Onboard macOS devices with certificates using Addigy and SCEP
In this topic, you will learn how to deploy Portnox™ Cloud SCEP certificates via Addigy, SCEP, and iMazing Profile Editor to manage macOS devices.
Addigy lets you create simple profiles using the cloud user interface but does not let you create profiles with many payloads, which you need to connect to Portnox Cloud using SCEP. However, you can distribute custom profiles using Addigy, so you can create a custom profile and then use Addigy for management.
This topic shows you how to create a custom Apple profile for user-based authentication to connect to Portnox Cloud via Wi-Fi and Ethernet. We recommend that you use a free app called iMazing Profile Editor, but you can create a custom profile using a different tool or edit it manually in XML, if you prefer.
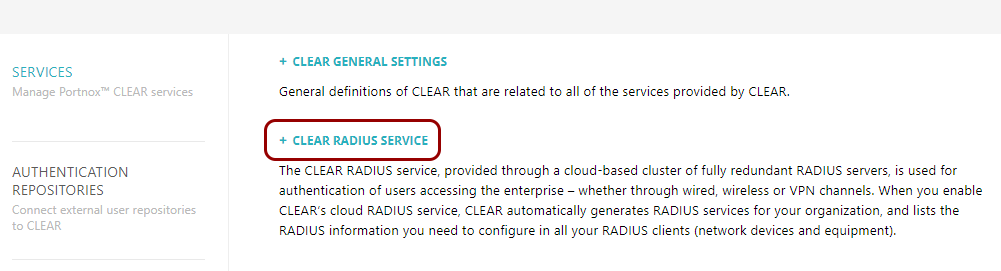
Turn on the Portnox Cloud SCEP services
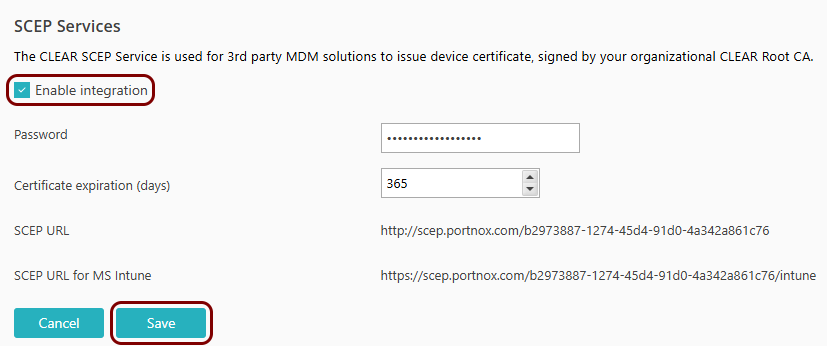
In this section, you will configure Portnox™ Cloud to provide SCEP services to your devices.
If you have previously turned on the Portnox Cloud SCEP services, skip to the later step in which you get the Cloud SCEP URL and password.
Portnox Cloud SCEP services let devices contact the Cloud SCEP server and get a unique certificate for the device or for the specific user of the device.
