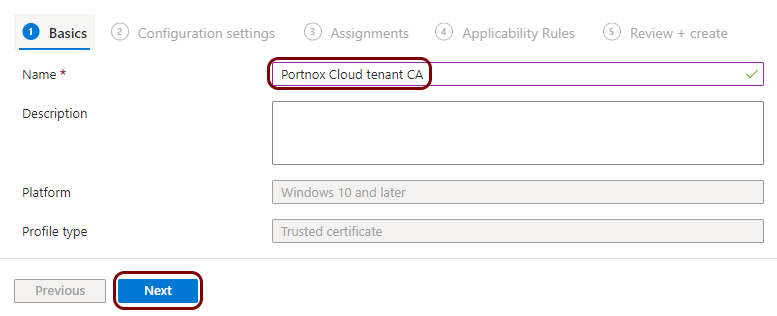
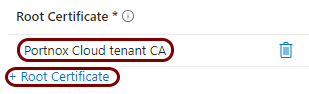
Create a profile for the tenant CA certificate
In this section, you will create a profile in Microsoft Intune for the downloaded Portnox™ Cloud tenant CA certificate.
Result: You created a trusted certificate profile for the Portnox Cloud tenant CA certificate.
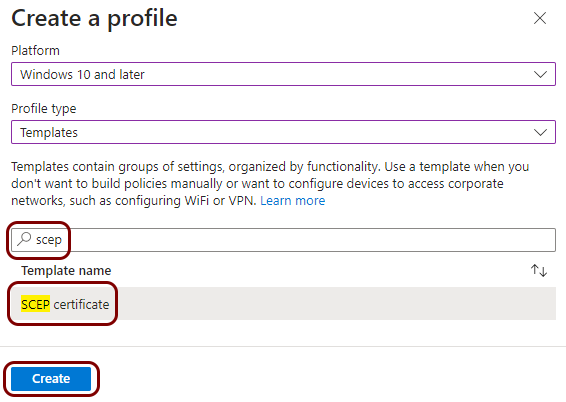
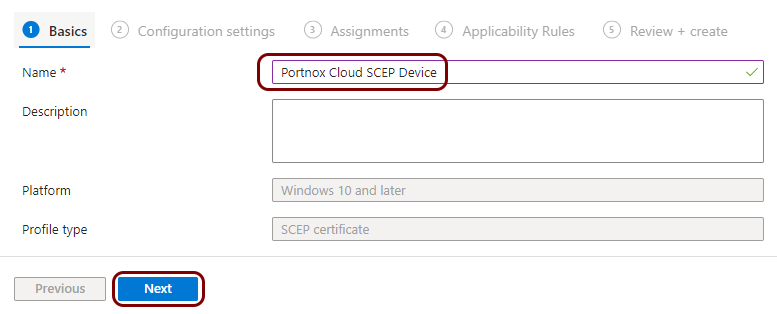
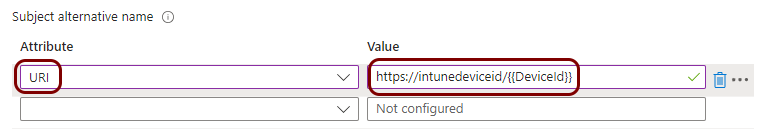
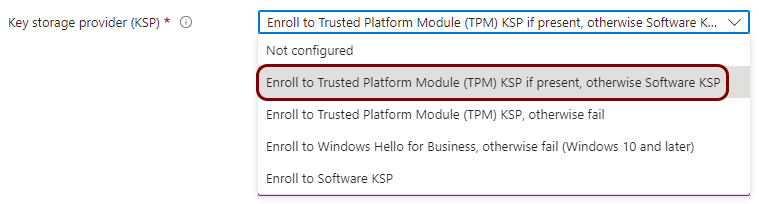
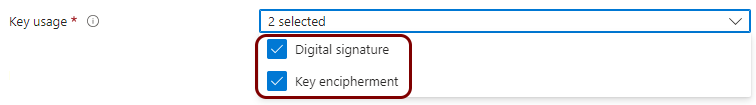
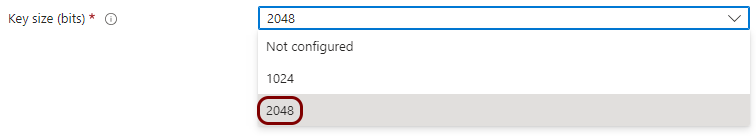
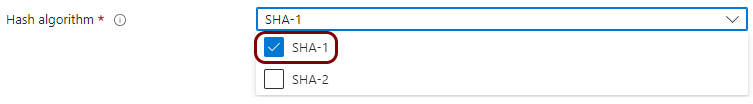
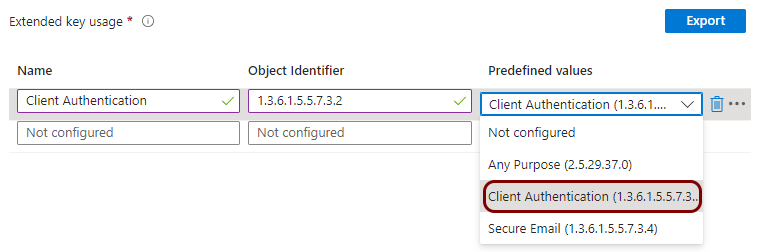
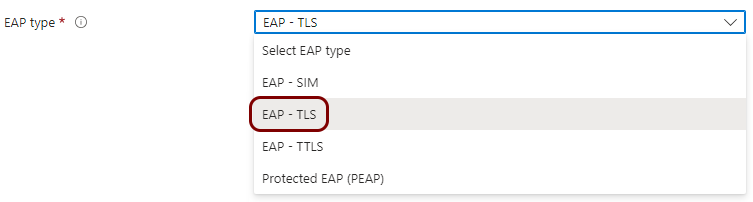
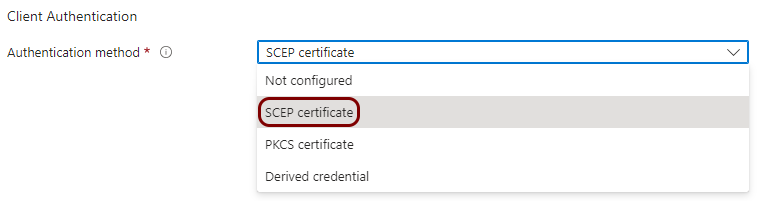
