Onboard Chromebooks with certificates using Google Workspace and SCEP
In this topic, you will learn how to deploy Portnox™ Cloud certificates via Google Workspace SCEP to manage Chromebook (ChromeOS) devices.
Before you can deploy Portnox Cloud certificates via Google Workspace and SCEP, you must complete the following steps:
-
Prepare a physical or virtual Windows server that can access Portnox Cloud SCEP services (has access to the Internet), where you will install the Google connector.
-
Make sure that the Google administrator account that you will use for this configuration has the Shared Device Settings privileges.
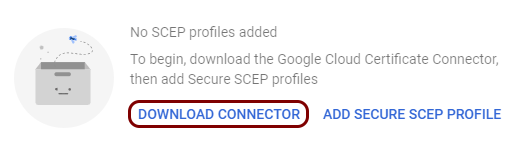
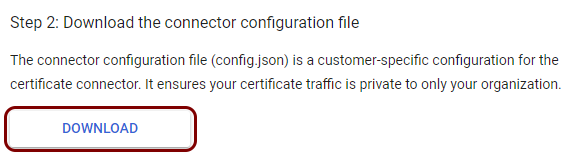
Download and install the Google connector
In this section, you will download and install the Google Cloud Certificate Connector software on a Windows server. Google Workspace needs this connector to connect to the Portnox™ Cloud SCEP server.
When a device managed by Google Workspace needs a certificate to connect to a managed network, the Google Cloud creates a SCEP request for that device. The Google Cloud Certificate Connector, running on a Windows server, polls the Google Cloud for any new requests every 30 seconds. If it finds a new request, the connector contacts the SCEP server, gets the certificate, sends it back to Google Cloud, and then Google Cloud propagates the certificate to the managed device.
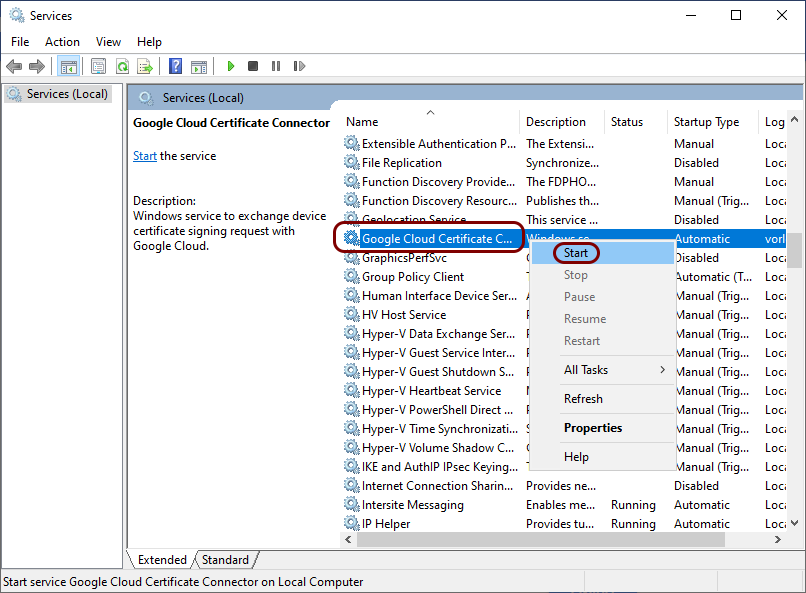
Do the following steps on the Windows server prepared earlier.
Google connector logs are visible in the Event Viewer under .
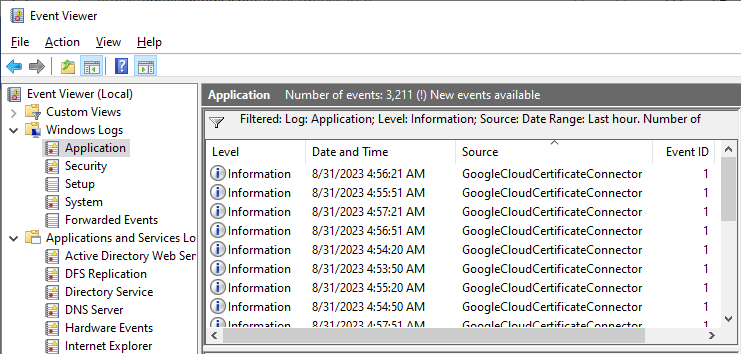
If you need to change the connector configuration, for example, download a new key, place new files in the installation directory and restart the service.