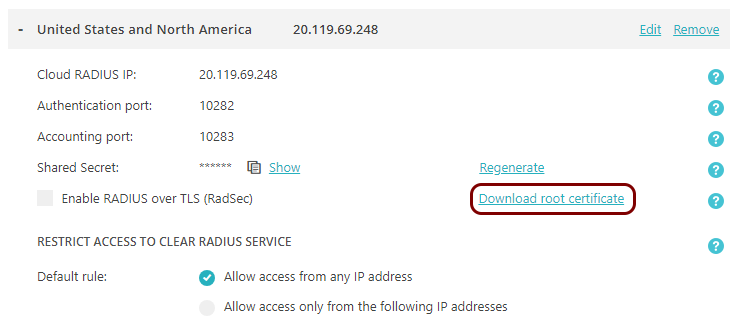
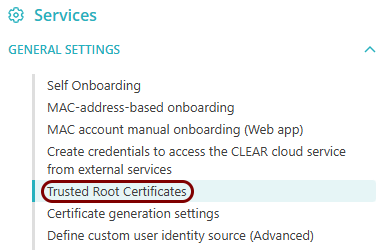
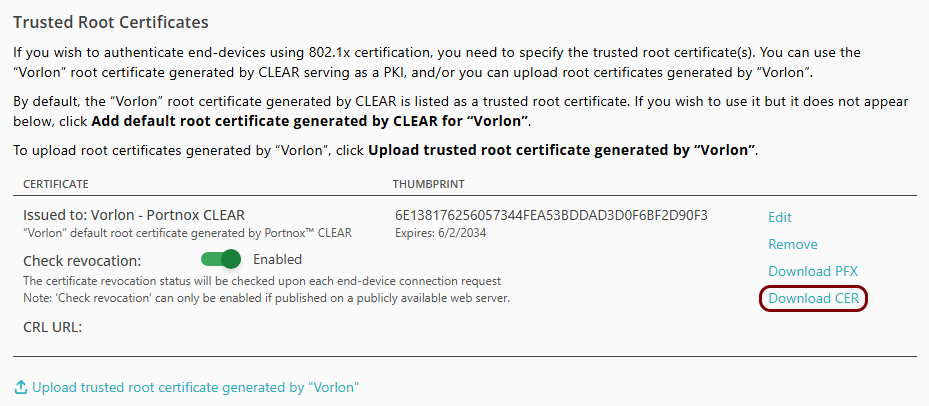
Download the root CA certificate
In this section, you will download the root CA certificate from Portnox™ Cloud, which is needed to create a profile.
Result: The root CA certificate file is in the Downloads folder on the local disk.
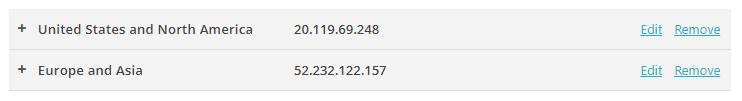
Download the tenant CA certificate
In this section, you will download the Portnox™ Cloud tenant CA certificate from the Cloud portal.
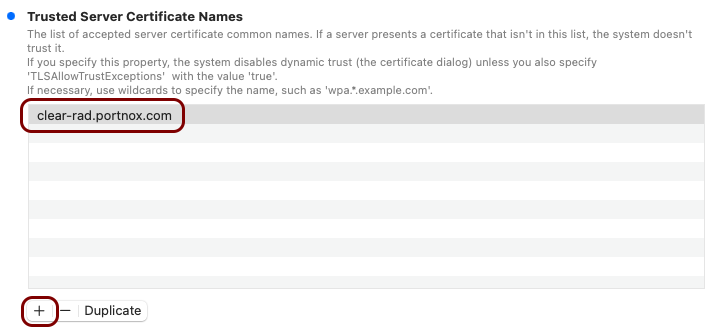
You need the tenant CA certificate from Portnox Cloud so that your managed devices can verify the validity of individual SCEP certificates, which are signed using the tenant CA certificate.
Optional: Hand over information from the Portnox Cloud team to the Addigy team
In this section, you will learn what information was collected in previous steps from Portnox Cloud, which is needed to configure Addigy to work with Portnox Cloud.
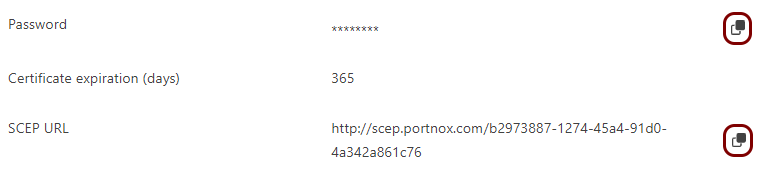
If different people are responsible for managing Portnox Cloud and Addigy, here is the information you need to hand over:
-
The URL of the Portnox Cloud SCEP server. For example, https://scep.portnox.com/b2973887-1274-45d4-91d0-4a342a861c76.
-
The password for the SCEP server.