Create a profile for SCEP device certificates
In this section, you will create a profile in Microsoft Intune for unique device certificates, which are generated by Portnox™ Cloud for the devices, and obtained through SCEP requests.
Result: You created a profile for device certificates obtained through SCEP.
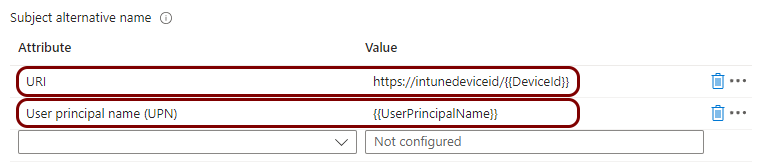
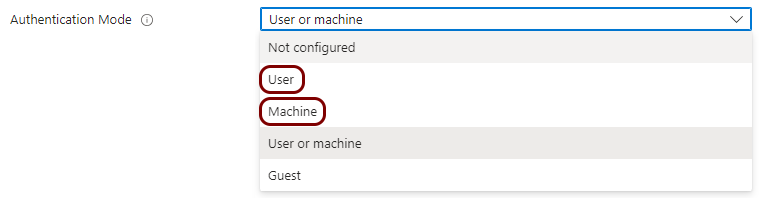
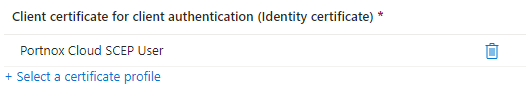
Create a profile for SCEP user certificates
In this section, you will create a profile in Microsoft Intune for unique user certificates, which are generated by Portnox™ Cloud for the users of devices, and obtained through SCEP requests.
Result: You created a profile for user certificates obtained through SCEP.