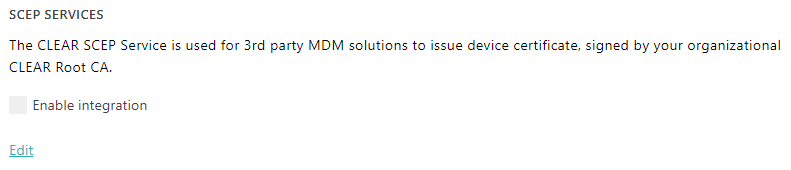
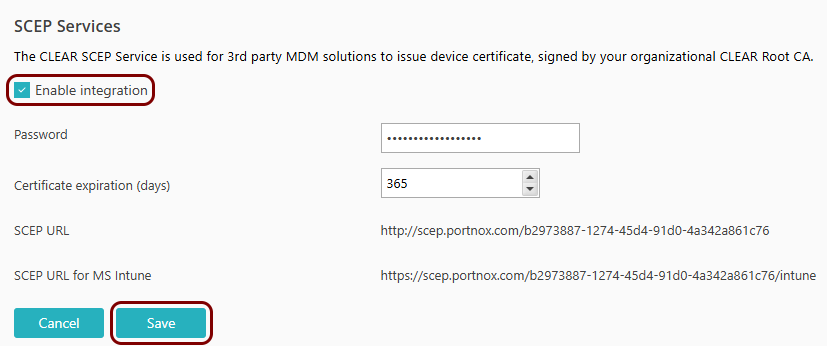
Turn on the Portnox Cloud SCEP services
In this section, you will configure Portnox™ Cloud to provide SCEP services to your devices.
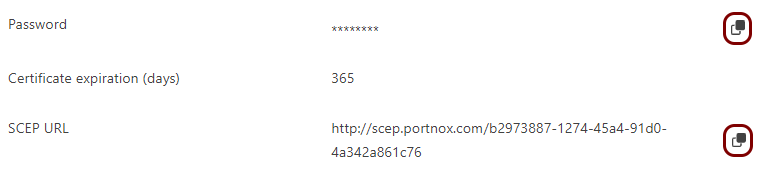
If you have previously turned on the Portnox Cloud SCEP services, skip to the step in which you get the Cloud SCEP URL and password.
Portnox Cloud SCEP services let devices contact the Cloud SCEP server and get a unique certificate for the device or for the specific user of the device.
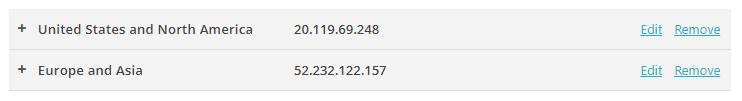
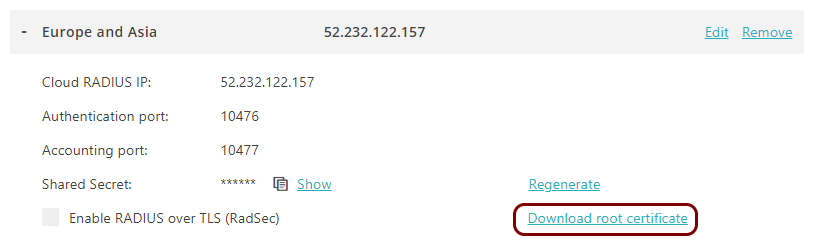
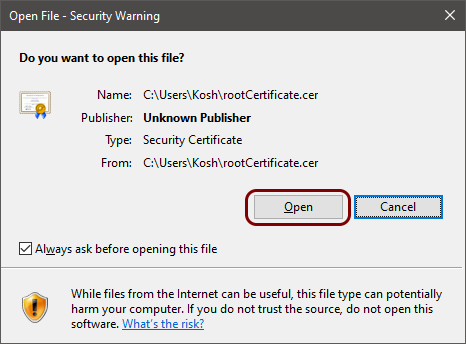
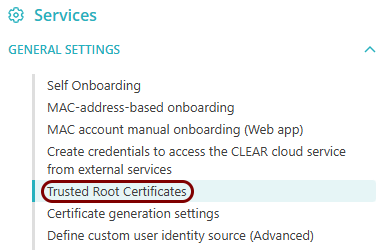
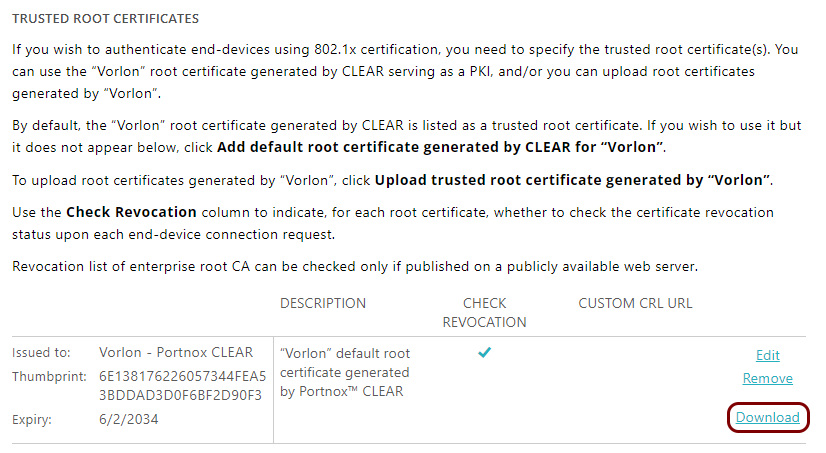
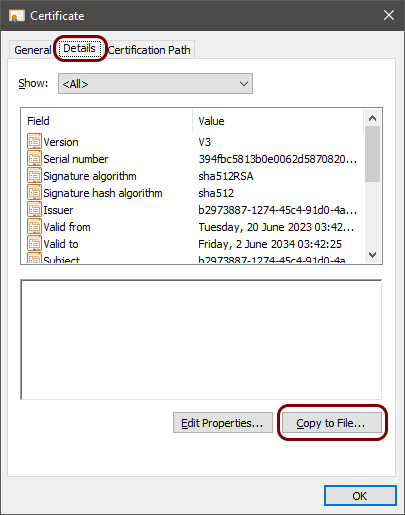
Download the root CA certificate from Portnox Cloud
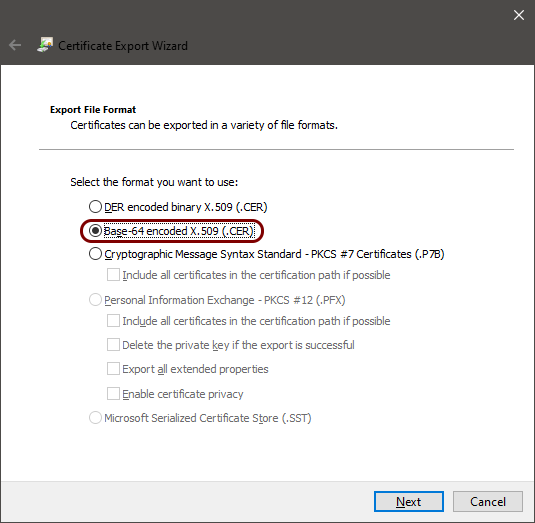
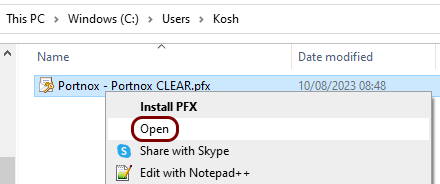