-
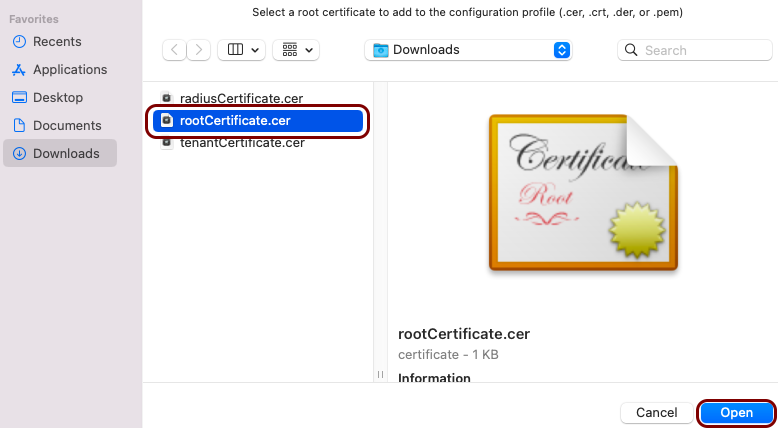
The root CA certificate file in the X.509 format. For example, rootCertificate.cer.
-
The tenant CA certificate file in the X.509 format. For example, tenantCertificate.cer.
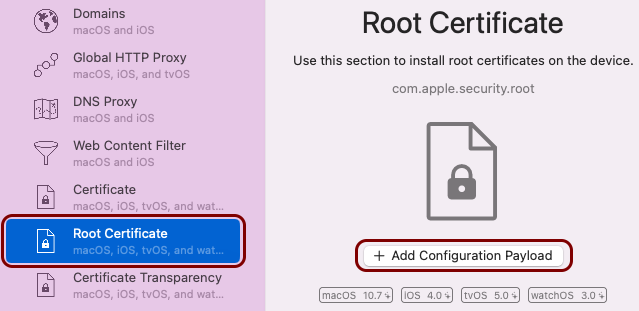
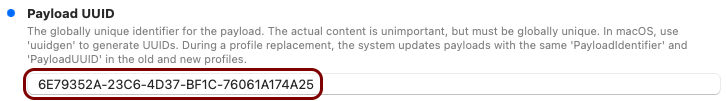
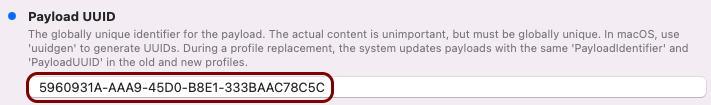
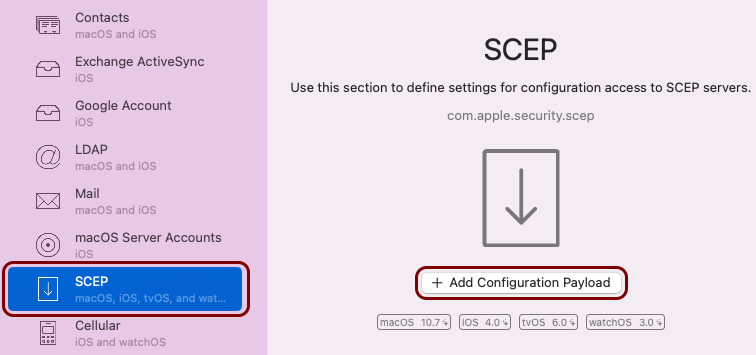
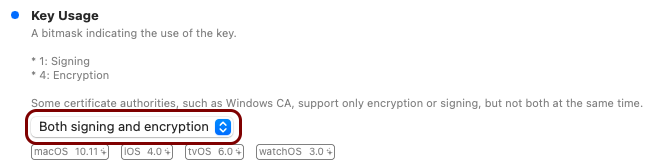
Create the custom profile
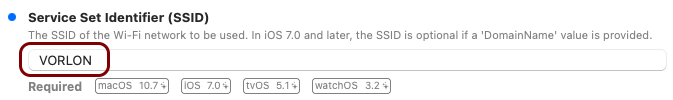
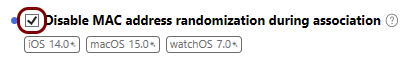
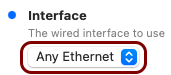
In this section, you will use the iMazing Profile Editor to create an Apple profile for use in Addigy, which contains the following payloads: the root CA certificate, the tenant CA certificate, the SCEP configuration for user-based authentication, the Wi-Fi configuration, and the Global Ethernet configuration.
Result: The custom profile file (.mobileconfig) is saved on the disk and ready for use in Addigy.
Add the custom profile to Addigy
In this section, you will upload the custom profile file to Addigy and assign it to an existing policy, so that Addigy can distribute it to managed devices.