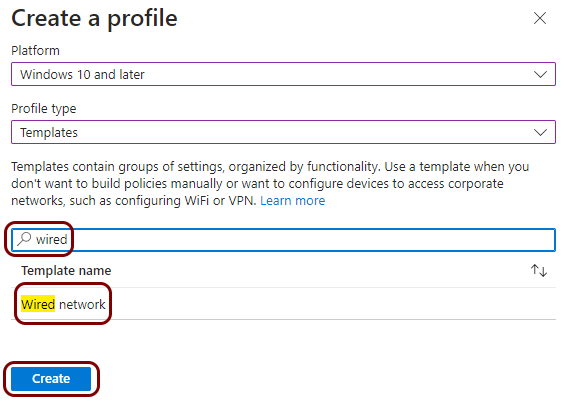
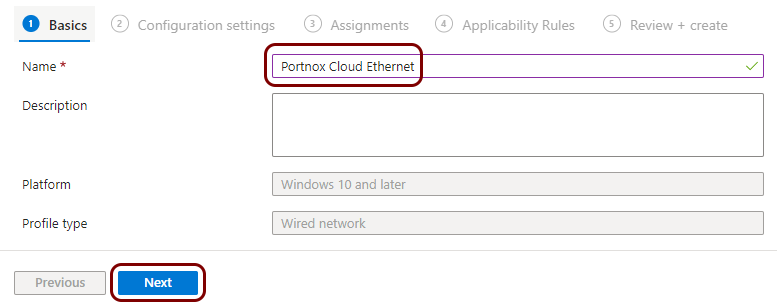
Create a profile for a wired network managed by Portnox Cloud
In this section, you will create a profile in Microsoft Intune for the connection of devices to the Ethernet network managed by Portnox™ Cloud.
Result: You created a profile for Windows devices and the Ethernet network managed by Portnox Cloud.
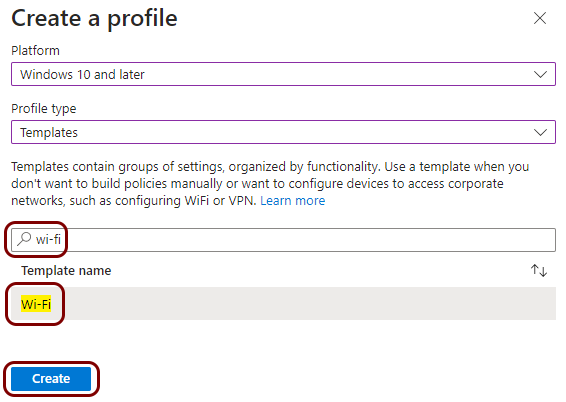
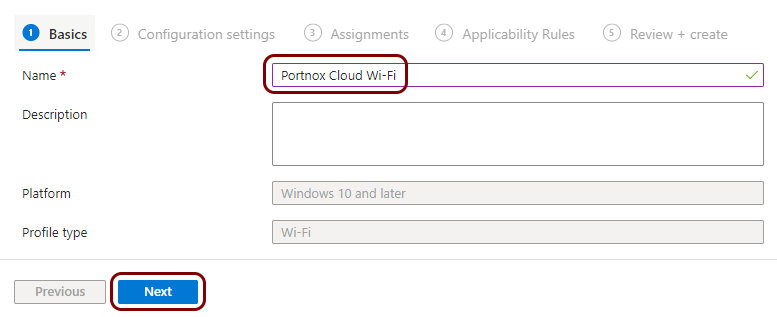
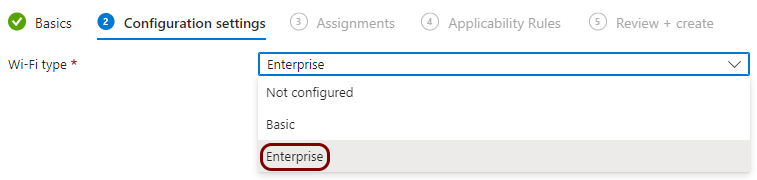
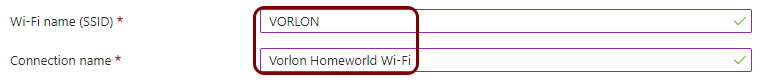
Create a Windows profile for Wi-Fi managed by Portnox Cloud
In this section, you will create a profile in Microsoft Intune for the connection of Windows devices to the Wi-Fi network managed by Portnox™ Cloud.
Result: You created a profile for Windows devices and the Wi-Fi network managed by Portnox Cloud.