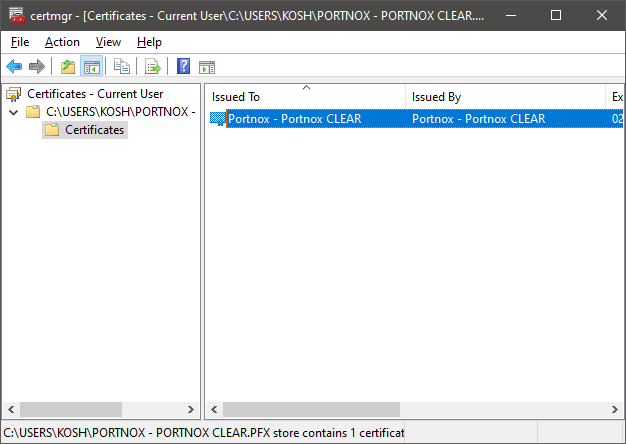
In this section, you will download the Portnox™ Cloud root CA certificate from the Cloud portal and convert it to the Base-64 encoded X.509 format.
You need the root CA certificate so that your managed devices can verify the validity of Cloud RADIUS servers, which have certificates signed by this root CA certificate. If the root CA certificate is not distributed to managed devices, some devices may show a security warning each time that the user connects to networks managed by Portnox Cloud.
Download the tenant CA certificate from Portnox Cloud
In this section, you will download the Portnox™ Cloud tenant CA certificate from the Cloud portal and convert it to the Base-64 encoded X.509 format.
You need the tenant CA certificate from Portnox Cloud so that your managed devices can verify the validity of individual SCEP certificates, which are signed using the tenant CA certificate.
