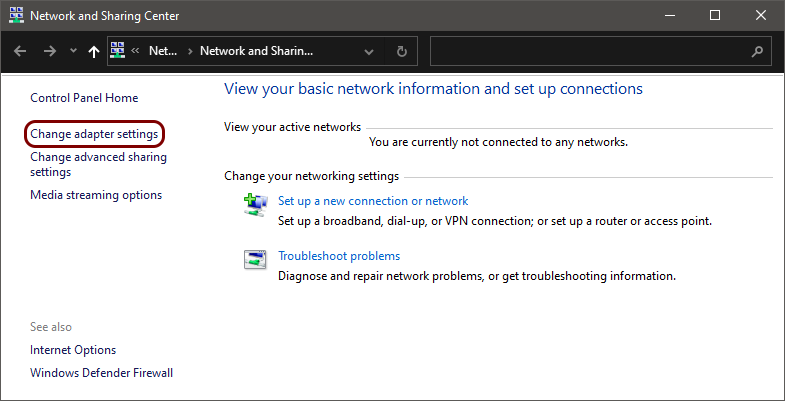
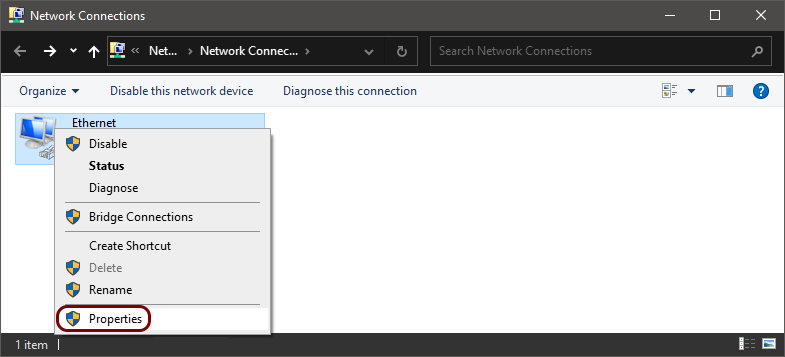
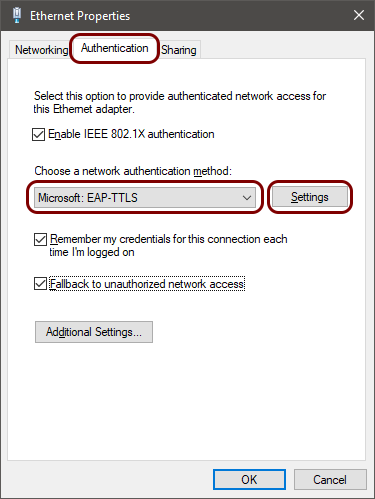
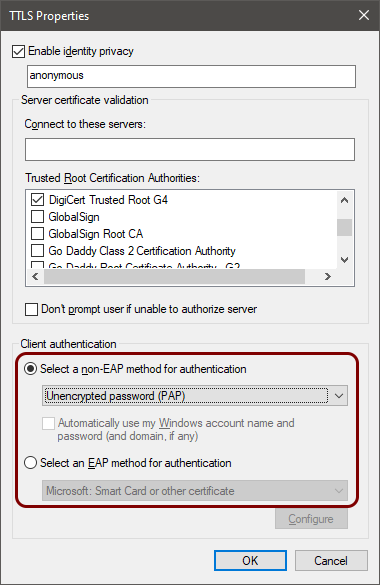
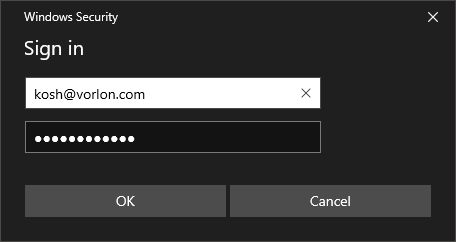
Onboard a Windows device to a wired network with credentials
In this topic, you will learn how to onboard using credentials, a Windows 10 computer, and a wired network managed by Portnox™ Cloud.
Note:
The user interface and the names of options may differ slightly for other Windows versions.
Note:
If your instance is integrated with Microsoft Entra ID
and your Entra ID access policy enforces multi-factor authentication (MFA), to log in using credentials you need to set up a
MFA bypass by following the steps in this topic: Bypass multi-factor authentication in Entra ID.
Result: Your Windows 10 computer is connected to a wired network managed by Portnox Cloud.
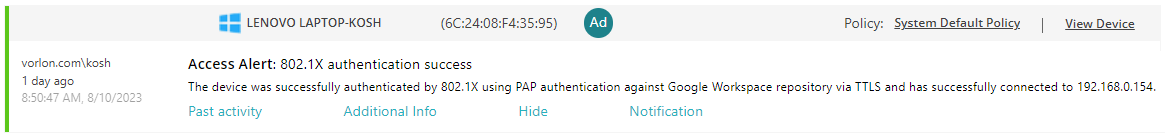
Troubleshooting information: See the following topic: How to troubleshoot typical device onboarding issues.