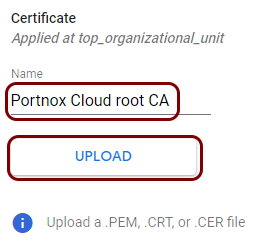
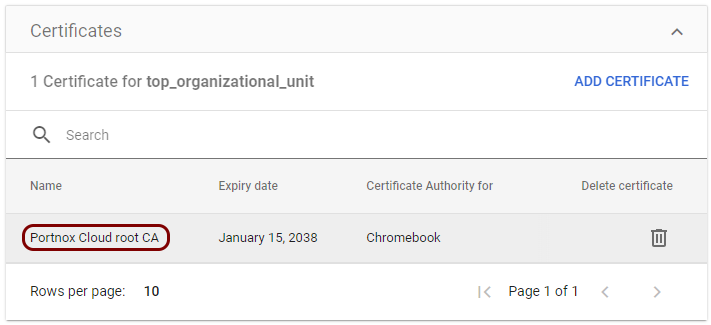
Create a profile for the root CA certificate
In this section, you will create a profile in Google Workspace for the downloaded Portnox™ Cloud root CA certificate.
Result: You created a profile for the Portnox Cloud root CA certificate.
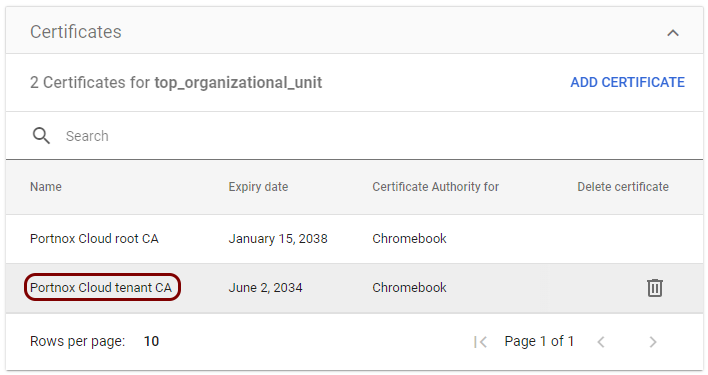
Create a profile for the tenant CA certificate
In this section, you will create a profile in Google Workspace for the downloaded Portnox™ Cloud tenant CA certificate.
Result: You created a profile for the Portnox Cloud tenant CA certificate.
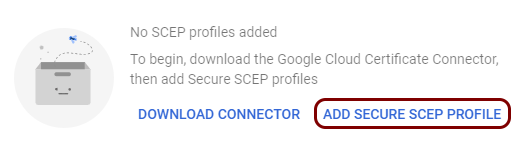
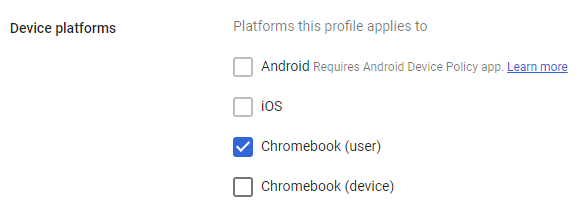
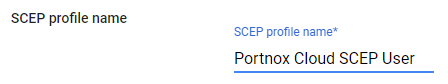
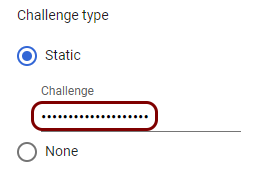
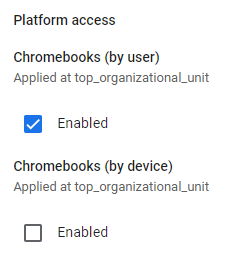
Create a secure SCEP profile
In this section, you will create a secure SCEP profile in Google Workspace. The secure SCEP profile lets devices managed by Google Workspace contact the Portnox™ Cloud SCEP server via the connector.
Result: You created a trusted SCEP profile.

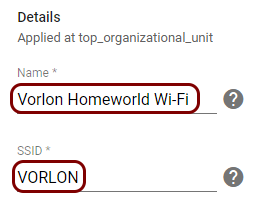
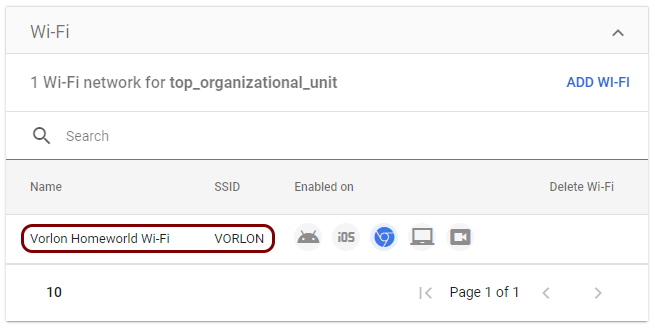
Create a Wi-Fi profile
In this section, you will create a Wi-Fi profile in Google Workspace for Chromebooks managed by Portnox™ Cloud.
Result: You created a Wi-Fi profile for the network managed by Portnox Cloud.
Test your configuration on a managed Chromebook
In this section, you will test the configuration you created in Google Workspace by connecting a Chromebook to the network managed by Portnox™ Cloud.